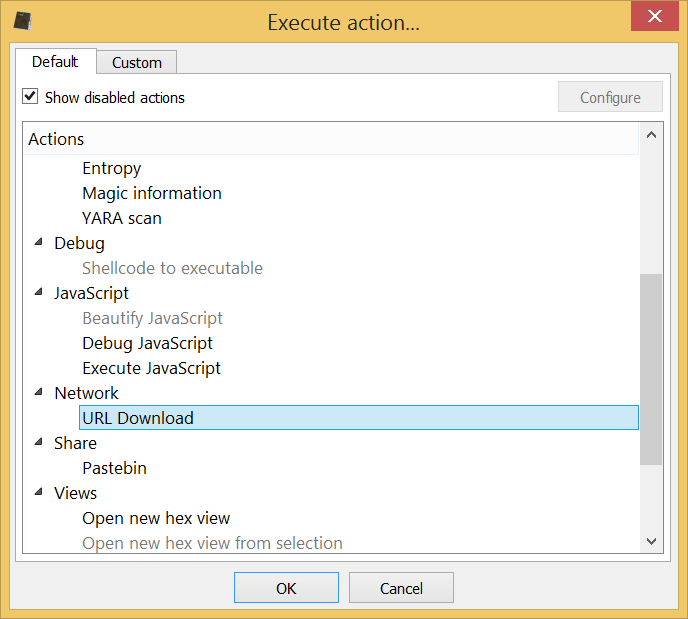
In the upcoming version of Profiler Advanced we have introduced a new useful action, namely the URL Download action.
Many times in previous posts we have analyzed some malware which at the end of its shellcode ended up downloading a binary from the internet and executing it. We thought it would be nice to give our users the possibility to anonymously download content from the internet in order to continue the analysis.
One way to download anonymously from the internet using our new action is via Tor. On Windows it’s sufficient to install and run the Tor browser.
The action will automatically try to load a possible URL from the current context, be it hex view, text editor or clipboard.
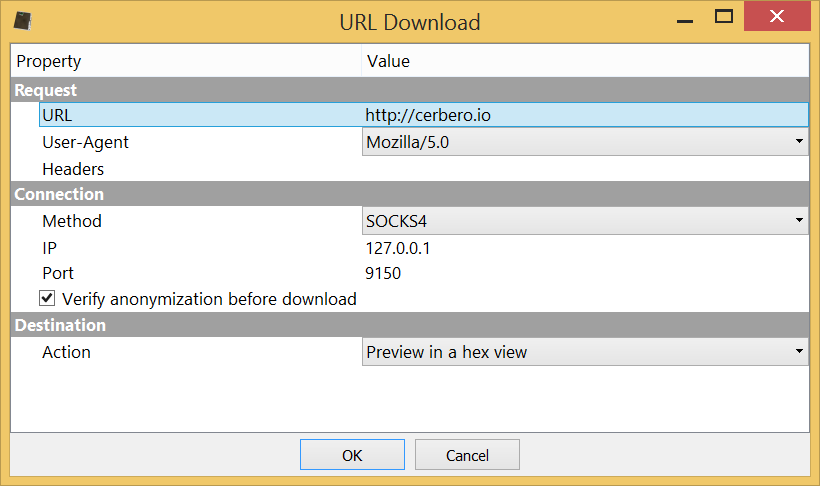
The dialog of the action offers different configuration settings: headers, user agent, download method (direct, SOCKS4, SOCKS5) along with relative parameters, anonymity check and also what to do with the downloaded content (either download it to file or preview it in a hex view).
Since we’re using Tor, we can either use the SOCKS4 or 5 method. We specify our local address and the port onto which Tor is listening for connections, in this case 9150.
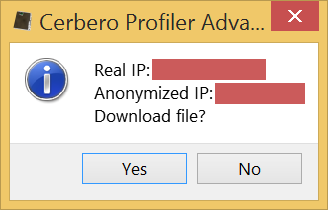
The anonymity check is performed against our own https secured server: it will fetch the real IP by connecting to our server and then try to connect again via the secure method.
When the anonymity verification option is selected, before downloading the payload, we are asked by a message box to confirm the success of the anonymization.
