Here summarized are the main news of this release of Cerbero Suite 5.5 and Cerbero Engine 2.5.
Cerbero Engine Editions
Cerbero Engine already supports various platforms and architectures. Now, it comes in two different editions: Classic and Metal.
While in the Classic edition all UI functions are available, the Metal edition comes without UI dependencies.

The Metal edition is designed to be run in cloud and server environments which may lack a graphical interface.
We took great care in preserving plugin compatibility.
Plugins which import graphical functions are compatible with the Metal edition: all UI functions are available, though they are provided only as stubs. A few graphical methods like msgBox fall back to console I/O.
Providing two editions of Cerbero Engine allows us to offer the perfect fit for organizations which need a powerful and flexible back-end for their services.
Microsoft Authenticode on Linux and macOS
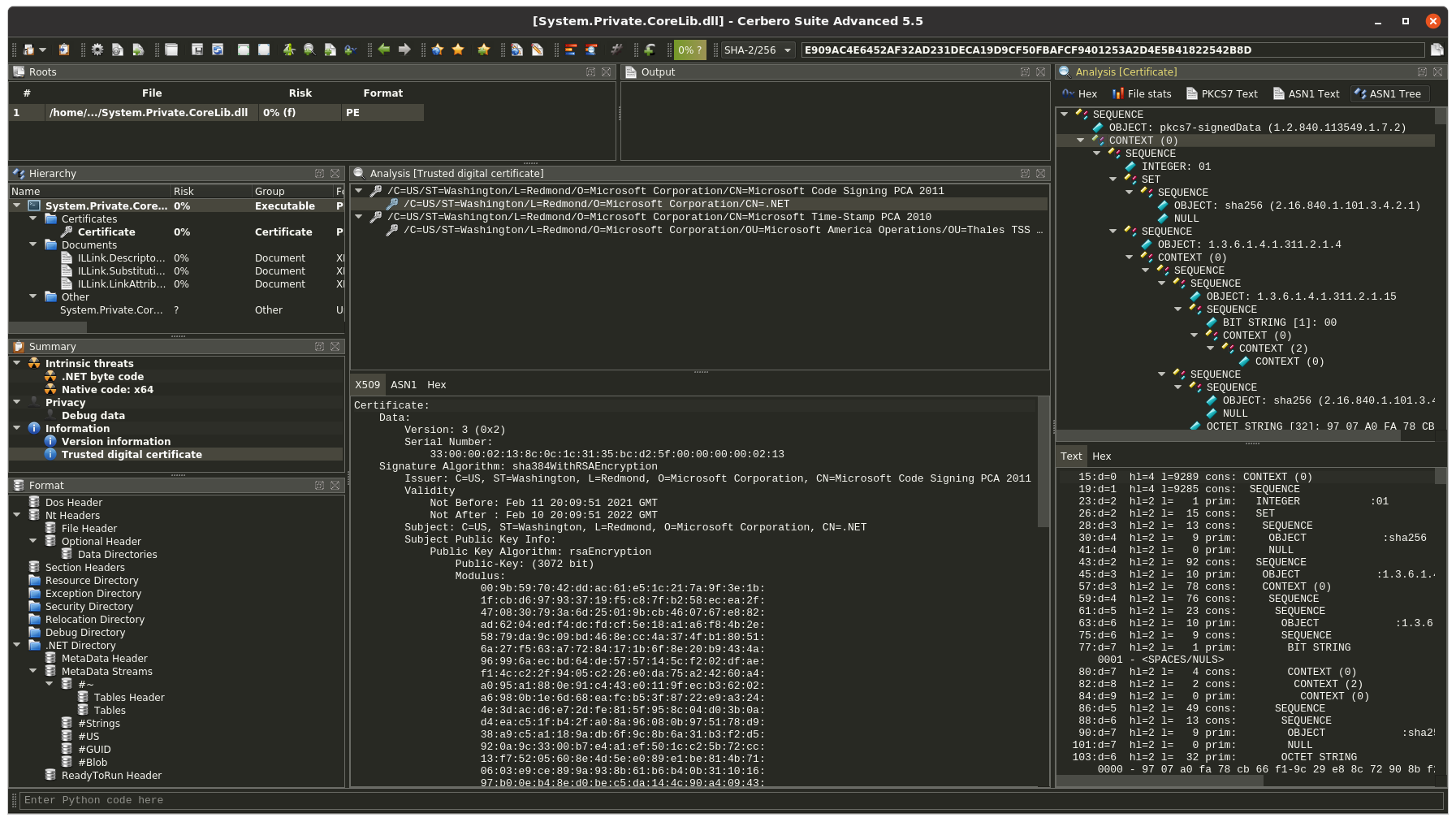
Customers with commercial licenses for Cerbero Suite Advanced and Cerbero Engine can verify Microsoft Authenticode signatures on Linux and macOS. Our Authenticode support includes full-chain certificate and time-stamp verification.
