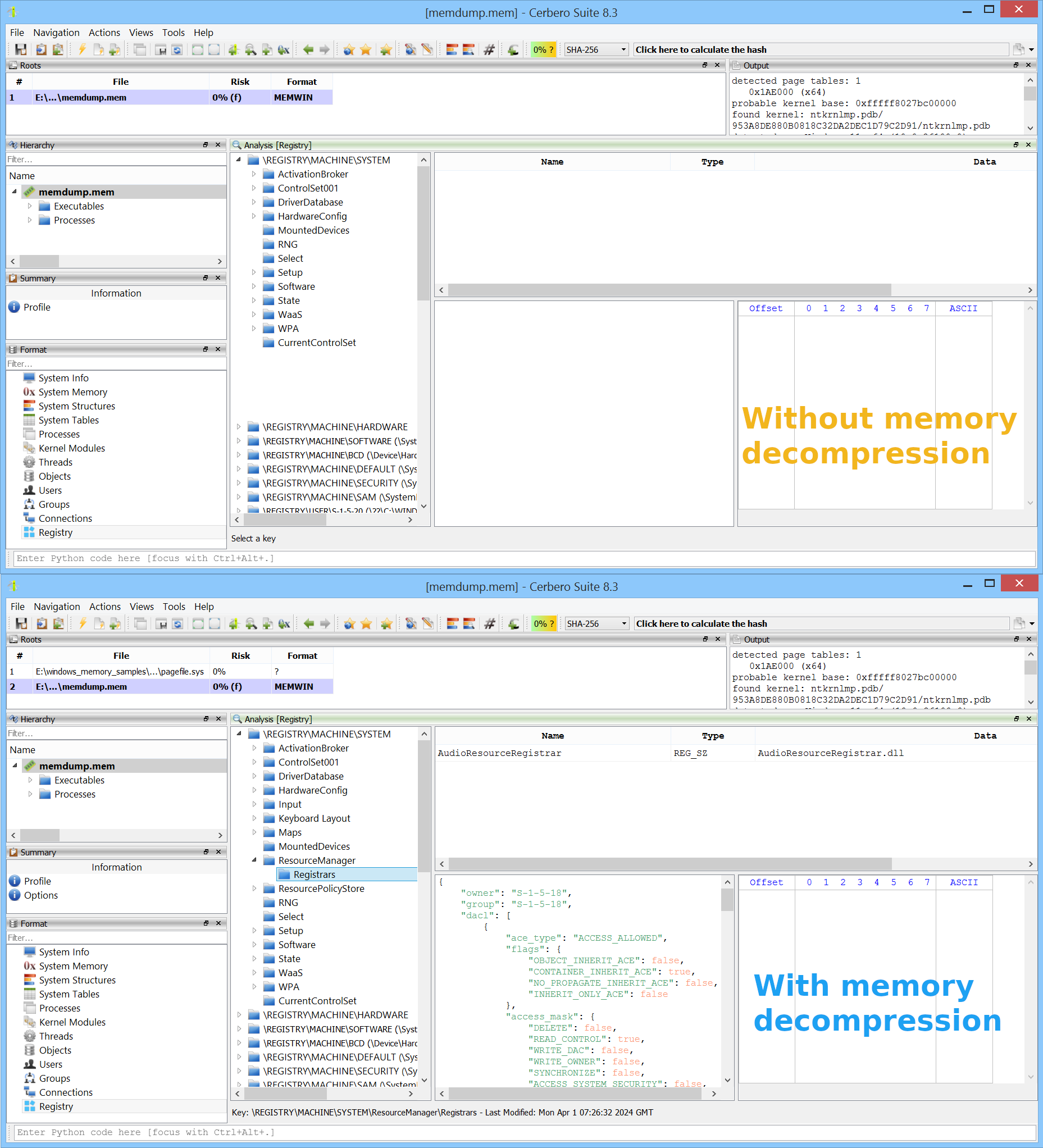
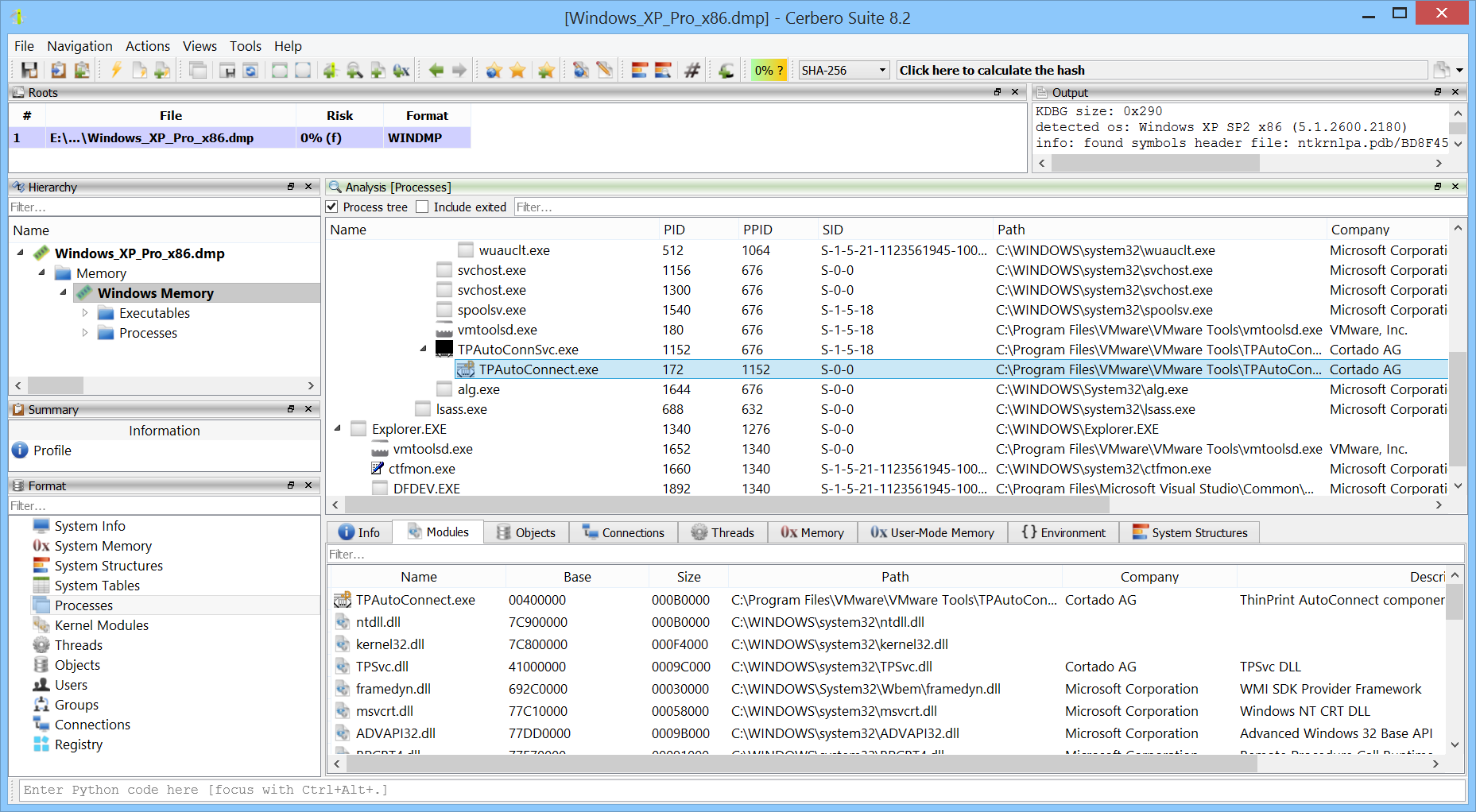
We’ve released version 0.4 of the Memory Analysis package, currently in beta for our commercial customers and soon to be available for personal licenses too. The main highlight is that, thanks to Cerbero Suite 8.4, all tables now support sorting — but there are other new features as well, which we’ll cover in this blog post.
