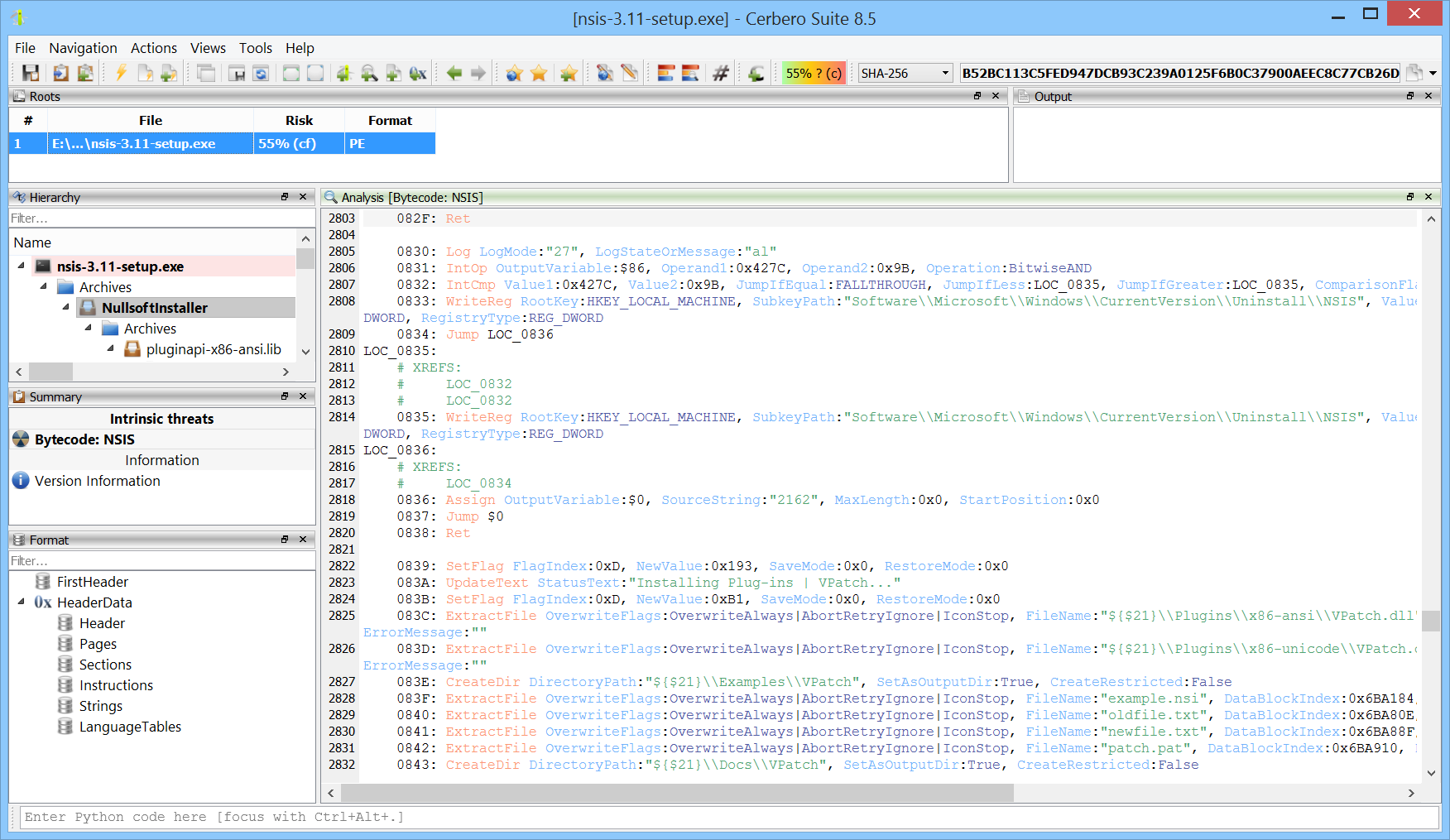
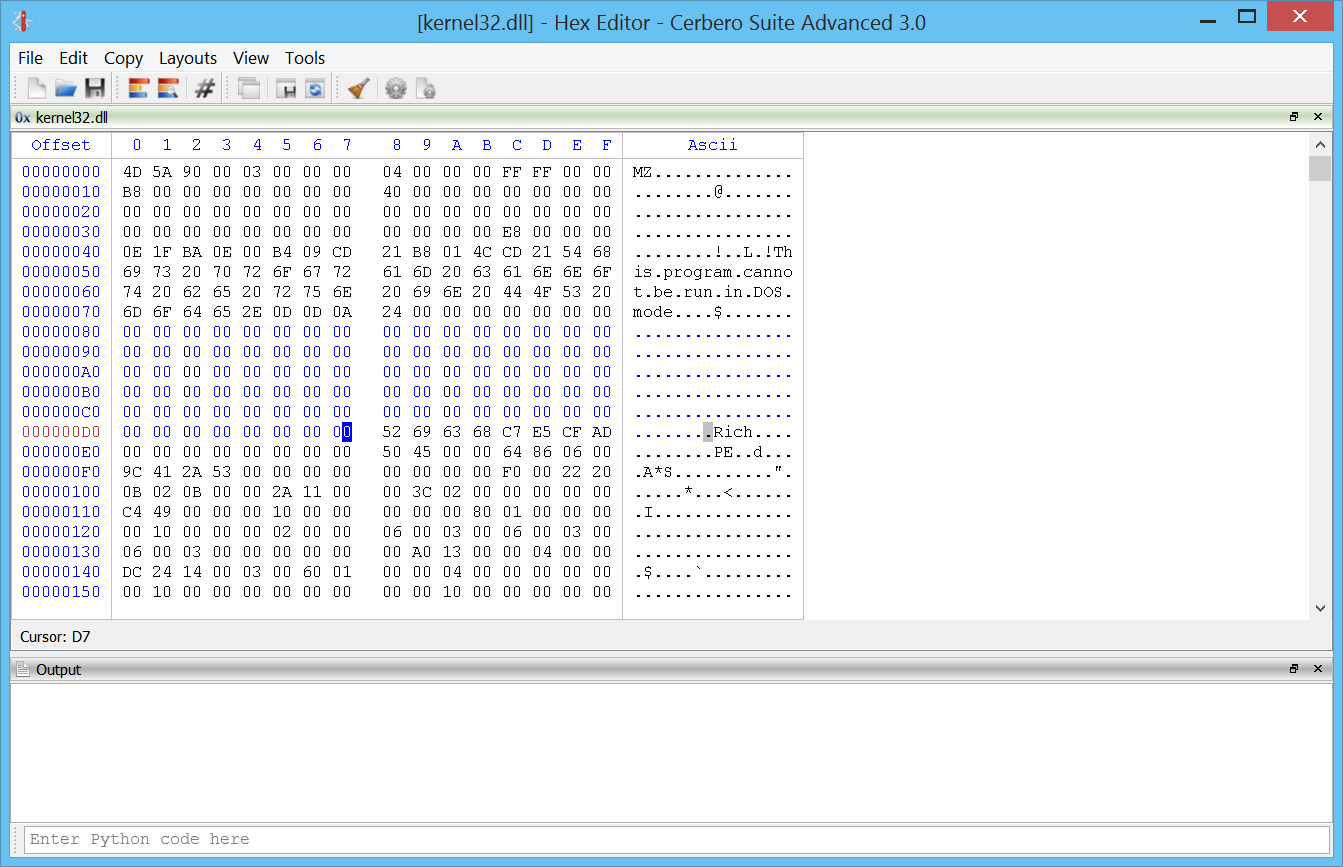
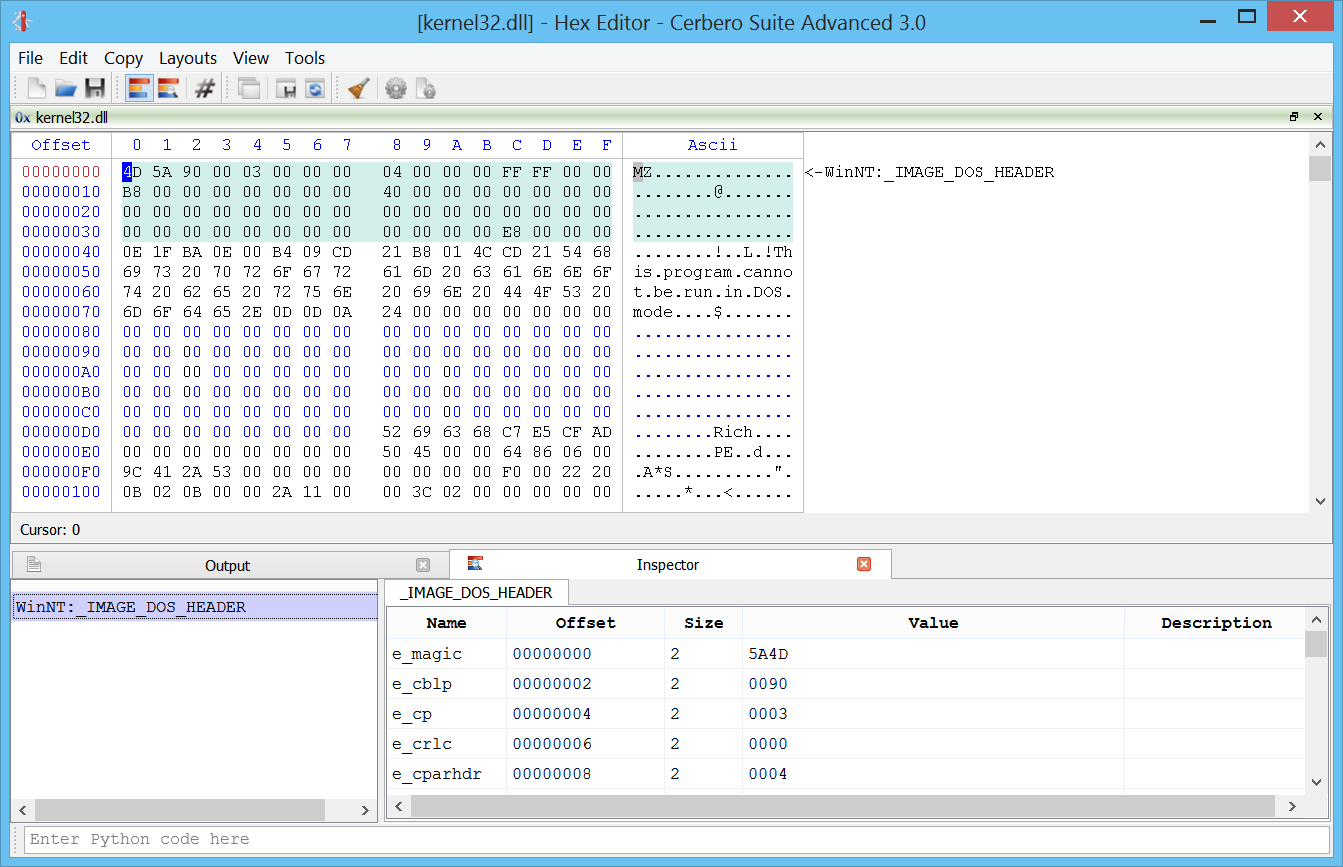
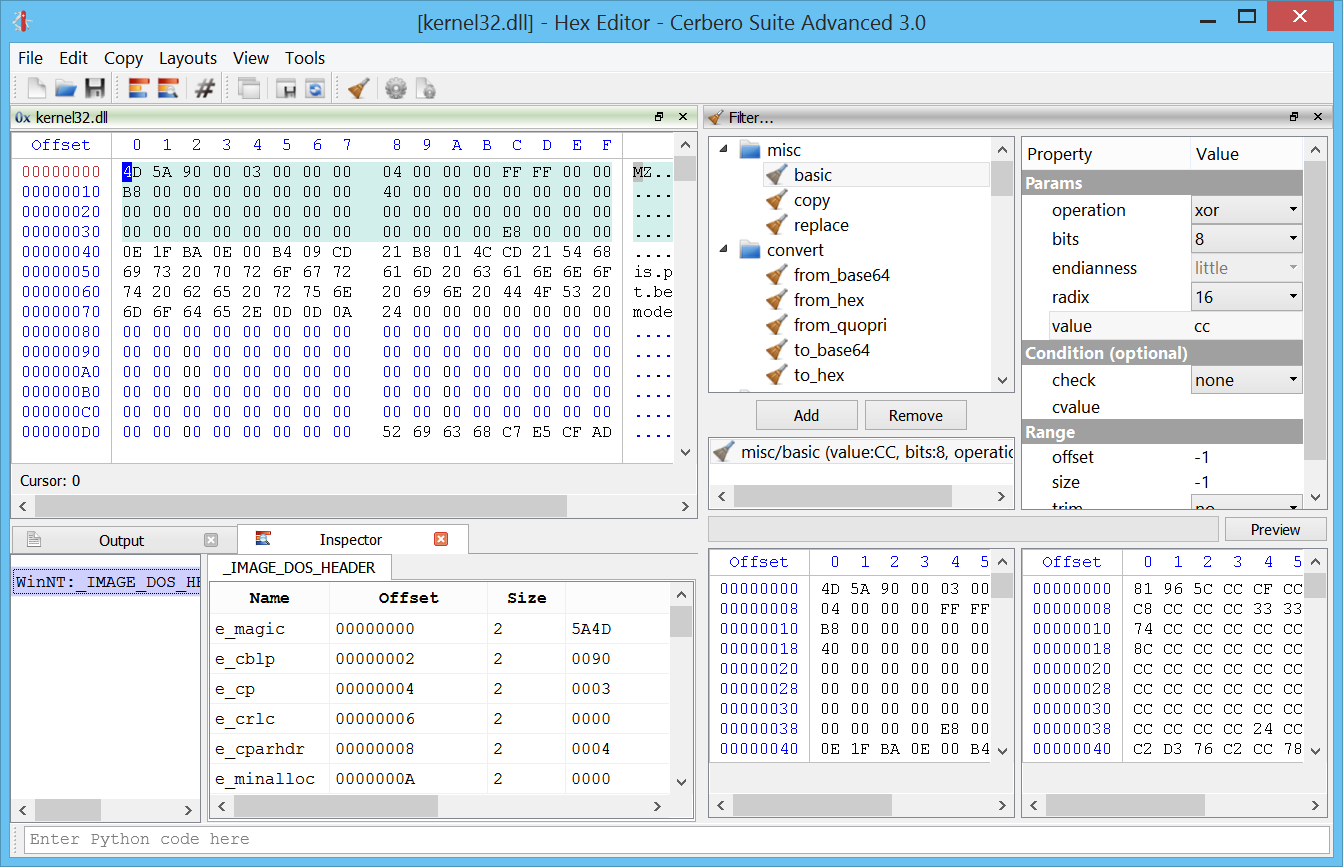