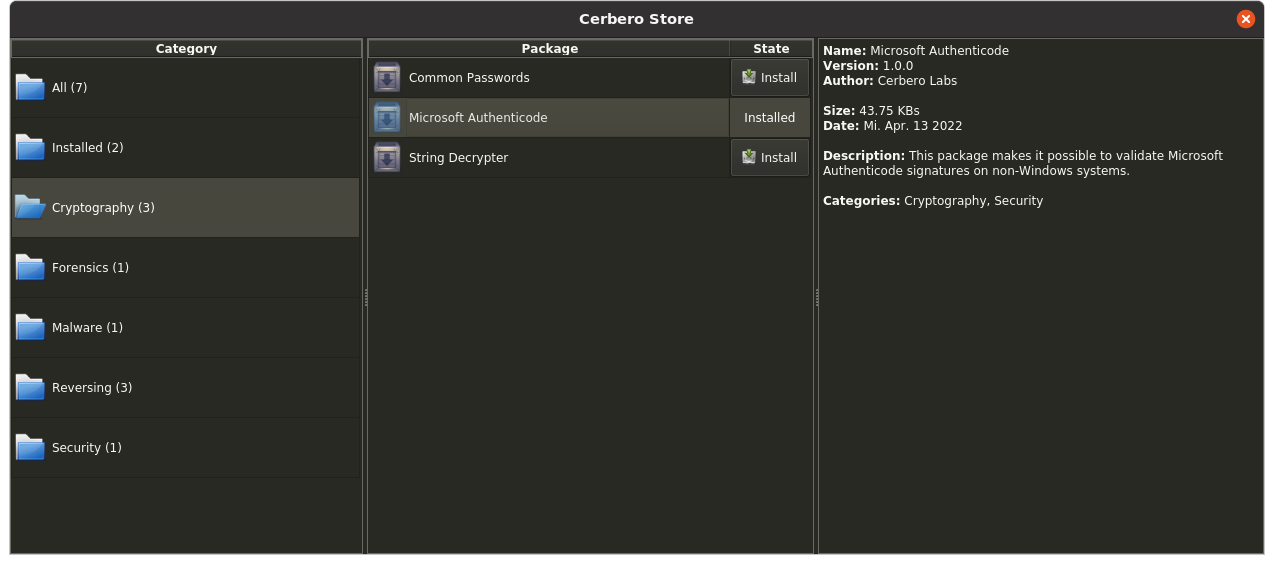
The only required step to verify Authenticode signatures on non-Windows systems is to install our “Microsoft Authenticode” package from Cerbero Store.
