In this post we’ll be talking about the improvements we’ve made to the command line in Cerbero Suite.
If you’re familiar with command-line scripting in Cerbero Suite, you might know that by running a script without the “-c” argument all output is redirected to the output view in the main window.
In certain cases, however, it might be desirable to avoid the creation of a main window.
For this purpose we have introduced the ‘-g’ argument.
For example:
cerpro.exe -g -r foo.py
If the script doesn’t create an output view, then the output of the ‘print’ function isn’t visible.
Furthermore, in the upcoming 5.5 version of Cerbero Suite we have added terminal support on Windows.
On Windows running scripts with the ‘-c’ argument results in not being able to see the stdout output. The reason for this is that the cerpro executable is built as a GUI application and therefore is not attached to a terminal.
To overcome this limitation we have added a launcher on Windows called “cerpro_console.exe”.
For example:
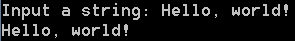
cerpro_console.exe -e "t=input('Input a string: ');print(t)"
The code asks the user to input a string and prints it back.
Of course, the cerpro_console executable can be used to launch any functionality of Cerbero Suite which supports console mode (‘-c’).
For example the following command prints out the command-line help to stdout:
cerpro_console.exe -h
Soon we’ll publish a complete tutorial about command-line scripting on our SDK page.