Windows memory forensics on OSX.
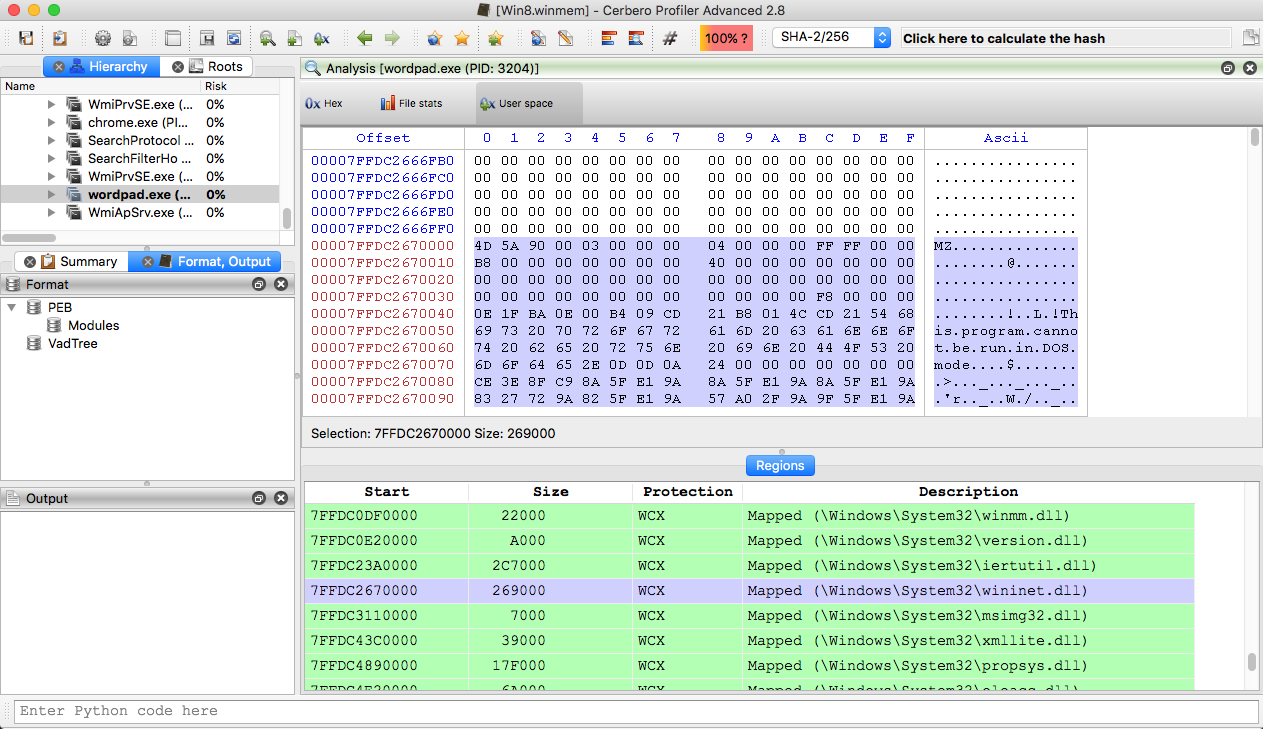
Profiler 2.8 is out with the following news:
+ added support for Windows raw memory images
