We released the XST Format package, which adds support for Microsoft Outlook PST and OST email data formats.
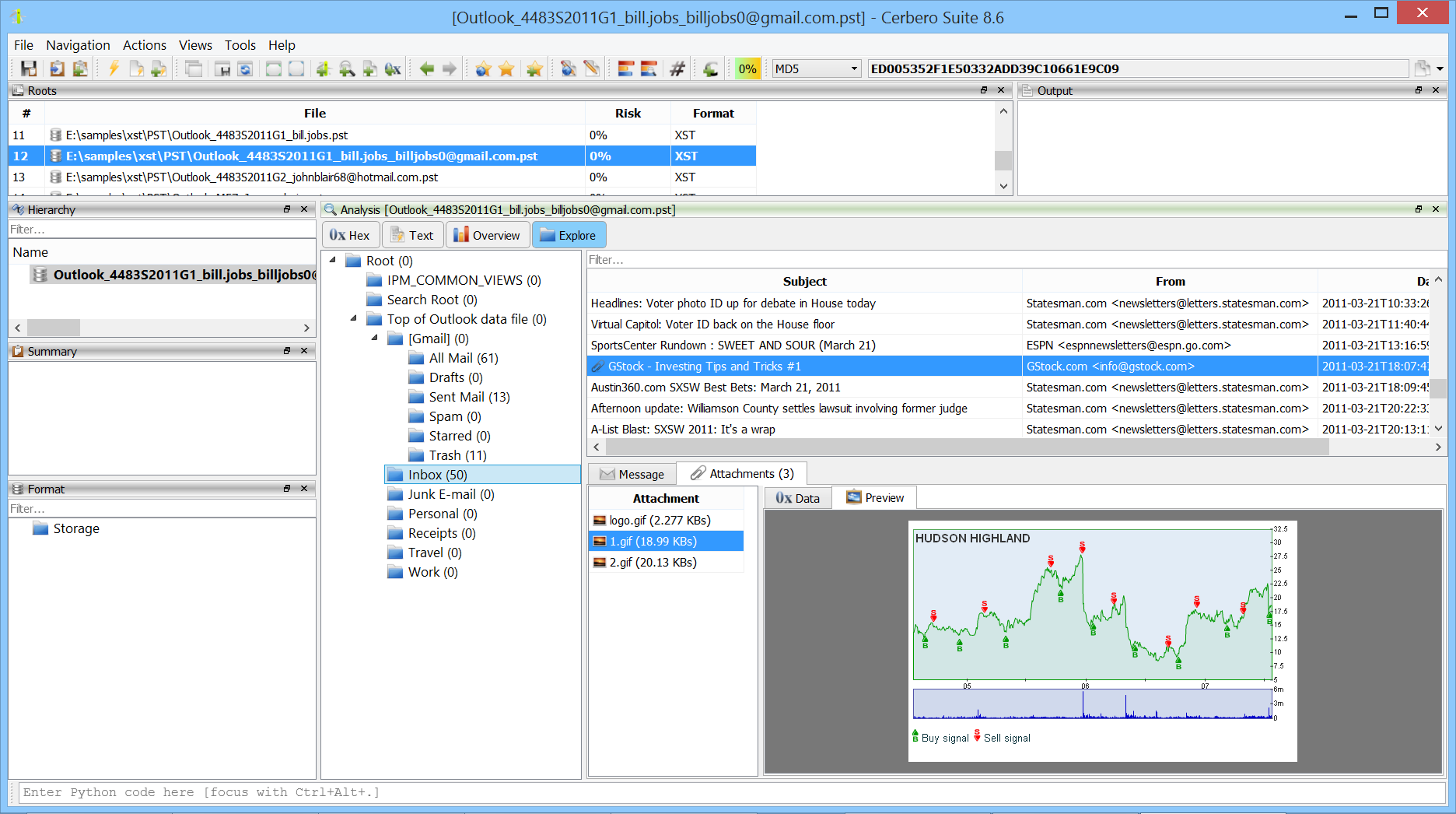
The package makes it possible to explore every part of an email container, including messages, folder structures, metadata and attachments.