If we click on OK, Profiler will then fetch the actual payload.
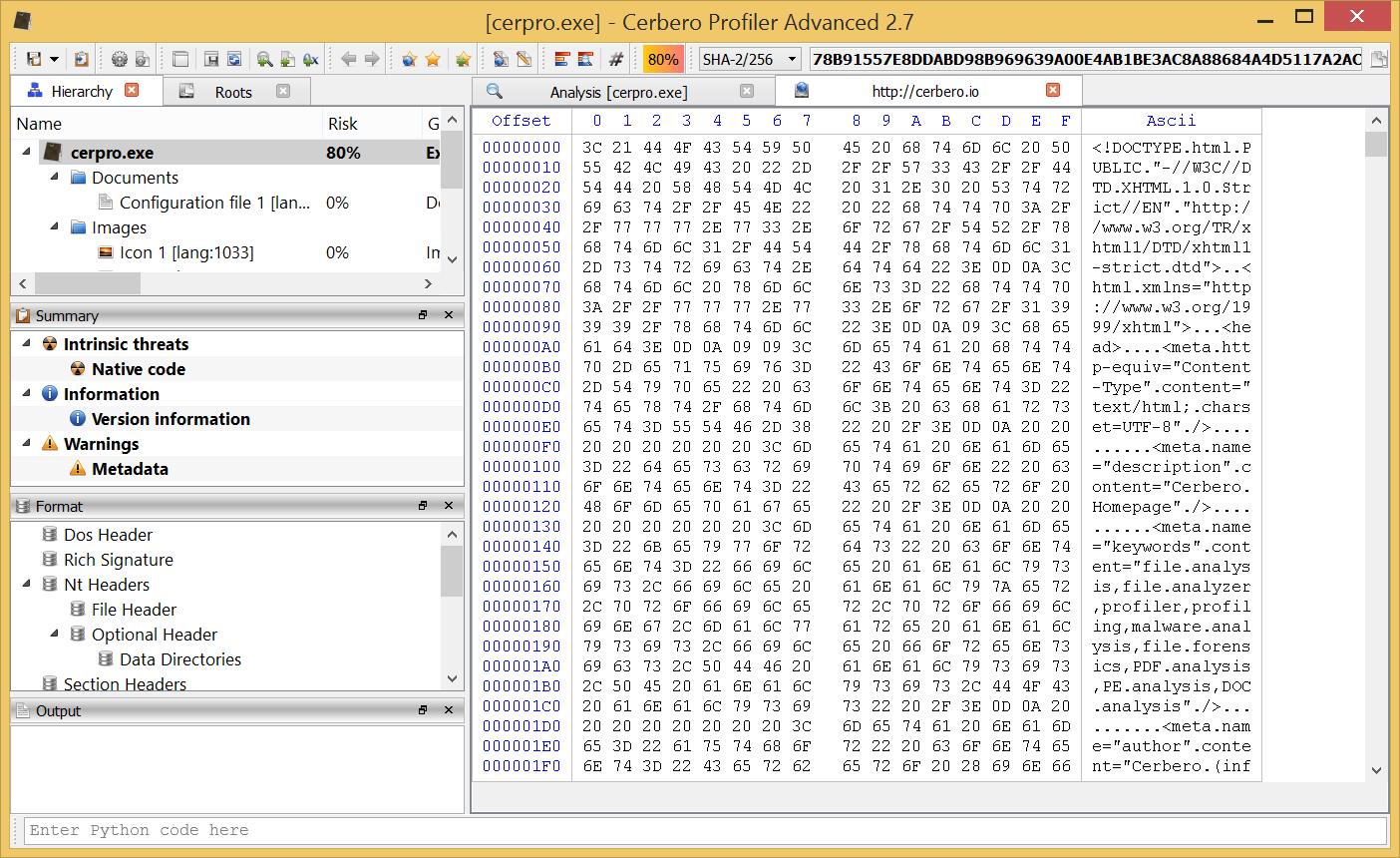
If we chose to preview the content in a hex view and decide later that we want to save it on disk, we can do so by selecting all the bytes (Ctrl+A) and then copying them into a new file via the copy menu.