We are proud to announce the release of the YARA Rules package for all licenses of Cerbero Suite!
This package is designed to be the ultimate toolkit for downloading, scanning with, creating, editing, and testing YARA rules.
![]()
YARA, an essential tool in the fight against malware, allows for the creation of descriptions to match patterns across various file types. Recognizing the importance of YARA in digital forensics and malware analysis, we have developed a comprehensive suite of tools designed to enhance the YARA rule management process.
The YARA Rules package for Cerbero Suite includes an array of features aimed at streamlining the workflow associated with YARA rules. Whether you’re downloading rules from public repositories, scanning files for matches, creating rules tailored to the latest malware threats, editing existing rules to improve accuracy, or rigorously testing rules to ensure effectiveness, this package has everything you need.
Our goal is to provide Cerbero Suite users with a powerful, efficient, and user-friendly set of tools that empowers them to use YARA rules more effectively than ever before. Whether you are a seasoned malware analyst or just starting out in the field of cybersecurity, the YARA Rules package is designed to enhance your analysis capabilities and streamline your workflows.
We invite you in this blog post to explore the full potential of the YARA Rules package and discover how it can enhance your malware analysis and forensic investigations.
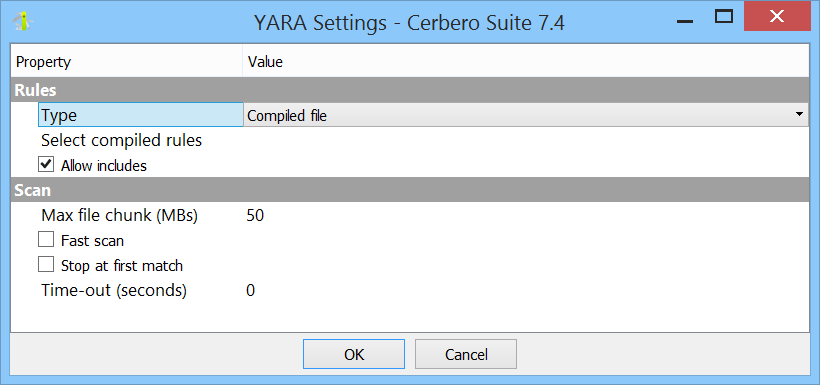
From the YARA Rules settings page, you can configure which rules you want to use for scanning files. You can specify remote Git repositories and Zip archives, as well as local files and directories.
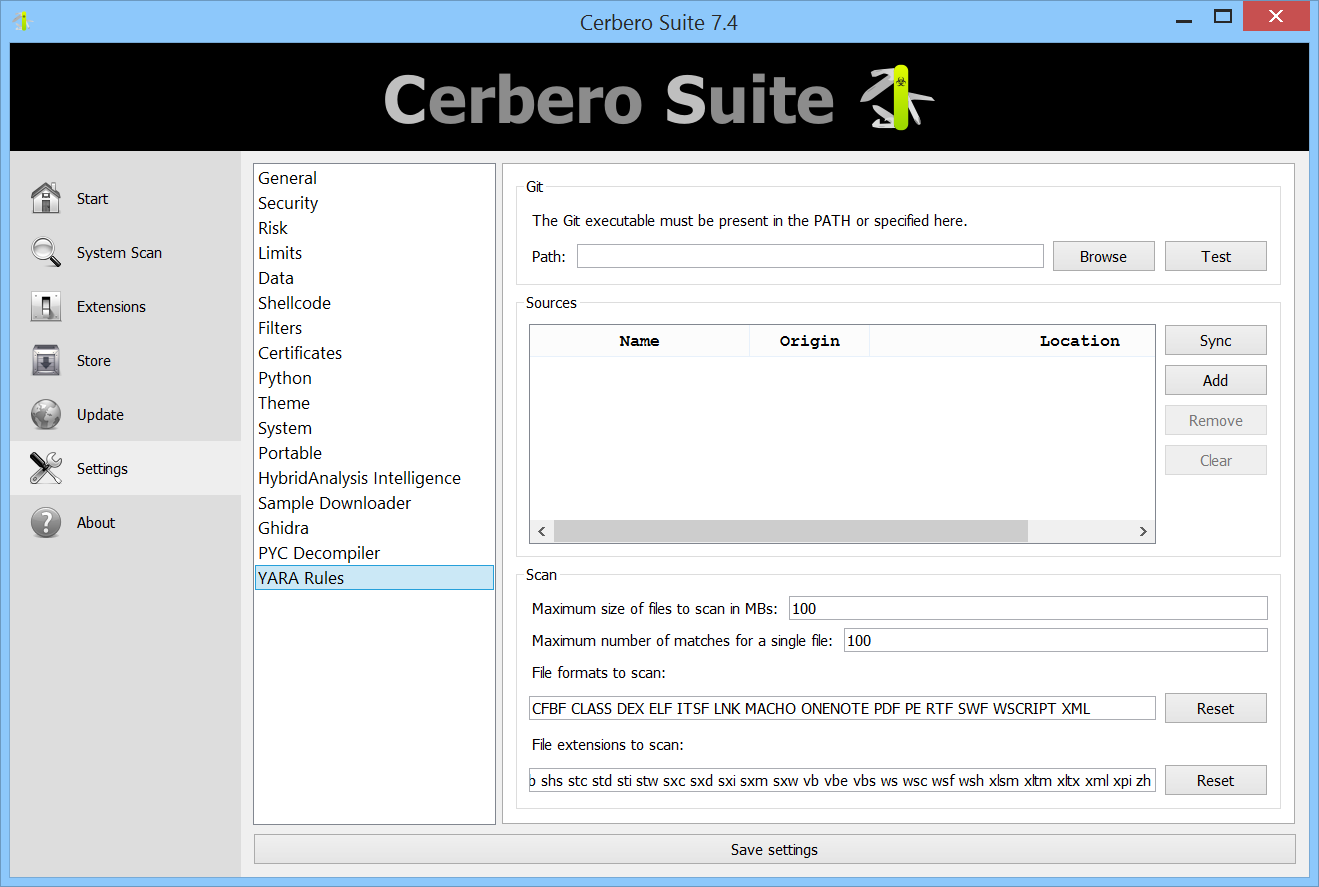
You can also configure various other settings, such as the formats and extensions that should be scanned using YARA when analyzing a file, the maximum file size and the maximum number of matches.
When adding a source, you can choose either to add one from a known list of public repositories or to add a custom source.
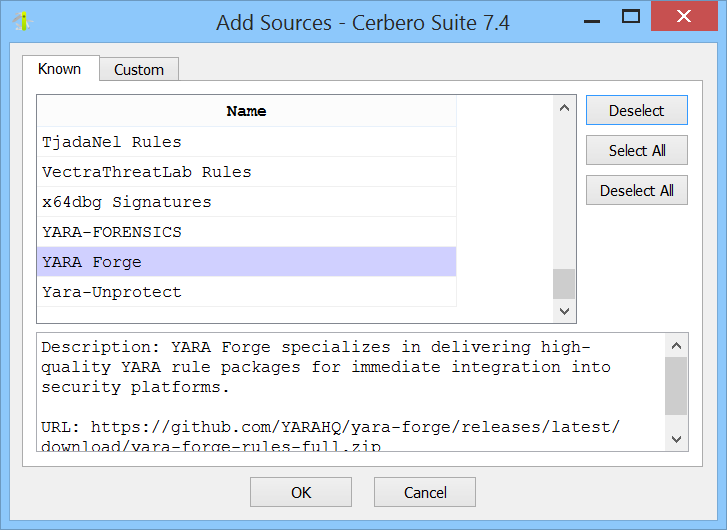
Custom sources can be local files, directories, or remote URLs to Git repositories or Zip archives.
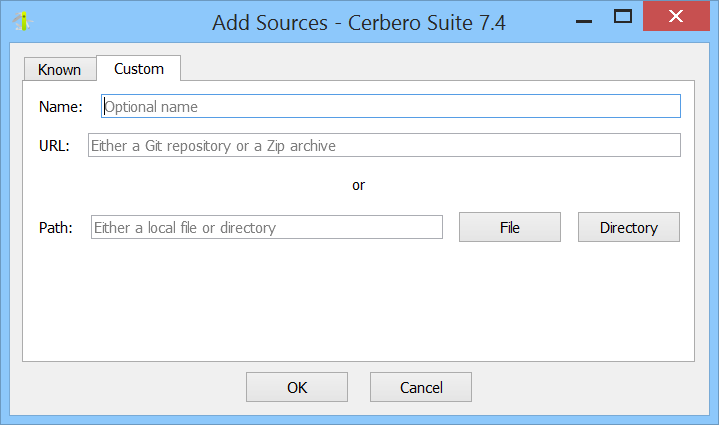
When adding a source that points to a Git repository, ensure that Git is installed on your system and available in the PATH. You can use the ‘Test’ button to verify this.