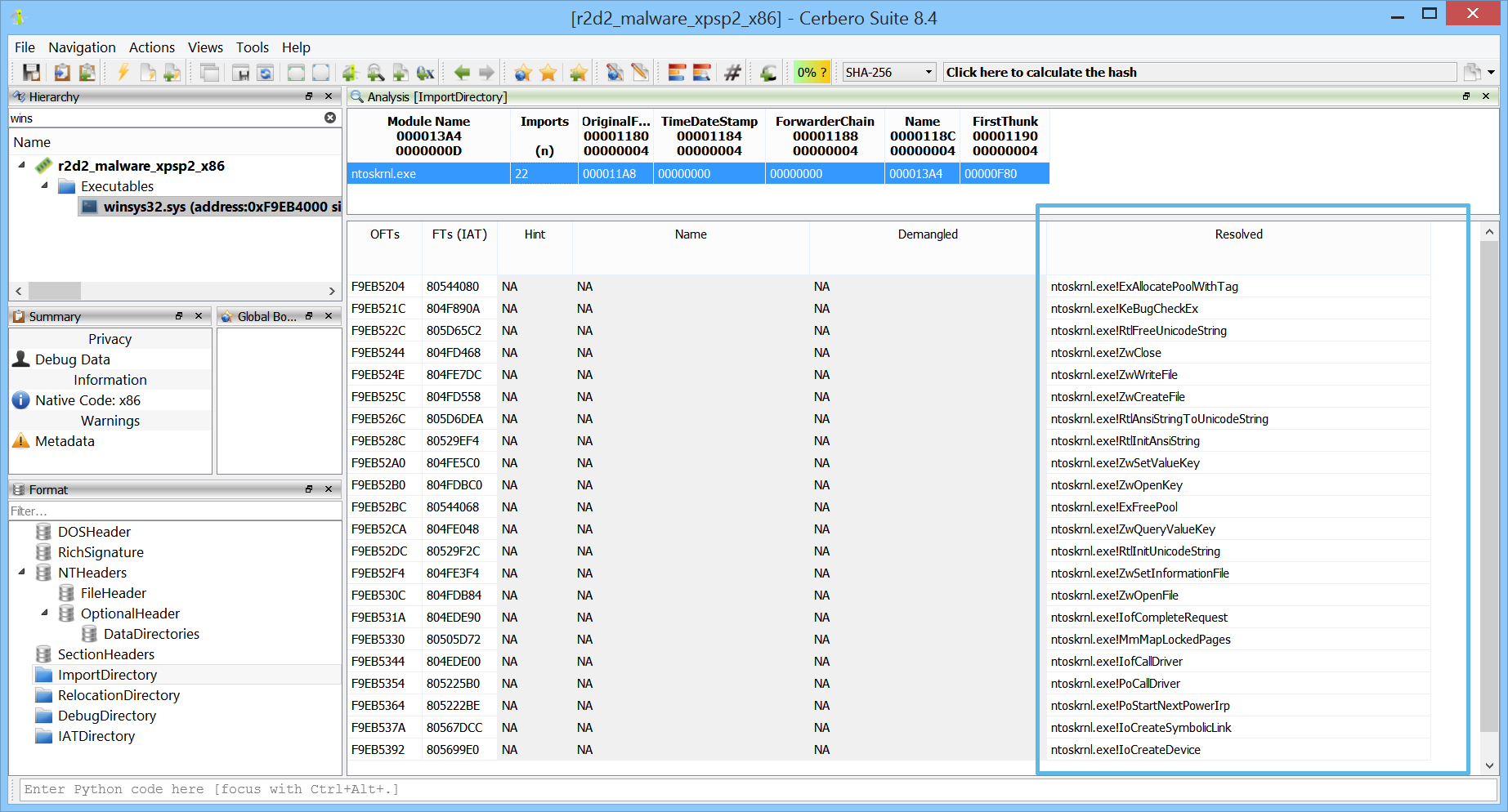
When inspecting a PE in memory, viewing the import table is useful — but seeing what the IAT entries actually point to is even better, especially if the import information is no longer available.