– added unhandled exception debug tools on Windows
– added unhandled exception notification for Python
– exposed tree control to the Python SDK
– improved CFBF support
– improved PDF parsing against new malware samples
– fixed PDB issue with zero-sized streams
– fixed issues in JBIG2 decoder
– fixed display of PE timestamps in UTC
The biggest news is undoubtedly the introduction of Windows memory forensics support in the Advanced version of Profiler.
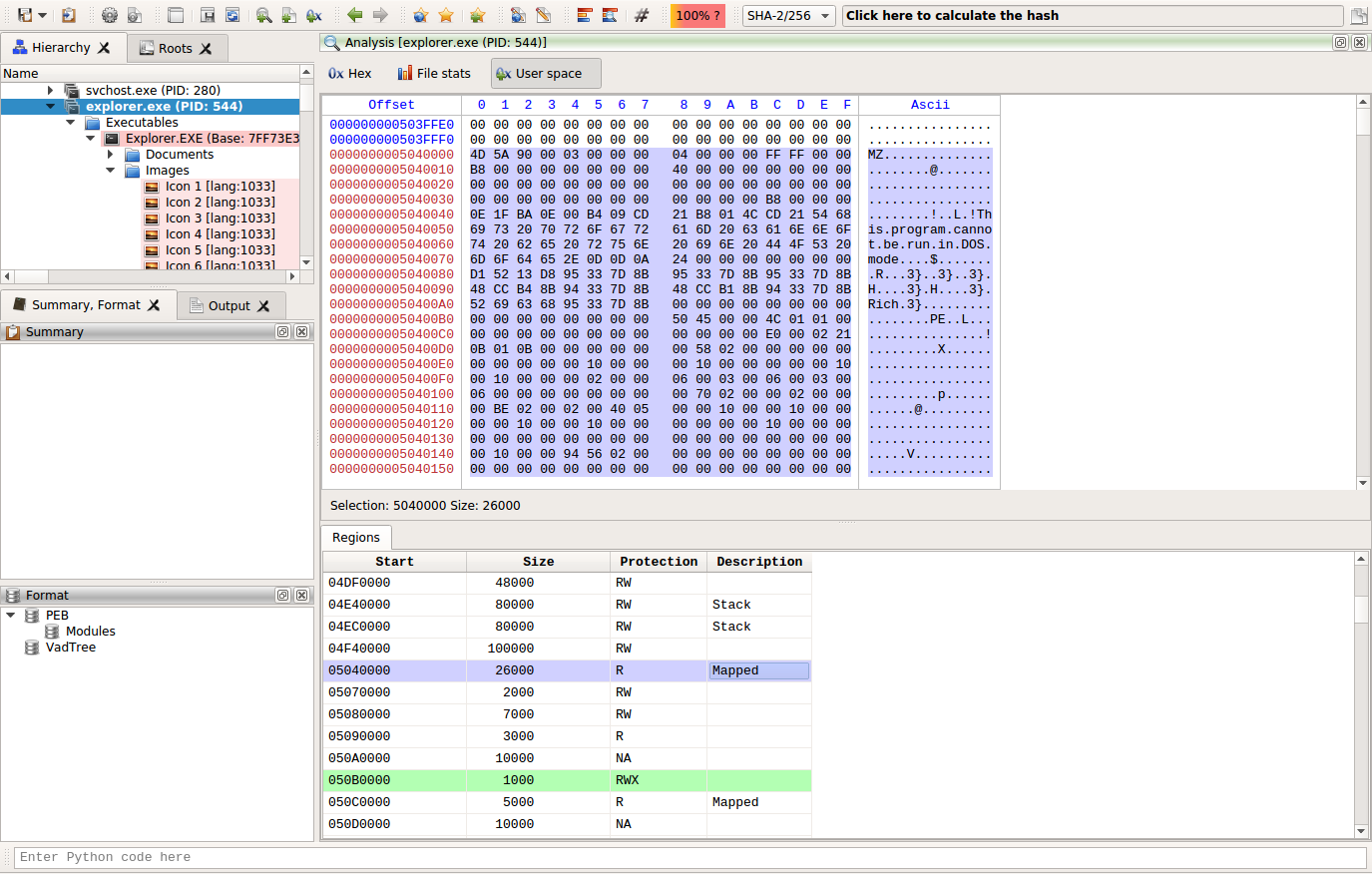
And here’s the same screenshot as above taken on Linux.
