It is always nice to give something back to the community and although this is unfortunately not always possible, we’re happy to announce the release of PE Insider, a free PE viewer which shares the same codebase for inspection as Cerbero Profiler and hence supports the entire PE specification and is incredibly fast and stable. We’re always very busy, but I was finally convinced by Ange Albertini to create this utility. 😉
The utility clearly stands light-years away in terms of functionality compared to the Profiler, but it does have some things which go beyond the simple format inspection including MSIL disassembly, navigation, ranges and resource preview.
Of course there’s room for improvement, but in the meantime here’s a first version. Enjoy!
P.S. To keep up-to-date with news regarding this utility either subscribe to our twitter account or follow the blog.
Hello,
Just to say BIG thanks.
Regards
Thanks STRELiTZIA 🙂
This is awesome 🙂
Hello,
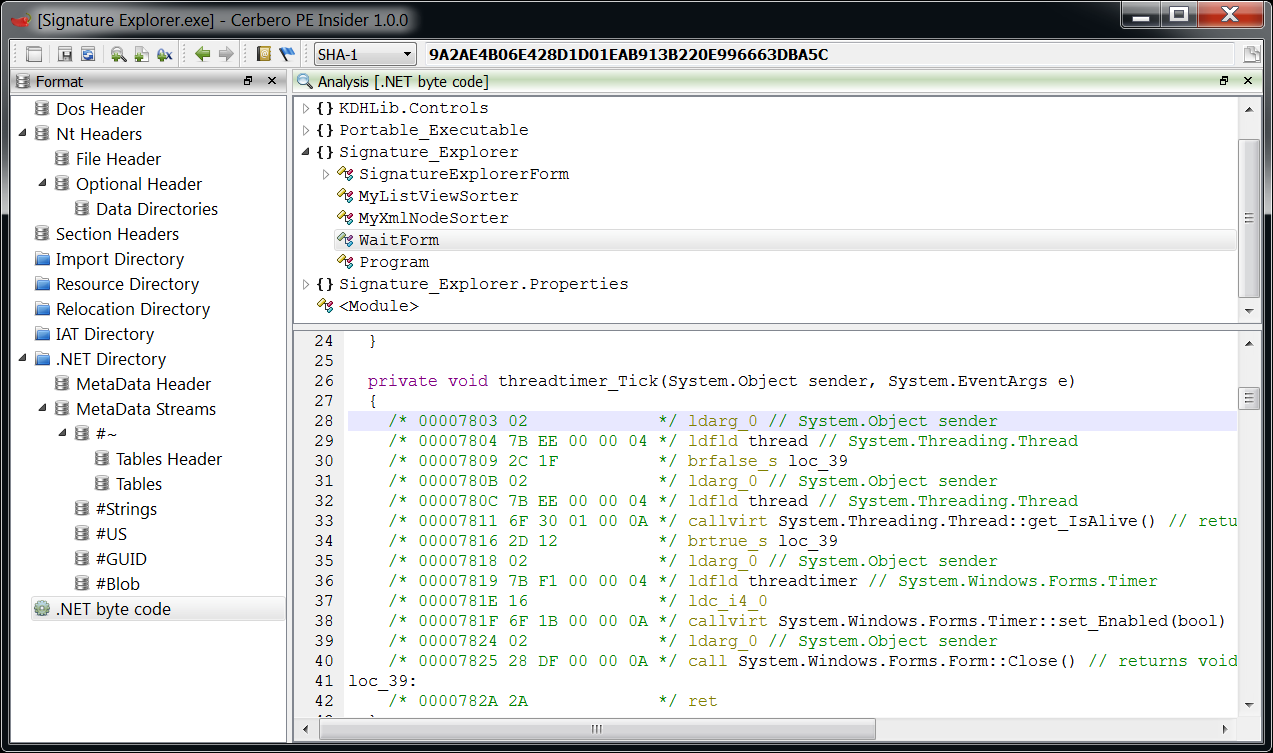
PEI crash when I analyze an malware sample.
Scenario:
Goto “.Net byte code” then “Expand all” select “Out”
NET Framework Verifier log (Windows XP SP3 X86):
[08/13/13,10:44:17] Install state for .NET Framework 1.0: not installed.
[08/13/13,10:44:17] Install state for .NET Framework 1.1: not installed.
[08/13/13,10:44:17] Install state for .NET Framework 2.0: installed with service pack 2.
[08/13/13,10:44:17] Install state for .NET Framework 3.0: installed with service pack 2.
[08/13/13,10:44:17] Install state for .NET Framework 3.5: installed with service pack 1.
[08/13/13,10:44:17] Install state for .NET Framework 4 Client: installed with no service packs.
[08/13/13,10:44:17] Install state for .NET Framework 4 Full: installed with no service packs.
[08/13/13,10:44:17] Install state for .NET Framework 4.5: not installed.
The malware sample link: “Dead Space 2 Keygen.exe”
hxxp://www.kernelmode.info/forum/viewtopic.php?f=16&t=643&p=4776
STRELiTZIA you caught a very serious bug which was introduced with the latest changes to the core in 0.9.7. To be specific the detach() method in CFFStruct was the culprit. Updated versions of the Profiler and PE Insider are already online. As bad as it is, be reassured that it had nothing to do with the malware, in fact it could happen with any other executable and it’s in no way exploitable, it’s was just a very difficult bug to catch triggered only under certain circumstances (that’s also why it didn’t show in our automatic tests). Thanks for the report, it has been extremely useful!
Thanks a lot! Very handy
Thanks Elias!
Hello,
It is normal, to get empty fields?
Screenshot:
hxxp://www.freeimagehosting.net/akkcf
Well, if there’s a problem in the PE file, then it is possible. However, we would need to see the original file to verify if that’s the case.
Link to download sample:
hxxp://www.mediafire.com/download/jolhjl31f66t9dr/DiffView.rar
Regards
Thanks for the sample!
You’re right, that was a bug… It’s actually a security measure, a check for recursion, but it had a bug and hence this problem. Updated version is online, thanks for the report!
Awesome! always appreciate the quality of your work Daniel. One minor thing, the setup does not place an entry to the tool either in start menu or a desktop icon at all. Was this on purpose?
Thanks greg!
Yes, that was on purpose. In the future perhaps a shortcut will be created. The only reason why a setup has been used is that it can be digitally signed. A self-extracting zip is also an option, but a setup in the end could be extended to do useful things like shortcuts and file extensions associations. I admit the package is not much refined, but unfortunately this is a very busy summer… 😉
Hi, Thanks for awesome tool, Please add to context menu for easy open files.
are there any plans to add editing ?
Not for the near future, but it’s not to be excluded that it will be possible eventually.