Cerbero Suite has been using its own implementation of Microsoft Authenticode for performance reasons since the very beginning, back in 2012. However, thanks to the recently introduced Cerbero Store we can now offer this feature on systems other than Windows.
We have also exposed Authenticode validation to our Python SDK. You can read more about the topic in our dedicated post.
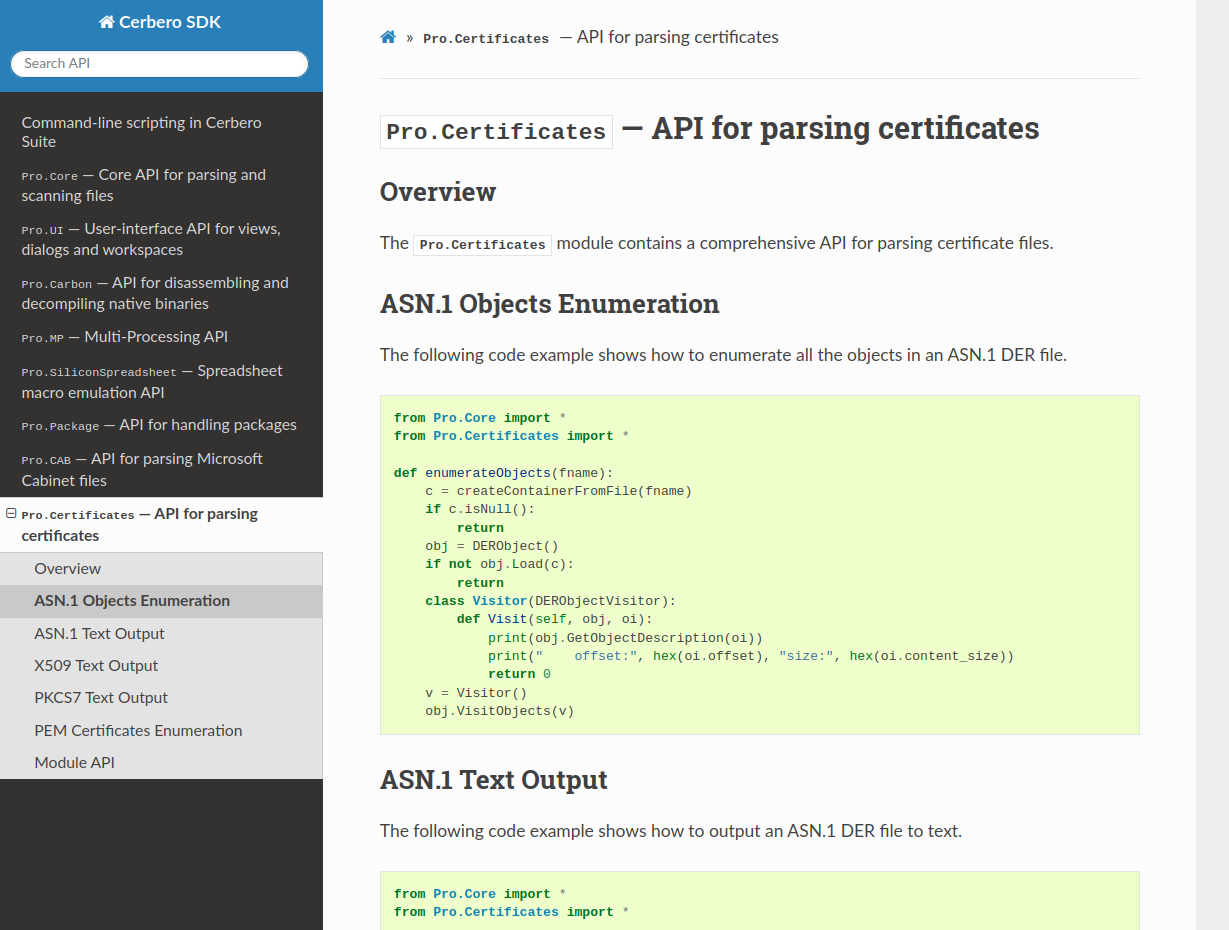
