We have added support for the Microsoft Office ActiveMime format. This format can be used to encapsulate Office documents and hide their contents during analysis. You can download the package from Cerbero Store.
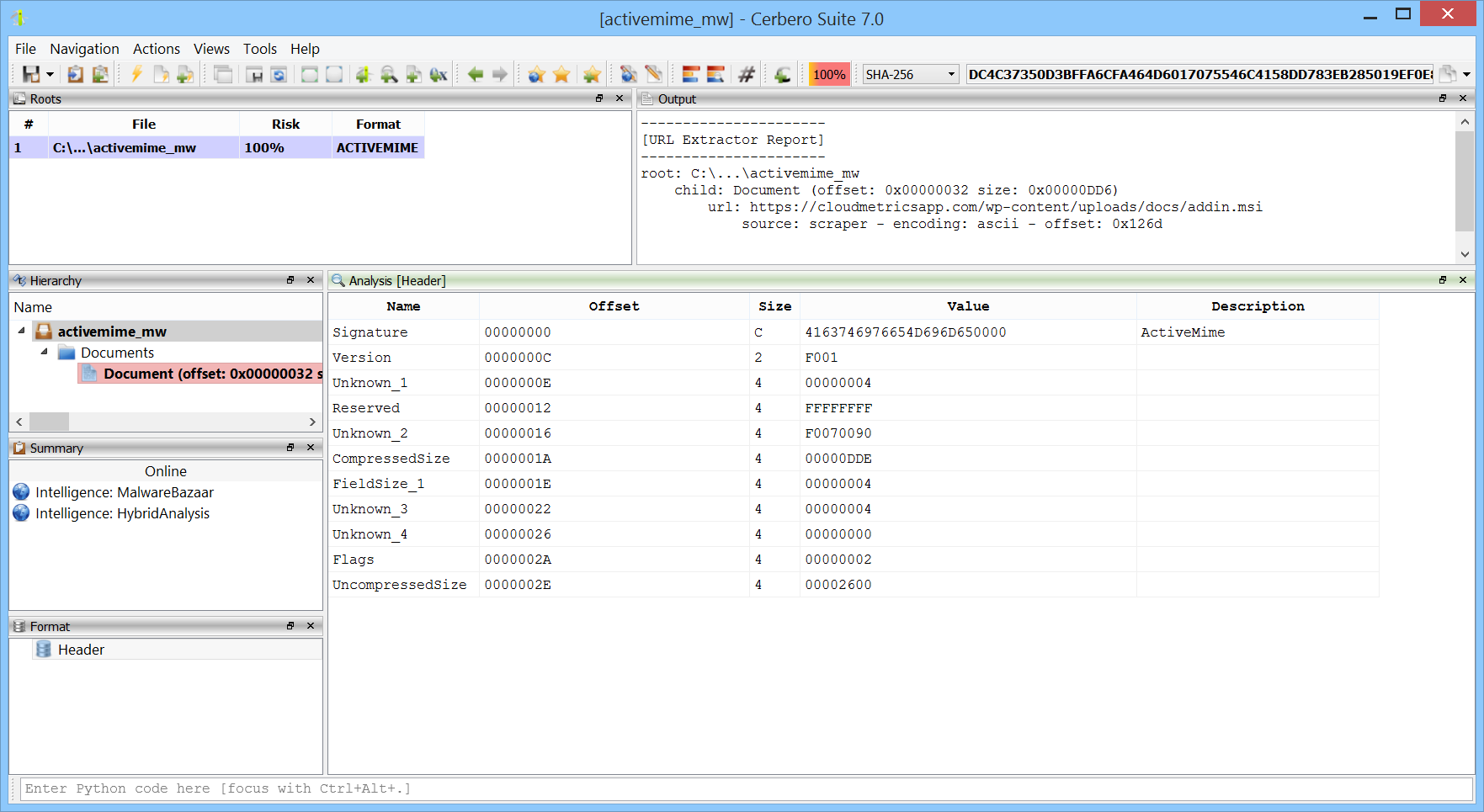
We have added support for the Microsoft Office ActiveMime format. This format can be used to encapsulate Office documents and hide their contents during analysis. You can download the package from Cerbero Store.

The malware sample analyzed in this video uses VBA code to extract a payload contained in Excel spreadsheet cells.
SHA256: F00252AB17546CD922B9BDA75942BEBFED4F6CDA4AE3E02DC390B40599CE1740
The following is the Python code which mimics the VBA extraction code.
from Pro.SiliconSpreadsheet import *
from Pro.UI import proContext
v = proContext().getCurrentAnalysisView()
if v.isValid():
view = SiliconSpreadsheetWorkspaceView(v)
ws = view.getSpreadsheetWorkspace()
sheet = ws.sheetFromName("Final Offer")
col = SiliconSpreadsheetUtil.colIndex("BS")
text = ""
for i in range(100, 701):
cell = sheet.getCell(col, i)
if cell.isEmpty():
continue
text += cell.value
print(text[::-1])
Note: the code must be executed while the spreadsheet is open in the analysis view.
From a Twitter post by InQuest, we analyzed an interesting malware:
Encrypted MS Office Document, VBA, Windows Link File (LNK), OLE objects, Windows Help Files (CHM), PNG steganography and Powershell.
SHA256: 46AFA83E0B43FDB9062DD3E5FB7805997C432DD96F09DDF81F2162781DAAF834
The analysis should take about 15-20 minutes in Cerbero Suite.
Highly recommended!
SPOILER ALERT: The images below show all the steps of our analysis.
This Microsoft Office document belongs to the Emotet malware campaign and as part of its obfuscation strategy uses the content of text boxes from its VBA code. In the upcoming Cerbero Suite 5.1 we have simplified the analysis of text controls by previewing their name in the format view.
The script below deobfuscates the VBA code.
from Pro.UI import *
v = proContext().findView("Analysis [VBA code]")
if v.isValid():
s = v.getText()
lines = s.split("\n")
new_lines = []
for line in lines:
if line.strip().startswith(("'", "Debug.Print")):
continue
while True:
i = line.rfind("'")
if i == -1:
break
line = line[:i]
new_lines.append(line)
print("\n".join(new_lines))
This script concatenates strings such as “a” + “b”:
from Pro.UI import *
import re
ctx = proContext()
v = ctx.getCurrentView()
if v.isValid() and v.hasSelection():
s = v.getSelectedText().replace('" &', '" +')
s = eval(s)
v.setSelectedText('"' + s + '"')
This second script decrypts strings the same way as the “NobosMeik” function:
from Pro.UI import *
import base64
ctx = proContext()
v = ctx.getCurrentView()
if v.isValid() and v.hasSelection():
s = v.getSelectedText()
s = base64.b64decode(s)
key = b"versache"
s2 = bytearray(s)
y = 0
tire = lambda r, g: (r & ~g) | (~r & g)
for x in range(len(s)):
s2[x] = tire(s2[x], key[y])
if y < len(key) - 1:
y += 1
else:
y = 0
print(s2)