In the previous post we’ve seen a brief introduction of how hooks work. If you haven’t read that post, you’re encouraged to do so in order to understand this one. What we’re going to do in this post is something practical: verifying the XML correctness of PE manifests contained in executables in the Windows directory.
The hook INI entry:
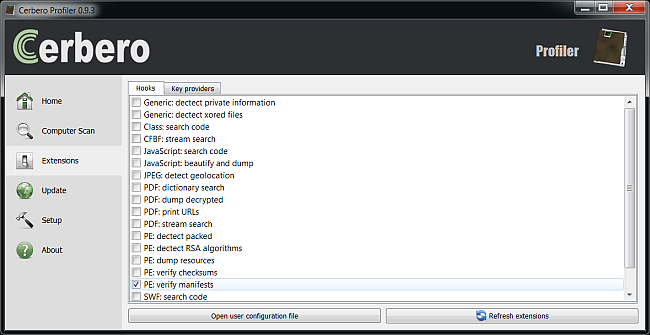
[PE: verify manifests]
file = pe_hooks.py
scanned = detectBrokenManifest
mode = batch
formats = PE And the python code:
from Pro.Core import *
from Pro.PE import *
def detectBrokenManifest(sp, ud):
sp.exclude()
pe = sp.getObject()
it = pe.ResourceIterator()
if it.MoveToRoot(RES_TYPE_CONFIGURATION_FILES) == False:
return
while it.Next() and it.RootName() == RES_TYPE_CONFIGURATION_FILES:
s = it.Data()
offs = pe.RvaToOffset(s.Num(0)) # same as s.Num("OffsetToData")
sz = s.Num(1) # same as s.Num("Size")
if offs == INVALID_OFFSET or sz == 0:
continue
bytes = pe.Read(offs, sz)
xml = NTXml()
if xml.parse(bytes) != NTXml_ErrNone:
sp.include()
break That’s it!
What the code above does is to ask the PE object for a resource iterator. This class, as our customers can observe from the SDK documentation, is capable of both iterating and moving to a specific resource directory or item. Thus, first it moves to the RES_TYPE_CONFIGURATION_FILES directory and then goes through all its items. If the XML parsing does fail, then the file is included in our final report.
So let’s proceed and do the actual scan. First we need to activate the extension from the extensions view:
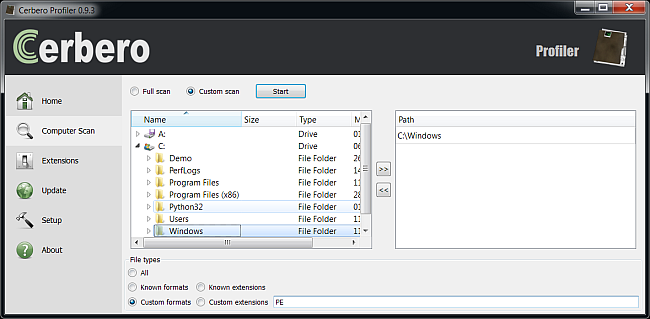
Then we need to specify the Windows directory as our scan directory and the kind of file format we’re interested scanning (PE).
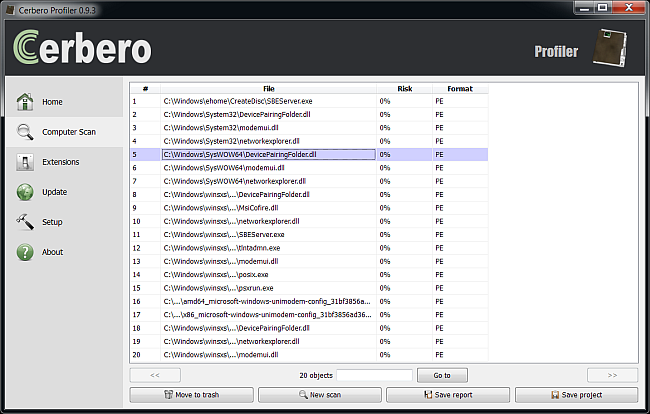
Let’s wait for the scan to complete and we’ll get the final results.
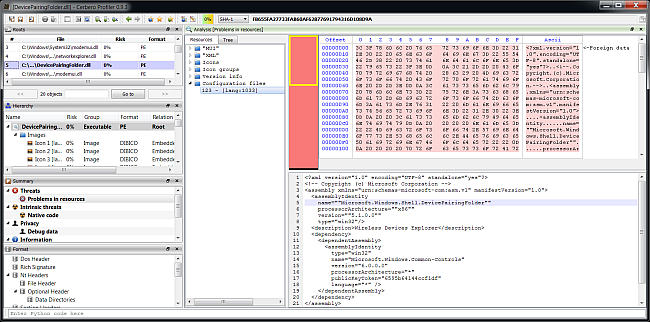
So seems these file have a problem with their manifests. Let’s open one and go to its manifest resources:
(if the XML is missing new-lines, just hit “Run action (Ctrl+R)->XML indenter”)
<?xml version="1.0" encoding="UTF-8" standalone="yes"?>
<!-- Copyright (c) Microsoft Corporation -->
<assembly xmlns="urn:schemas-microsoft-com:asm.v1" manifestVersion="1.0">
<assemblyIdentity
name=""Microsoft.Windows.Shell.DevicePairingFolder""
processorArchitecture=""x86""
version=""5.1.0.0""
type="win32"/>
<description>Wireless Devices Explorer</description>
<dependency>
<dependentAssembly>
<assemblyIdentity
type="win32"
name="Microsoft.Windows.Common-Controls"
version="6.0.0.0"
processorArchitecture="*"
publicKeyToken="6595b64144ccf1df"
language="*" />
</dependentAssembly>
</dependency>
</assembly> As you can see some attributes in assemblyIdentity contain double quotes. I don’t know whether this DLL has been created with Visual C++, but I do remember that this could happen when specifying manifests fields in the project configuration dialog.