We’re happy to present to you the new version of the Profiler with the following news:
– introduced Lua filters: lua/custom and lua/loop
– added optional condition to misc/basic
– added JavaScript execute action
– added JavaScript debugger
– simplified save report/project logic
– included actions among the extensions views
– improved detection of shellcodes
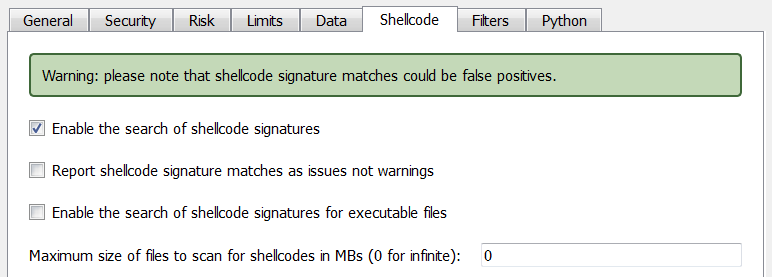
– introduced max file size option for shellcode detection
– improved OLE Streams parsing and extraction from RTFs
– exposed getHash method in ScanProvider to Python
– added text replace functionality to text controls
While most of the items in the list have been discussed in previous posts, some of them need a brief introduction.
Max file size for shellcode detection
While shellcode detection applies by default to files of any size, you might want to specify a threshold.
This is useful if you want to speed up the analysis of large files. It might come handy in some cases.
The ‘getHash’ method
This method should be used by hooks to retrieve a hash for the currently scanned file. The syntax is very simple:
sp.getHash("md5")
Of course one could use a filter to hash the file, but the advantage of this method is that once a particular hash type has been computed it won’t be computed again if requested by another hook.
Improved OLE Streams parsing and extraction from RTFs
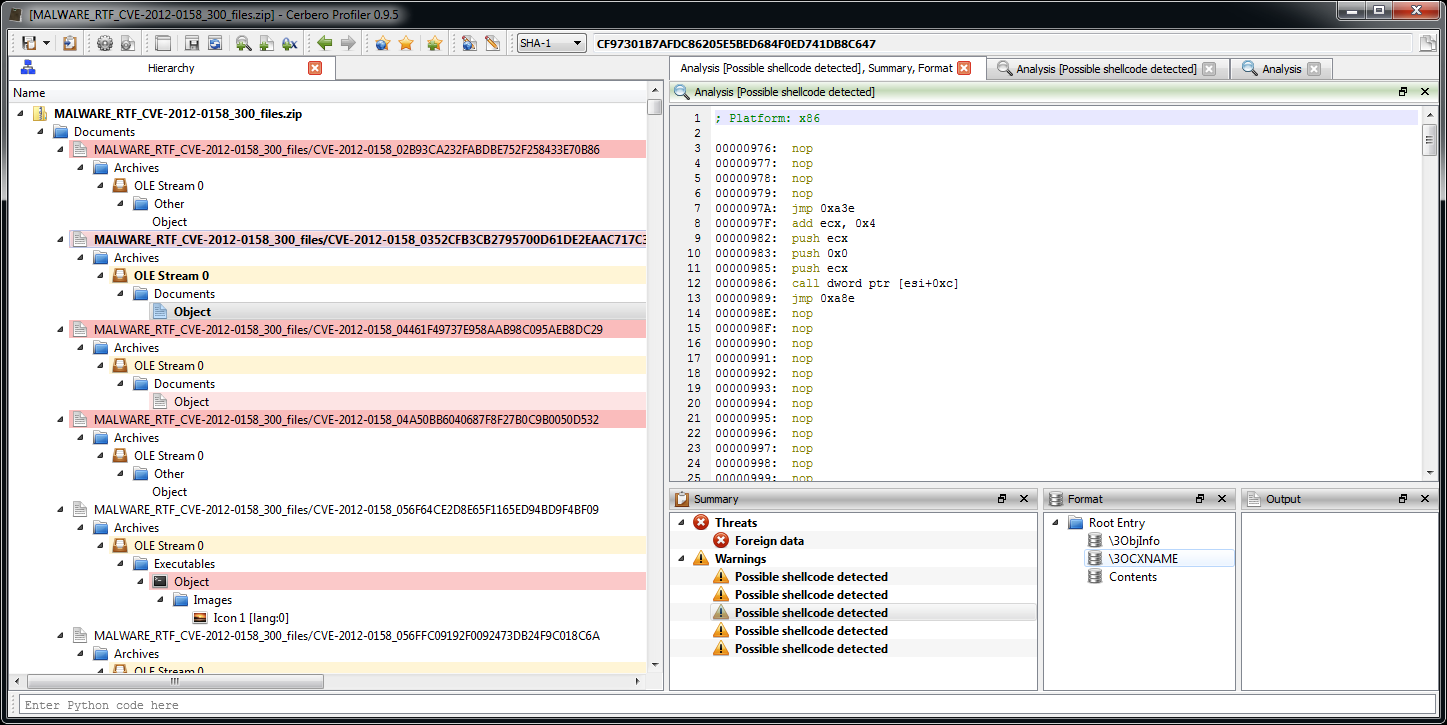
In one of the previous use cases we’ve analyzed a huge set of malicious RTF documents. Some of them were not recognized correctly and some of them showed problems in the automatic extraction of OLE streams. This release fixes these issues.