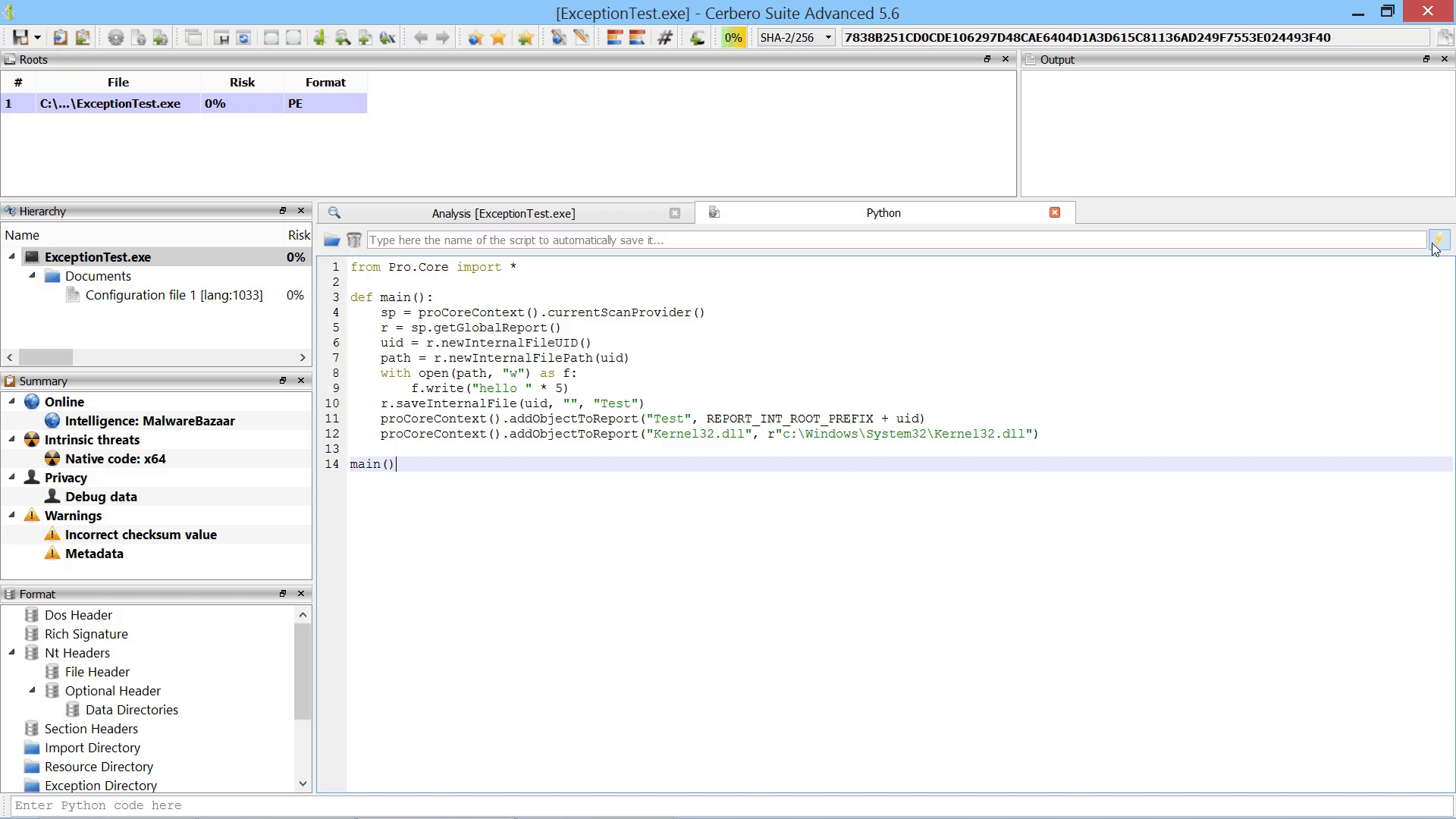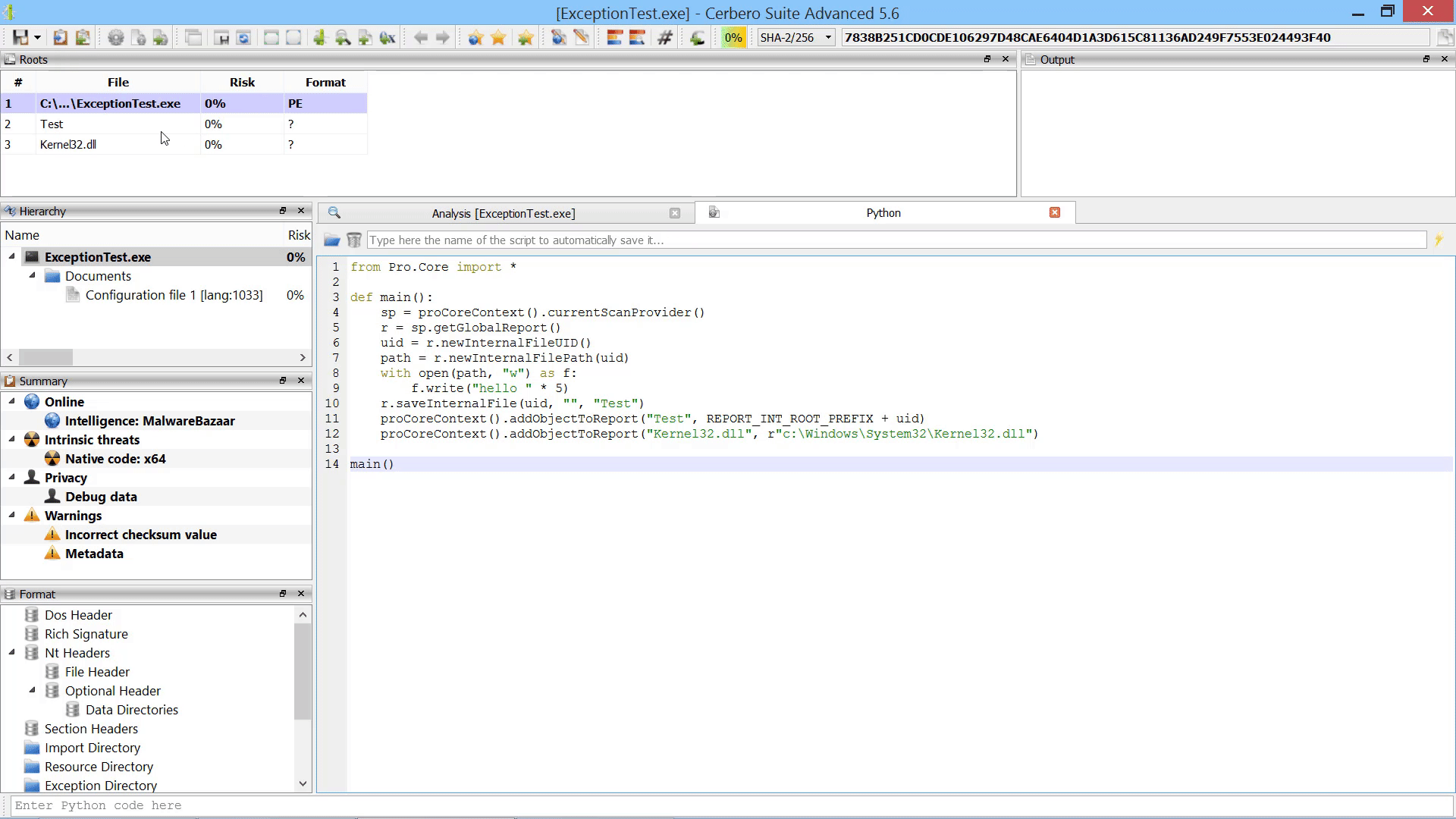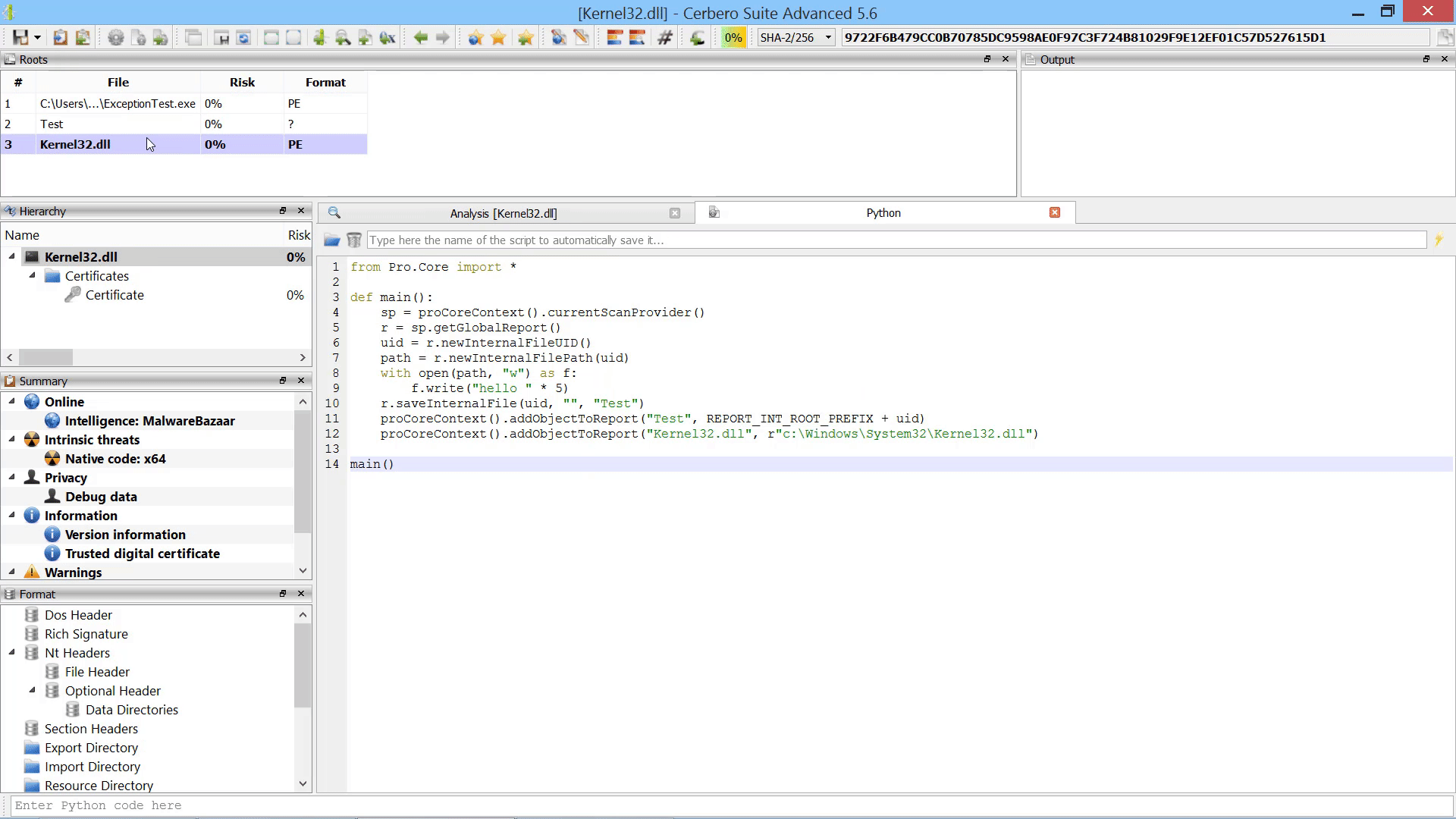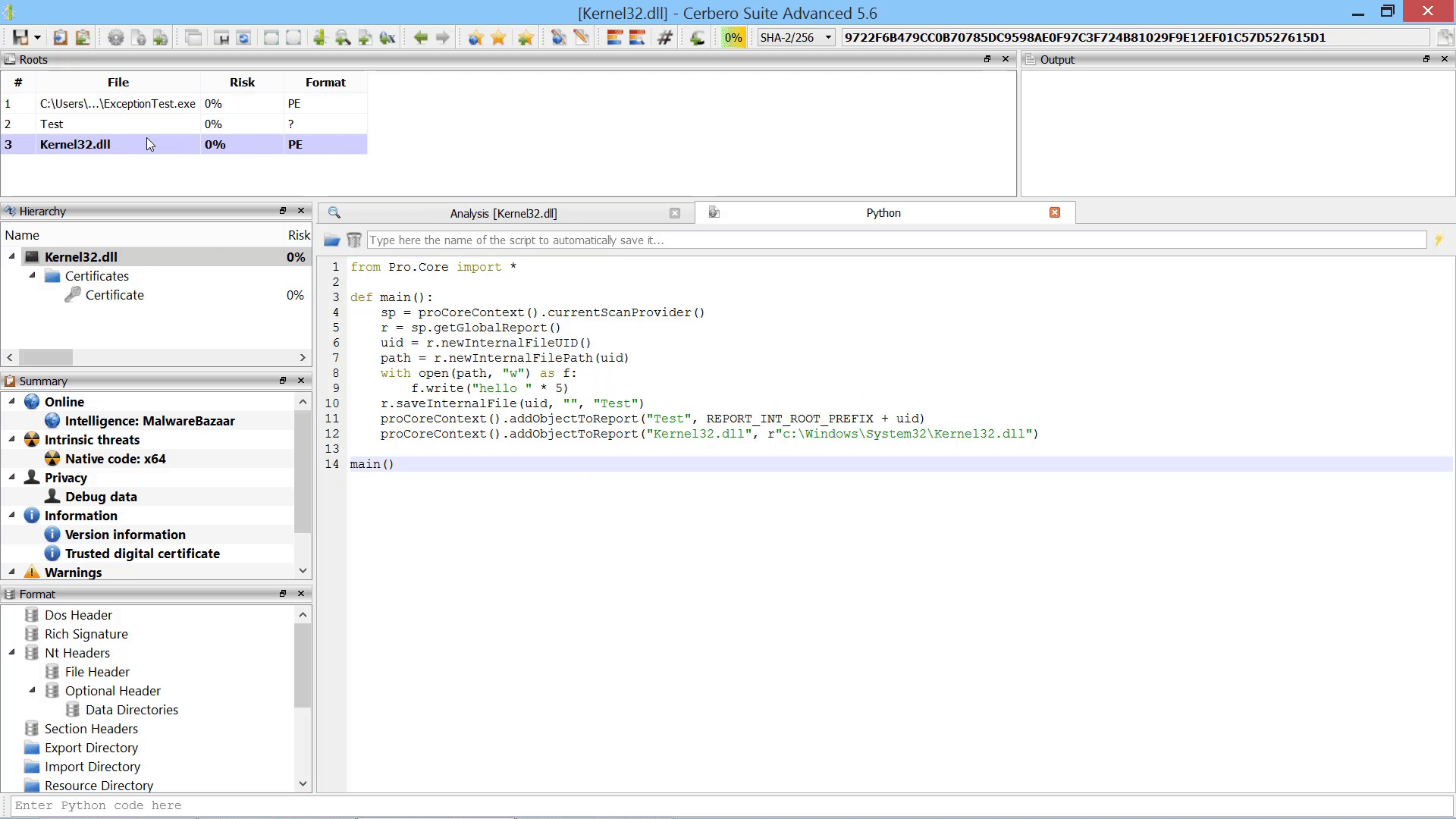
Certificates Support
While Cerbero Suite already lets you inspect certificates