This script concatenates strings such as “a” + “b”:
from Pro.UI import *
import re
ctx = proContext()
v = ctx.getCurrentView()
if v.isValid() and v.hasSelection():
s = v.getSelectedText().replace('" &', '" +')
s = eval(s)
v.setSelectedText('"' + s + '"')
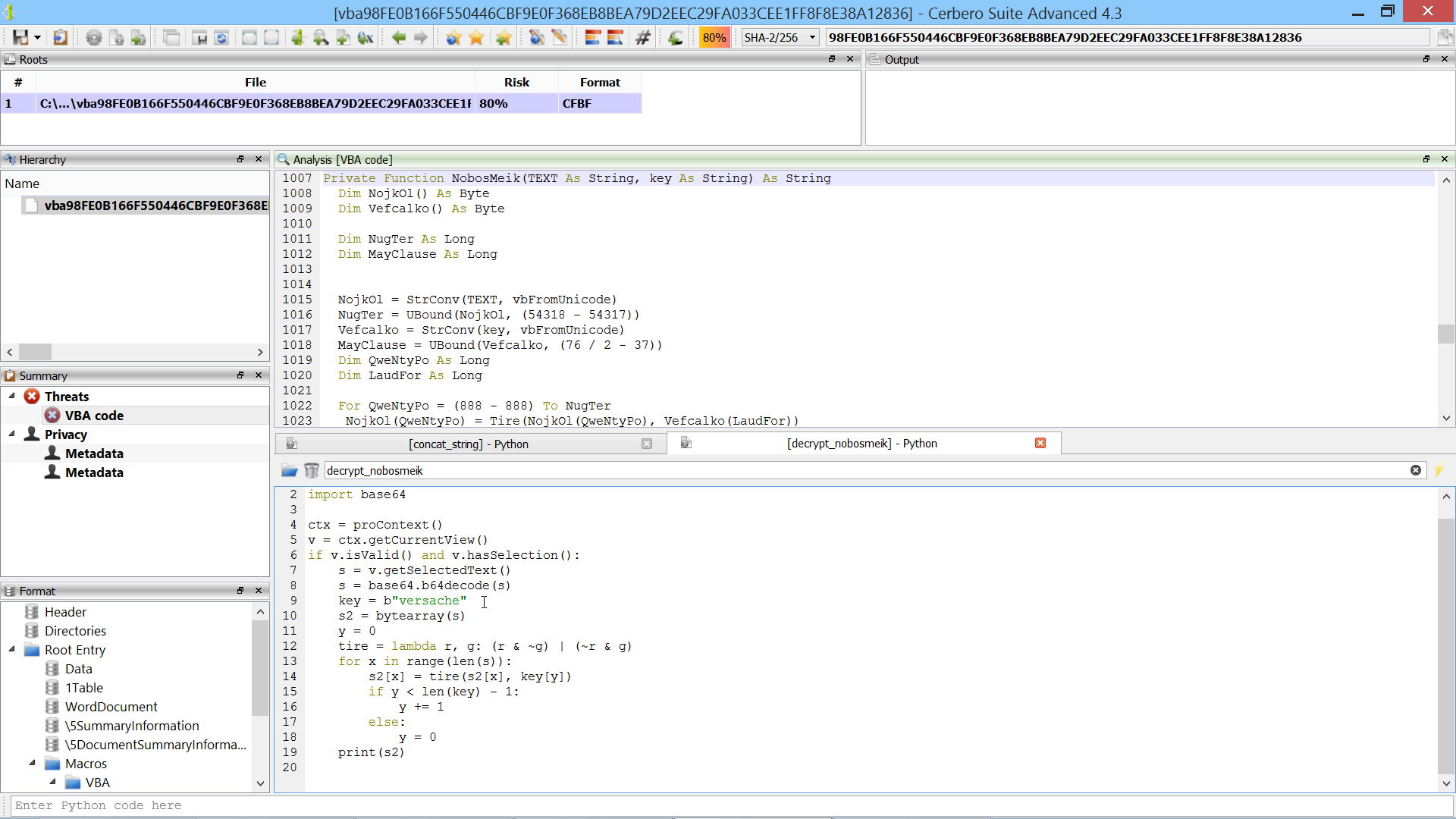
This second script decrypts strings the same way as the “NobosMeik” function:
from Pro.UI import *
import base64
ctx = proContext()
v = ctx.getCurrentView()
if v.isValid() and v.hasSelection():
s = v.getSelectedText()
s = base64.b64decode(s)
key = b"versache"
s2 = bytearray(s)
y = 0
tire = lambda r, g: (r & ~g) | (~r & g)
for x in range(len(s)):
s2[x] = tire(s2[x], key[y])
if y < len(key) - 1:
y += 1
else:
y = 0
print(s2)