As you can see all RTFs are now correctly parsed and their OLE stream has been extracted. Some of the OLE objects though are not extracted correctly. After looking into it, it seems to be a problem with the malicious files themselves. OLE streams are encoded as hex strings into the RTF and in some of these files there’s an extra byte which invalidates the sequence.
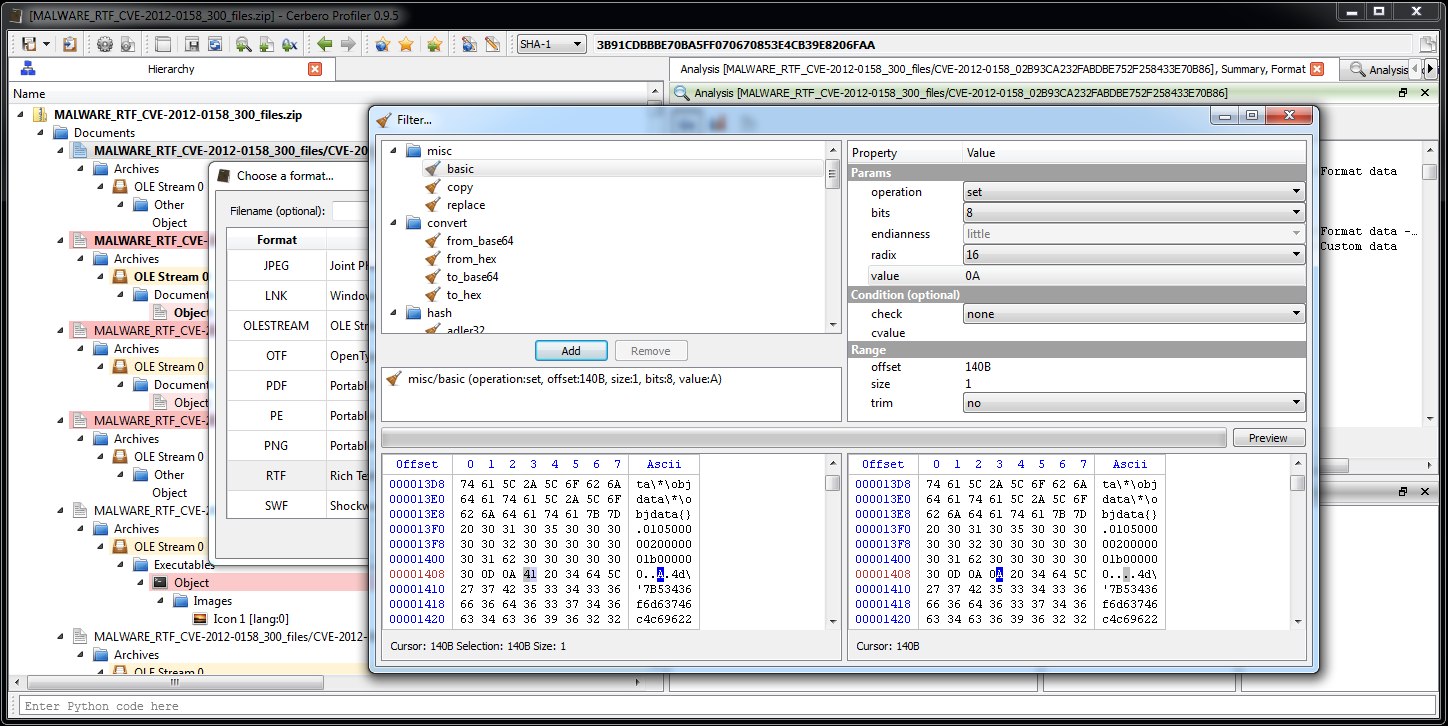
01 05 00 00 02 00 00 00 1B 00 00 00 A 4D
That ‘A’ character between 00 and 4D makes the sequence to be 00 A4 D which is incorrect. Our guess is that the malware generator which produced these RTFs outputted some invalid ones by inserting an ‘A’ character instead of a 0x0A newline.