Improved Exception Handling
We have also drastically improved exception handling for both Python and native code, especially on Windows.
Whenever Python raises an unhandled exception a message box pops up on Windows and on other systems the exception is printed out to the terminal if it happens outside of the UI thread.
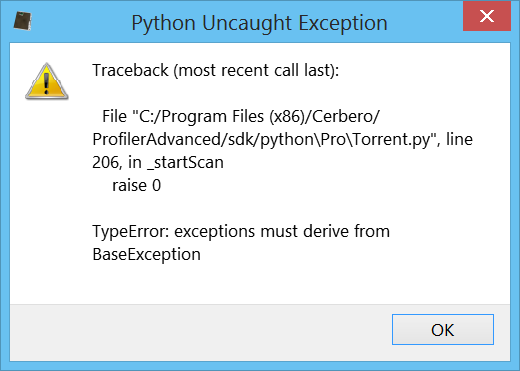
When the issue is more serious and results in a crash the user will be presented with the following message box on Windows.
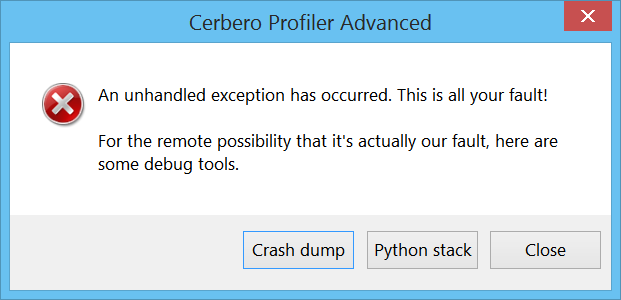
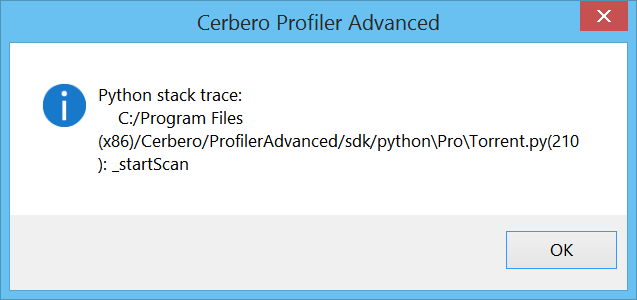
If the crash happened from Python code, the user is given the possibility to retrieve a backtrace of the last executed Python methods.
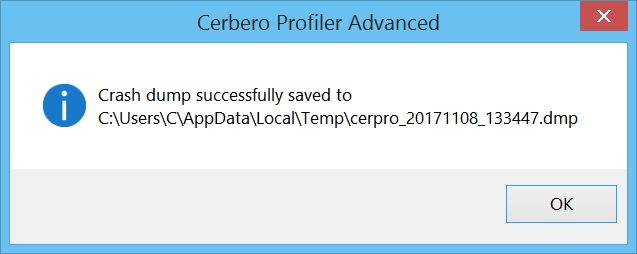
If the crash happened in the native code, it’s now possible to create a dump file.
Enjoy!