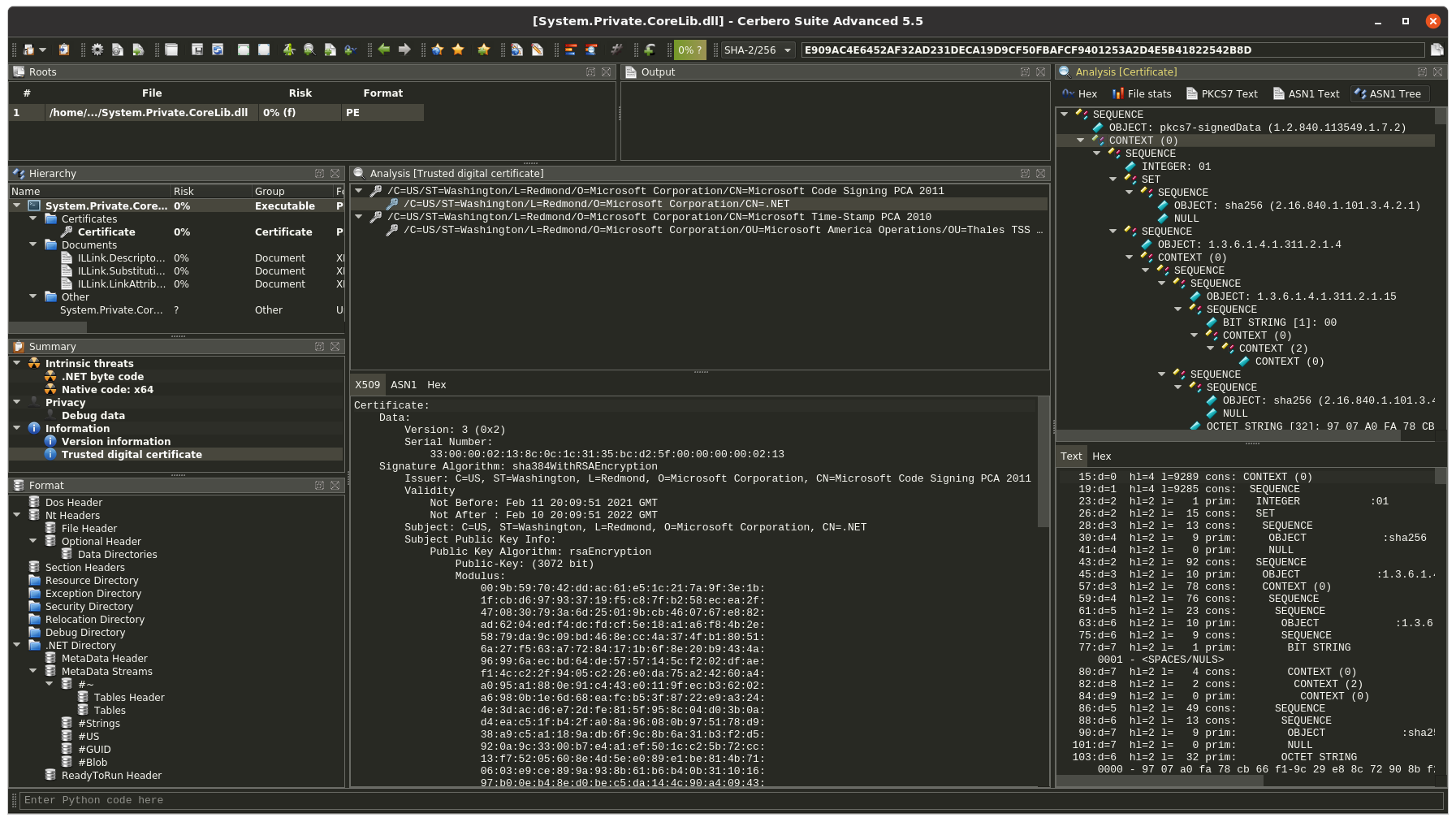
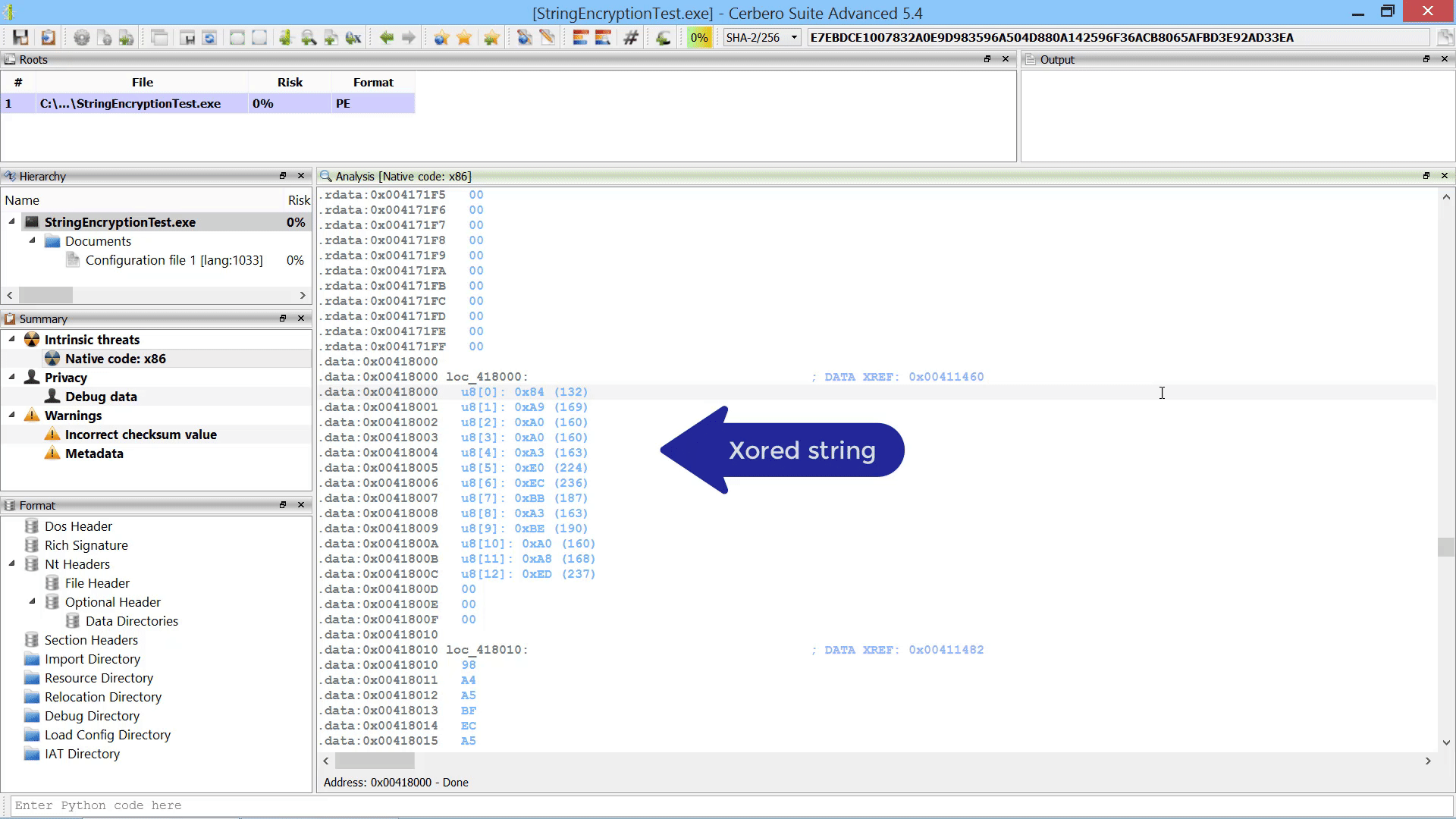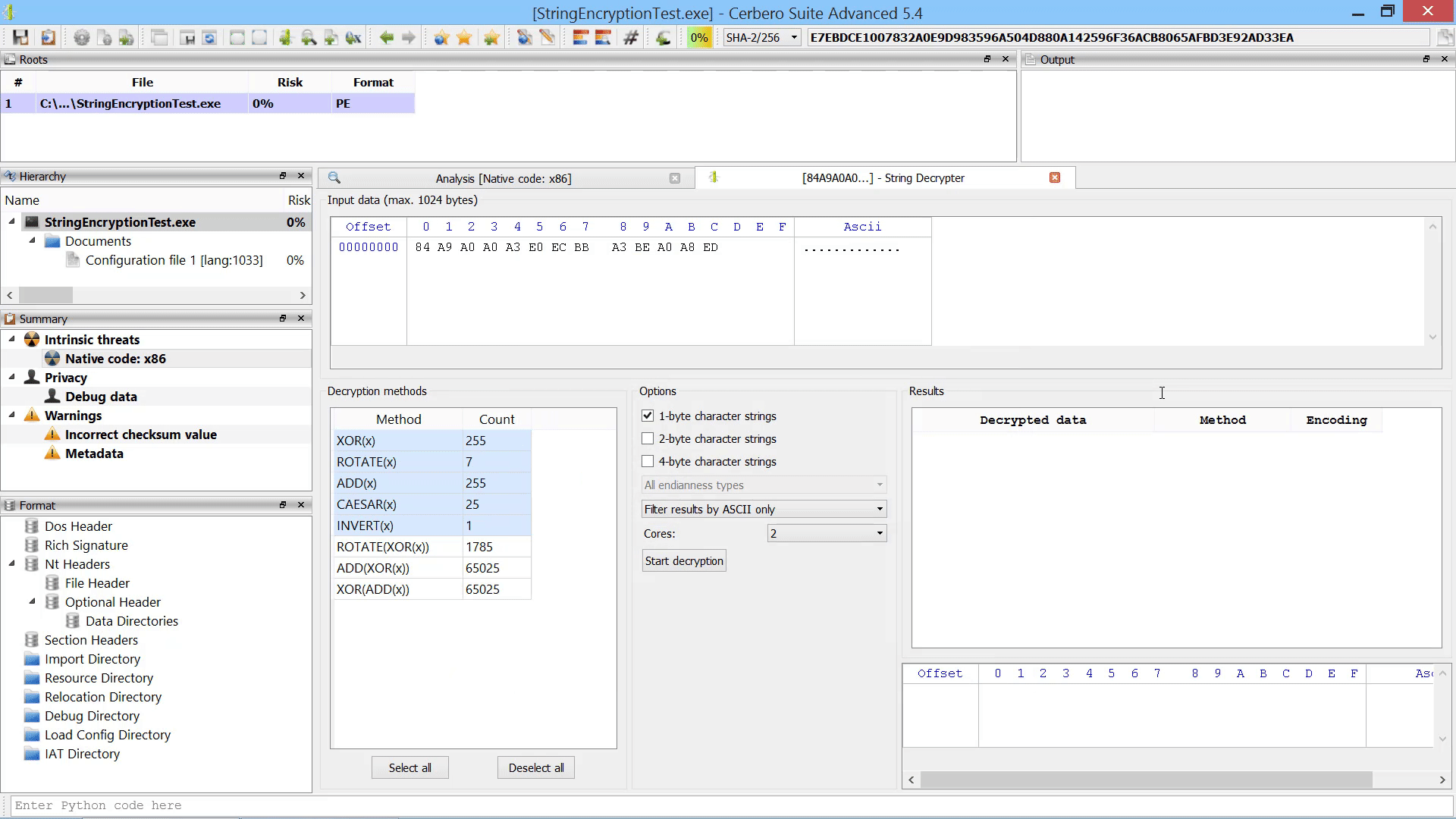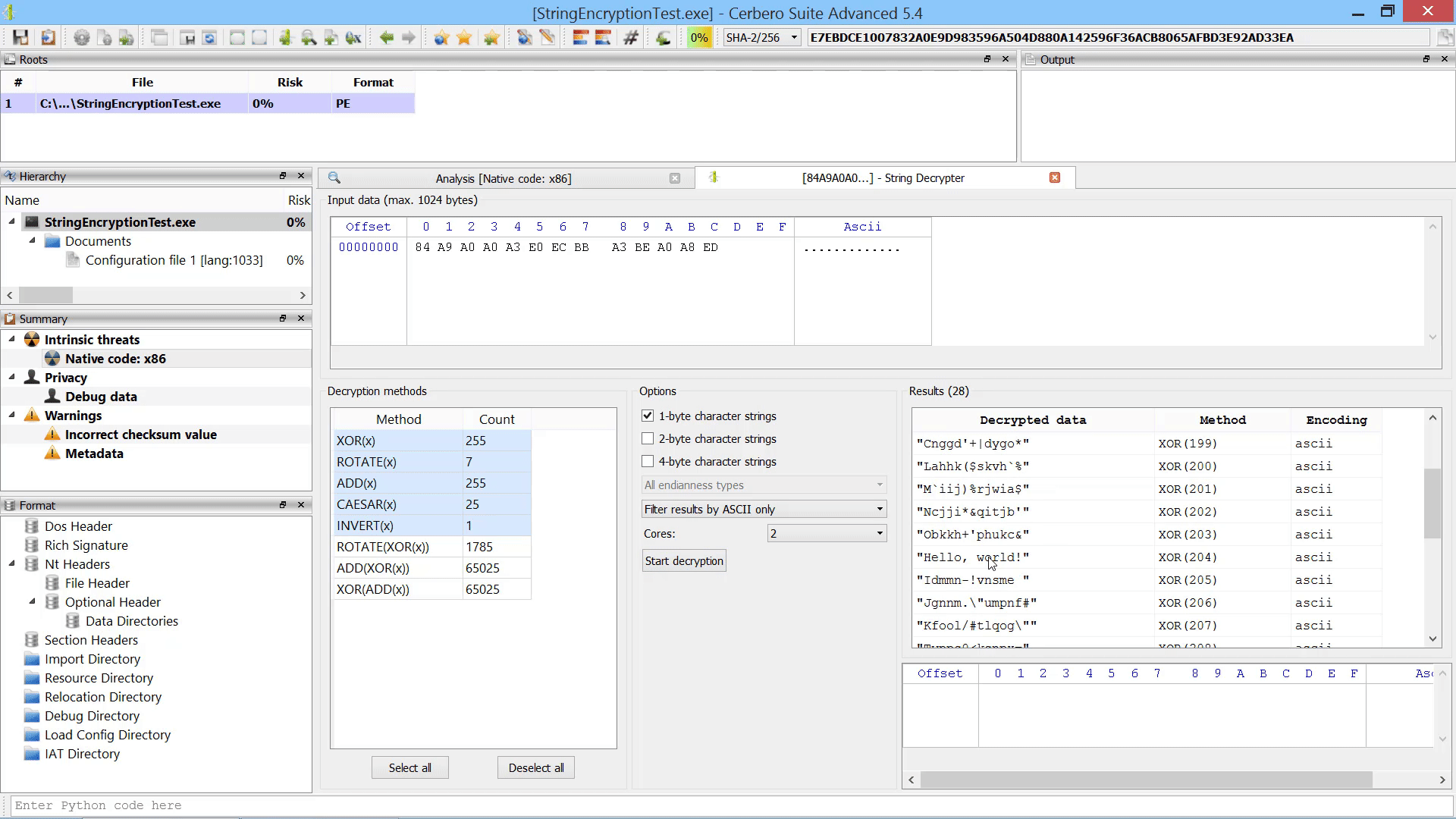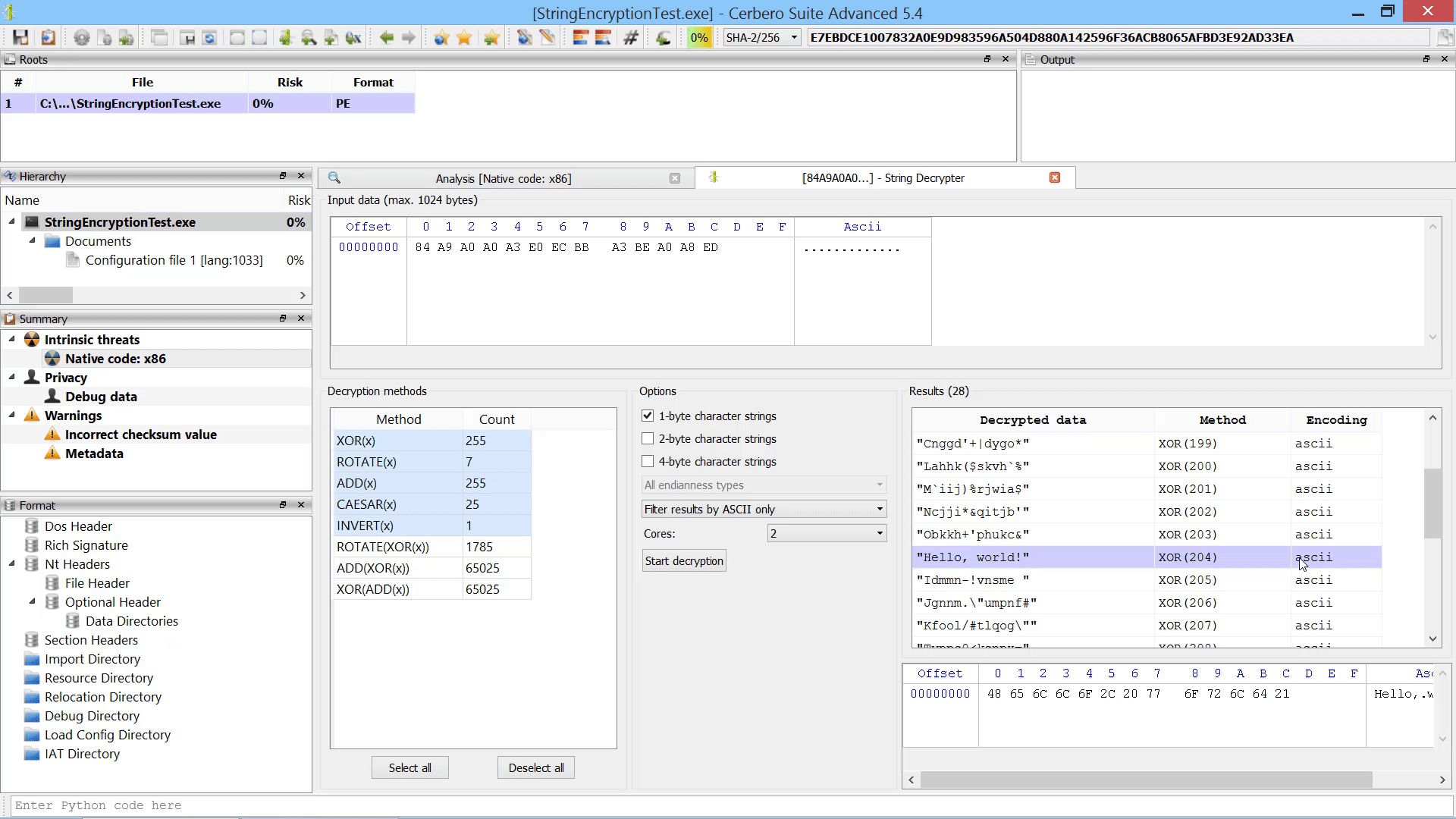
With the upcoming releases customers with commercial