While RTF readers are not able to parse these objects either it’s still interesting for our analysis to be able to inspect them. So we just load the RTF files patching the ‘A’ character with a filter as in the screenshot below.
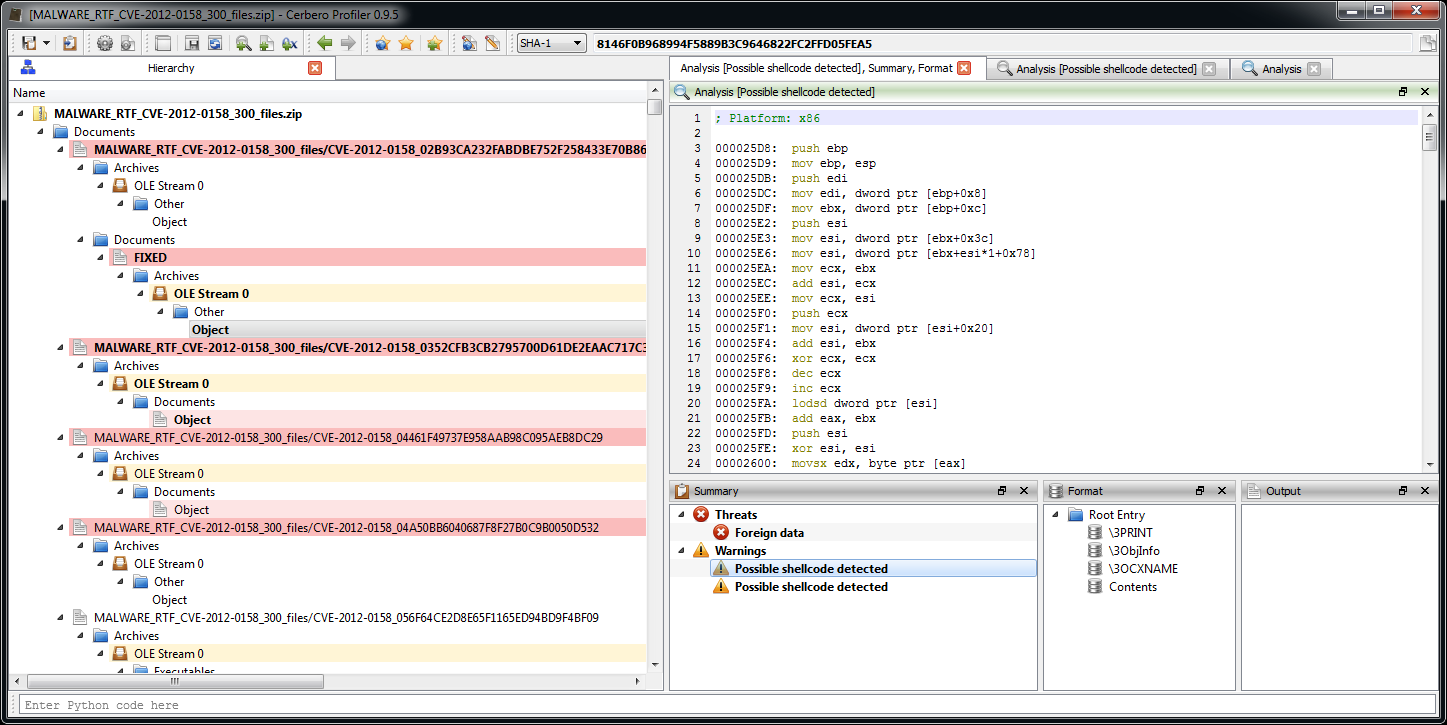
That fixes it and we are now able to inspect the embedded OLE object and its threats. As you can see we get directly the shellcode disassembly from the automatic analysis.
Enjoy!
Hello,
Realy… I like this tool!
Can you update (only add some features) the DEMO release, I now that is DEMO and not object of any update.
Regards
Hello STRELiTZIA,
glad you like the tool!
What features would you like to see in the demo version? Unfortunately, it’s often difficult to add features to it because they are dependent on other features which rely on yet other features and so on. But we’re interested in suggestions for the demo, so do not hesitate to suggest improvements. 🙂
Cheers
Daniel
It is a little hard to enumerate needed features 🙂 but it would be nice to support pdf/exe files and embedded objects can be inspected.
I hope they has not a lot of dependencies on other features to add support for pdf/exe for DEMO release.
BTW, if you have a beta teste project for external users, I can add my candidature to test your product.
Regards
While there are no plans to include PE/PDF inspection into the demo version for the moment, who knows maybe in the future… 🙂
We’re not currently running any beta test project, the product has already been used in production for a year and as far as we know is very stable.
Thanks nonetheless for the offer.
Cheers
Daniel
Thank you very much for your answers.
Regards