inside binaries, now it can load them directly from disk and also lets you inspect each individual ASN1 object.
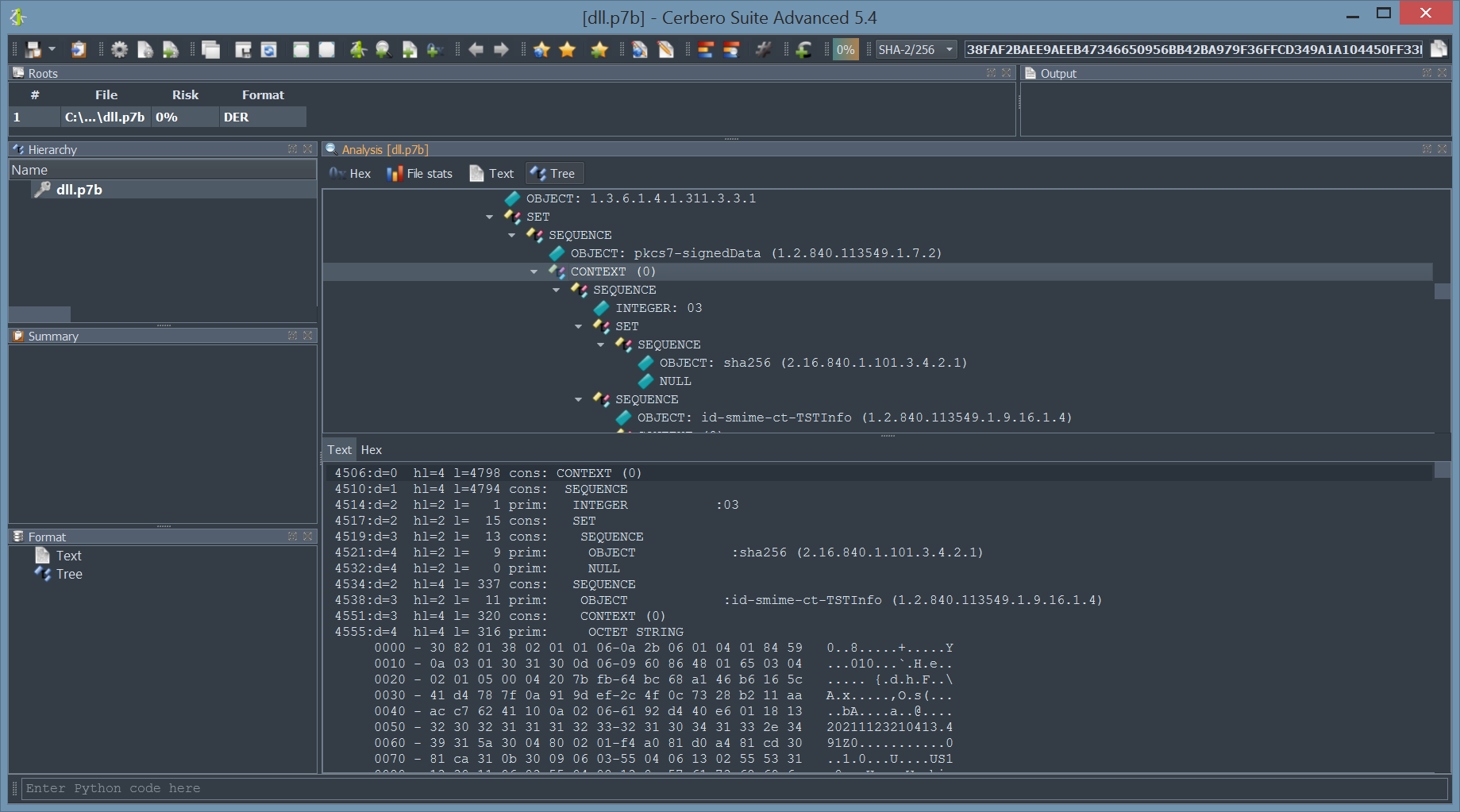
Both DER and PEM encodings for certificates are supported.