We released the XST Format package, which adds support for Microsoft Outlook PST and OST email data formats.

The package makes it possible to explore every part of an email container, including messages, folder structures, metadata and attachments.
The upcoming 2.7 version of Profiler Advanced introduces support for the EML file format.
Support for EML files had until now only been present as experimental hook to extract attachments. We have now introduced full-fledged EML support and have removed the previous experimental code.
It’s possible to preview the email messages:
Inspect their file format:
And, as expected, inspect their attachments:
The image above shows JavaScript contained in a PDF inside a Zip archive attachment, while the image below shows ActionScript3 byte code of a SWF contained in a PDF inside a Zip archive attached to an email.
Enjoy!
Even though sending malware via zipped attachments in spam emails is nothing new and had been around for eons but many people are still puzzled at how it works. Thus, I will go through with you on how to do it with Profiler. I will try to fill in required information about where to look out for information and how decode some of the information.
Firstly, we are going to learn how are a bit about the .msg file format and how is it used to store a message object in a .msg file, which then can be shared between clients or message stores that use the file system.
From an investigator’s point of view, you should always analyze the .msg file without installing Outlook. In order to analyze the .msg file without Outlook, we can read more about the file format from:
The purpose of this post is to give a better technical understanding of how attackers makes use spam emails to spread malware.
[ Sample used in the analysis ]
MD5: BC1DF9947B9CF27B2A826E3B68C897B4
SHA256: C7AC39F8240268099EC49A3A4FF76174A50F1906BBB40AE6F88425AF303A44BB
Sample: Sample
[ Part 1 : Getting Started ]
For those who want to follow along, this is a link to the .msg file. Do note, this is a MALICIOUS file, so please do the analysis in a “safe” environment. The password to the attachment is “infected29A”
Now, let’s start getting our hands dirty…and open the suspicious .msg file.
The msg file is already flagged by Profiler, as it contains some suspicious features.
Each “__substg” contains valuable pieces of information. The first four of the eight digits at the end tells you what kind of information it is (Property). The last four digits tells you the type (binary, ascii, Unicode, etc)
[ Part 2 : Email investigation ]
If we are interested in email investigation, let’s check out the following file, “__substg1.0_0C1F001F”.
As we can see below, the sender’s email address is “QuinnMuriel64997@haarboutique-np.nl”
But is it really sent from Netherlands?
Well, let’s check out the message header located in “__substg1.0_007D001F” to verify that.
If we were to do through the message header, do a whois on “haarboutique-np.nl” and check out the MX server. We can confirm that the sender is spoofing email as well.
From the message header, we can conclude that the sender sent the email from “115.78.135.85” as shown in the image and the extracted message header as shown below.
Whois information showed that IP address where this spam email is sent from is from Vietnam.
But it doesn’t mean that the attacker is from Vietnam. Anyone in the world can buy web hosting services in Vietnam. This is just to let you know that the attacker is definitely not sending from “haarboutique-np.nl”
[ Part 3 : Email investigation ]
Using this information opening the “__substg1.0_0E1D001F” file and we can see the subject, “Re:“
Hmmmm…this doesn’t look any useful at all. Let’s try opening the file, “__substg1.0_1000001F”, containing the “subject body” instead.
Please find attached document you requested. The attached file is your account balance and transactions history.
Regards,
Muriel Quinn”
Awesome, Muriel Quinn is sending me my account balance and transactions history which I may or may not have requested at all. Awesome, he is also attaching the files to the email just for me. This is definitely suspicious to me.
[ Part 4 : Email attachment ]
Now that we are interested in the attachments, let’s look at “Root Entry/__attach_version1.0_#00000000” and refer to the specifications again.
If we were to look at “__substg1.0_3704001F”, we will see that the filename of the attachment is called “transa~1.zip” and the display name “__substg1.0_3001001F” of the attachment is called “transactions-625.zip”.