licenses for Cerbero Suite Advanced and Cerbero Engine can verify Microsoft Authenticode signatures on Linux and macOS. Our Authenticode support includes full-chain certificate and time-stamp verification.
In conjunction with our recently extended support for certificate file formats, this provides complete support for inspecting signed Portable Executable binaries.
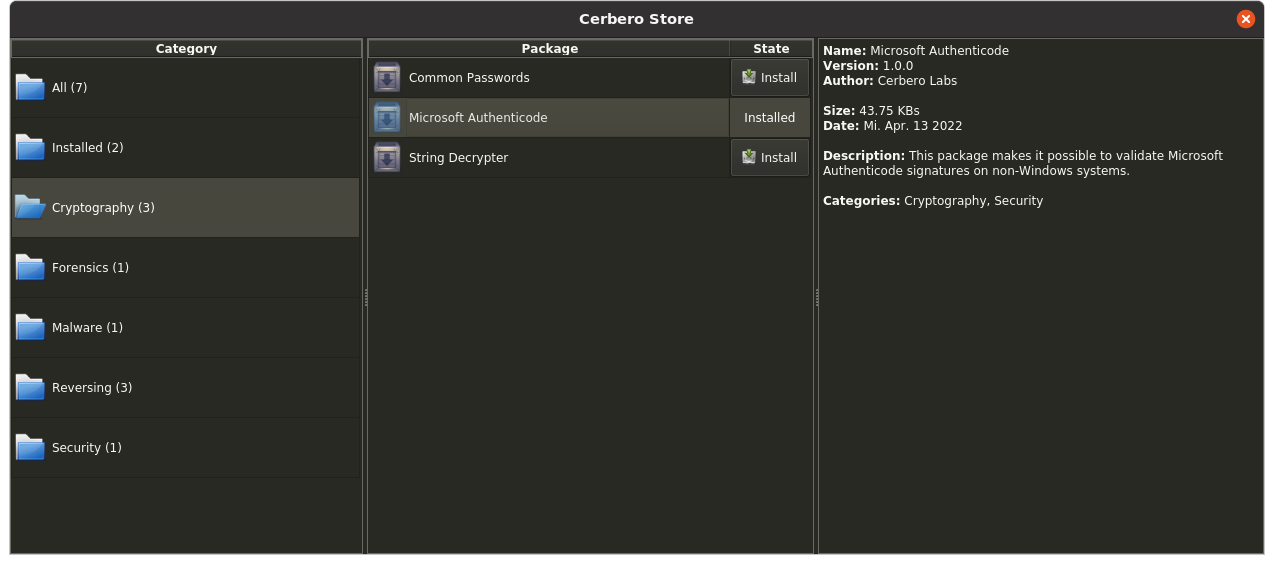
The only required step to verify Authenticode signatures on non-Windows systems is to install our “Microsoft Authenticode” package from Cerbero Store.
Cerbero Suite has been using its own implementation of Microsoft Authenticode for performance reasons since the very beginning, back in 2012. However, thanks to the recently introduced Cerbero Store we can now offer this feature on systems other than Windows.
We have also exposed Authenticode validation to our Python SDK.
from Pro.PE import * print(PE_VerifyAuthenticode(obj))
Alternatively, scan hooking extensions can check the generated report for the validation scan entries.