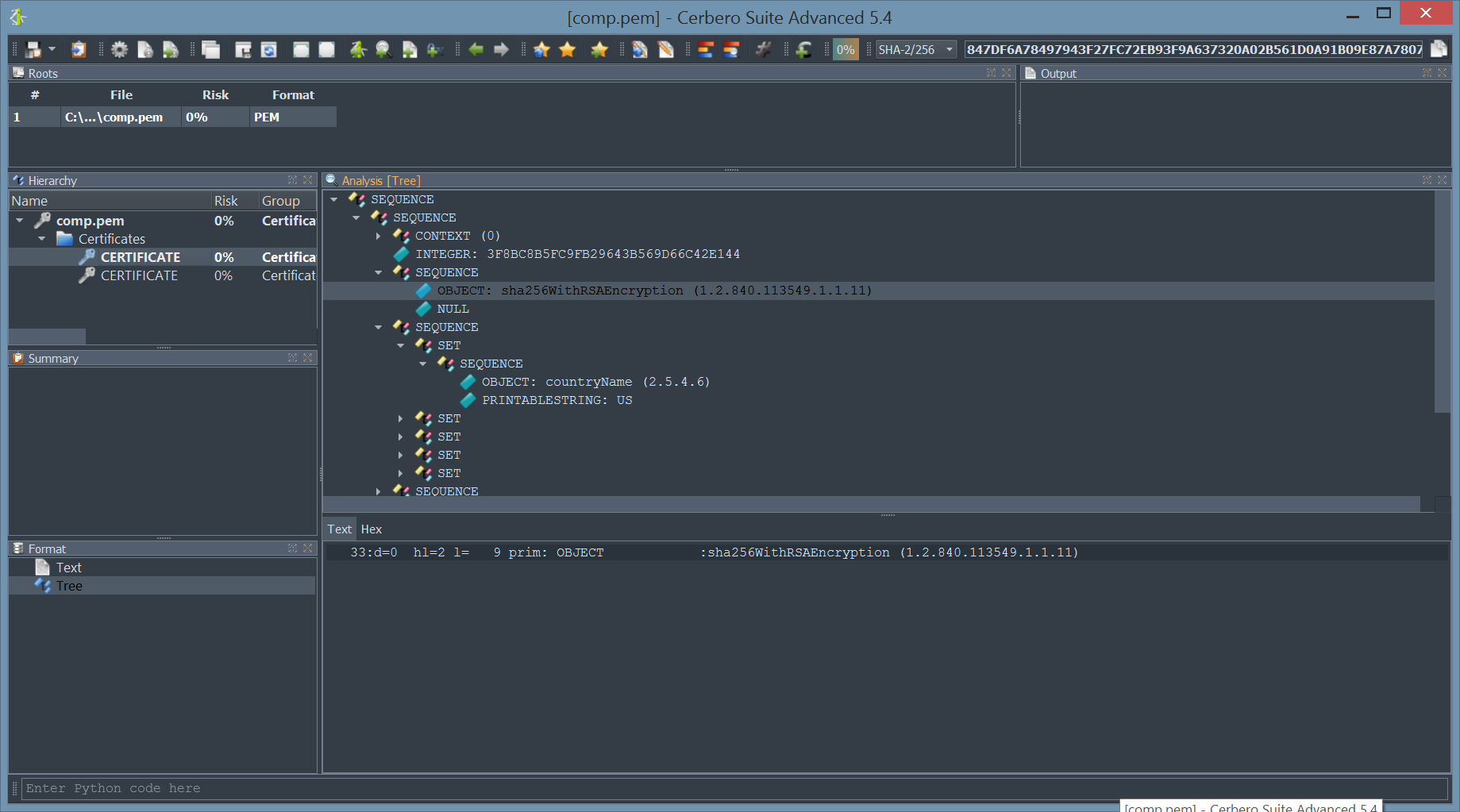
You can inspect all types of certificates, including X509, PKCS7 and PKCS12.
We have also exposed the code to our Python SDK in order to make the programmatic parsing of certificates a simple task.
You can read more about the topic in our dedicated post.