Now let’s look at the actual data located within “__substg1.0_37010102” as shown below.
Now, let’s press “Ctrl+A” to select the entire contents. Then copy it into a new file as shown in the image below.
But as we can see on the left, Profiler can identify what is inside the attachment. There are 3 Javascript files inside the .zip file.
Now let’s fire up “New Text View” and copy the contents of “transactions 774219.js” as shown below.
Press “Ctrl+R” and select “Beautify JavaScript” and Profiler will “JSBeautify” it for you. But let’s add some “Colouring” to it by doing “Right-click -> Language -> JavaScript” as shown below.
We can use Profiler to debug the JavaScript but I shall leave that as an exercise for the readers.
The decoded JavaScript will look something like this.
As we can see from the image above, it is downloading from “http://infograffo[.]com[.]br/lkdd9ikfds” and saving it as “ew3FbUdAB.exe” in the victims’ TEMP directory.
We won’t be going through on reversing the malware.
In the meantime, we hope you enjoyed reading this and would be happy to receive your feedback!
The upcoming 0.9.9 version of the Profiler includes some very useful SDK additions. Among these, the addEmbeddedObject method (to add embedded objects) and a new hook notification called ‘scanning’. The scanning notification should be used for long operations and/or to add embedded objects. In this post we’ll demonstrate these new features with a little script to detect attachments in EML files.
One of the advantages of using the Profiler is that we are be able to inspect the sub-files of the attachments as well. The screenshot above shows a PNG contained in an ODT attachment. Nice, isn’t it?
But the nicest part is how little code is necessary to extend the functionality of the Profiler. These are the lines to add to the user hook configuration file:
[EML: detect attachments]
file = eml.py
scanning = detectEmlAttachments And this is the Python code:
from Pro.Core import INVALID_STREAM_OFFSET
def detectEmlAttachmentsCb(offset, npattern, sp):
c = sp.getObjectStream()
# hdr range
m = c.findFirst("\n--".encode("ascii"), 0, offset, False)
hdrstart = 0 if m.offset == INVALID_STREAM_OFFSET else m.offset
m = c.findFirst("\r\n\r\n".encode("ascii"), offset)
hdrend = c.size() if m.offset == INVALID_STREAM_OFFSET else m.offset
# make sure it's an attachment
m = c.findFirst("Content-Disposition: attachment".encode("ascii") , hdrstart, hdrend - hdrstart)
if m.offset == INVALID_STREAM_OFFSET:
return 0
# data range
datastart = hdrend + 4
m = c.findFirst("\r\n\r\n".encode("ascii"), datastart)
dataend = c.size() if m.offset == INVALID_STREAM_OFFSET else m.offset
# retrieve file name (if any)
name = "no_name"
m = c.findFirst('name='.encode("ascii"), hdrstart, hdrend - hdrstart)
if m.offset != INVALID_STREAM_OFFSET:
namestart = m.offset + 5
namedel = "\r\n"
if c.read(namestart, 1) == '"'.encode("ascii"):
namedel = '"'
namestart = namestart + 1
m = c.findFirst(namedel.encode("ascii"), namestart)
if m.offset != INVALID_STREAM_OFFSET:
namesize = min(m.offset - namestart, 200)
name = c.read(namestart, namesize).decode("utf-8")
# add attachment
sp.addEmbeddedObject(datastart, dataend - datastart, "?", name, " That’s it. Of course, this is just a demonstration, to improve it we could add support for more encodings apart from ‘base64’ like ‘Quoted-Printable’ for instance.
Some email programs like Thunderbird store EML files by appending them in one single file. In fact, as you can see, the screenshot above displays the attachments of an entire Inbox database. 😉
Also notice that in the code the addEmbeddedObject method is called by specifying a base64 decode filter to load the file. We can, of course, specify multiple filters and Lua ones as well. This makes it extremely easy to load files without having to write code to decode/decrypt/decompress them. The “?” parameter leaves the Profiler to identify the format of the attachment.