Command Line Improvements
We’ve made various improvements to command line support, the most interesting among them is the addition of command line I/O on Windows.
On Windows running scripts with the ‘-c’ argument results in not being able to see the stdout output. The reason for this is that the cerpro executable is built as a GUI application and therefore is not attached to a terminal.
To overcome this limitation we have added a launcher on Windows called “cerpro_console.exe”.
For example:
cerpro_console.exe -e "t=input('Input a string: ');print(t)"
The code asks the user to input a string and prints it back.
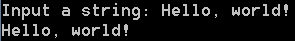
Of course, the cerpro_console executable can be used to launch any functionality of Cerbero Suite which supports console mode (‘-c’).
For example the following command prints out the command-line help to stdout:
cerpro_console.exe -h
You can read about all the improvements we’ve made in our dedicated post.
Command Line Scripting & Package Management SDK Documentation
We have released the official SDK documentation for command line scripting and package management.
Improved SDK Documentation
We have improved the visualization of the SDK documentation by adding tables which sum up the contents of modules and classes.
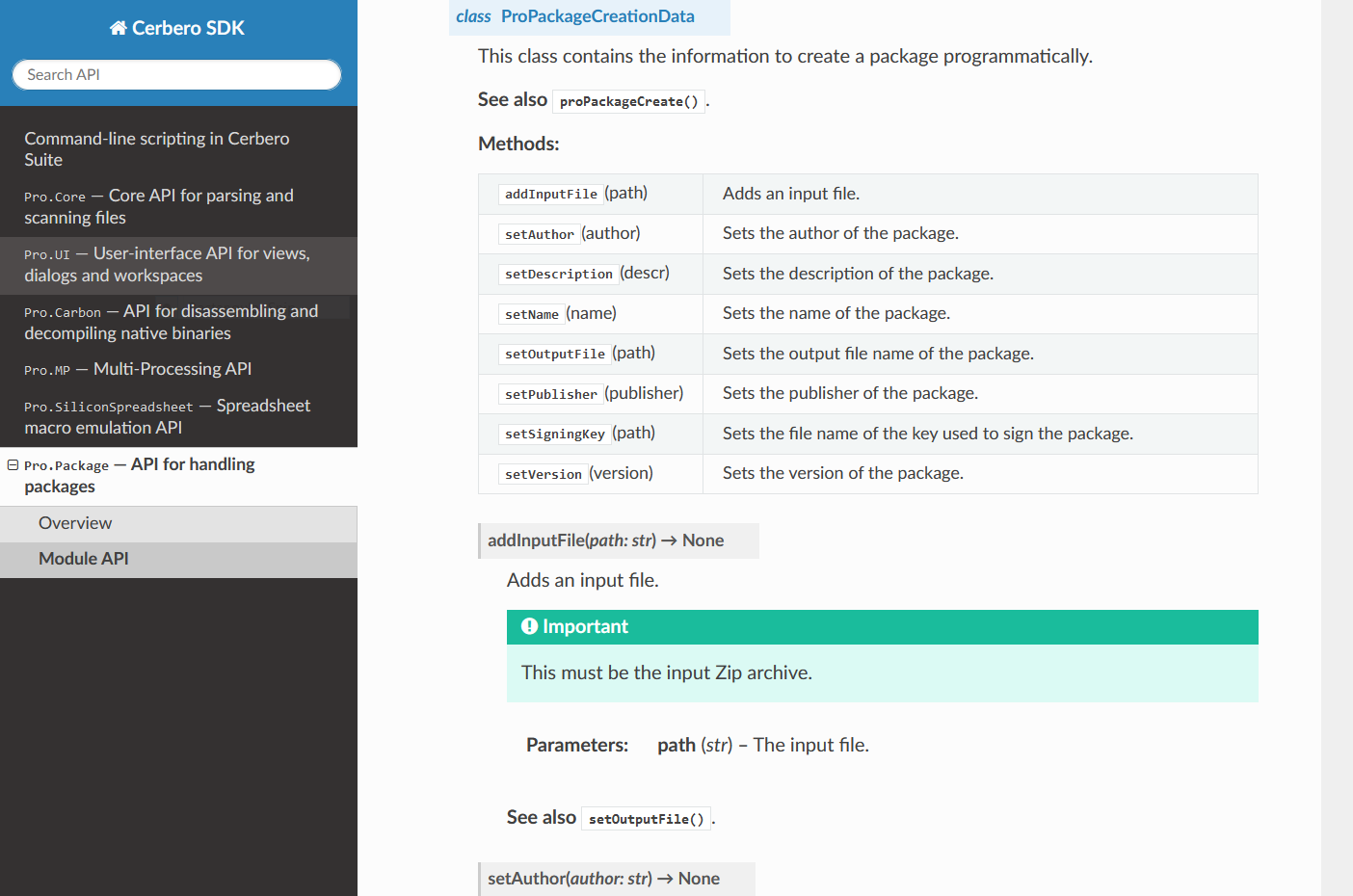
This makes it quicker to grasp the contents of an object.
We have also made other minor improvements and fixed a few bugs.