Once you have added your sources, you can click the ‘Sync’ button to download or update and compile the rules.
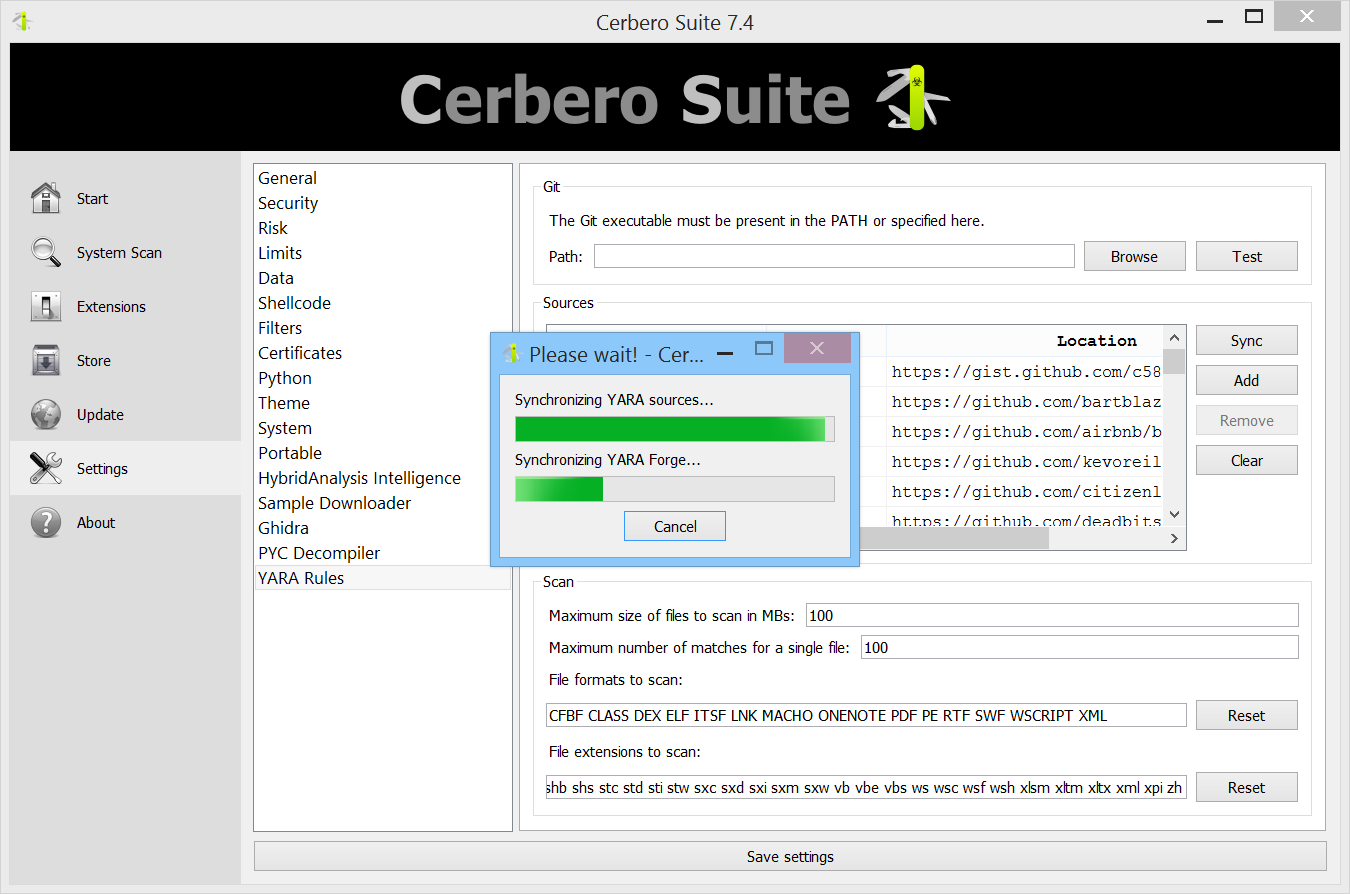
If you are only interested in using public repositories, you are all set up at this stage. Now, analyzed files will report matches with YARA rules.
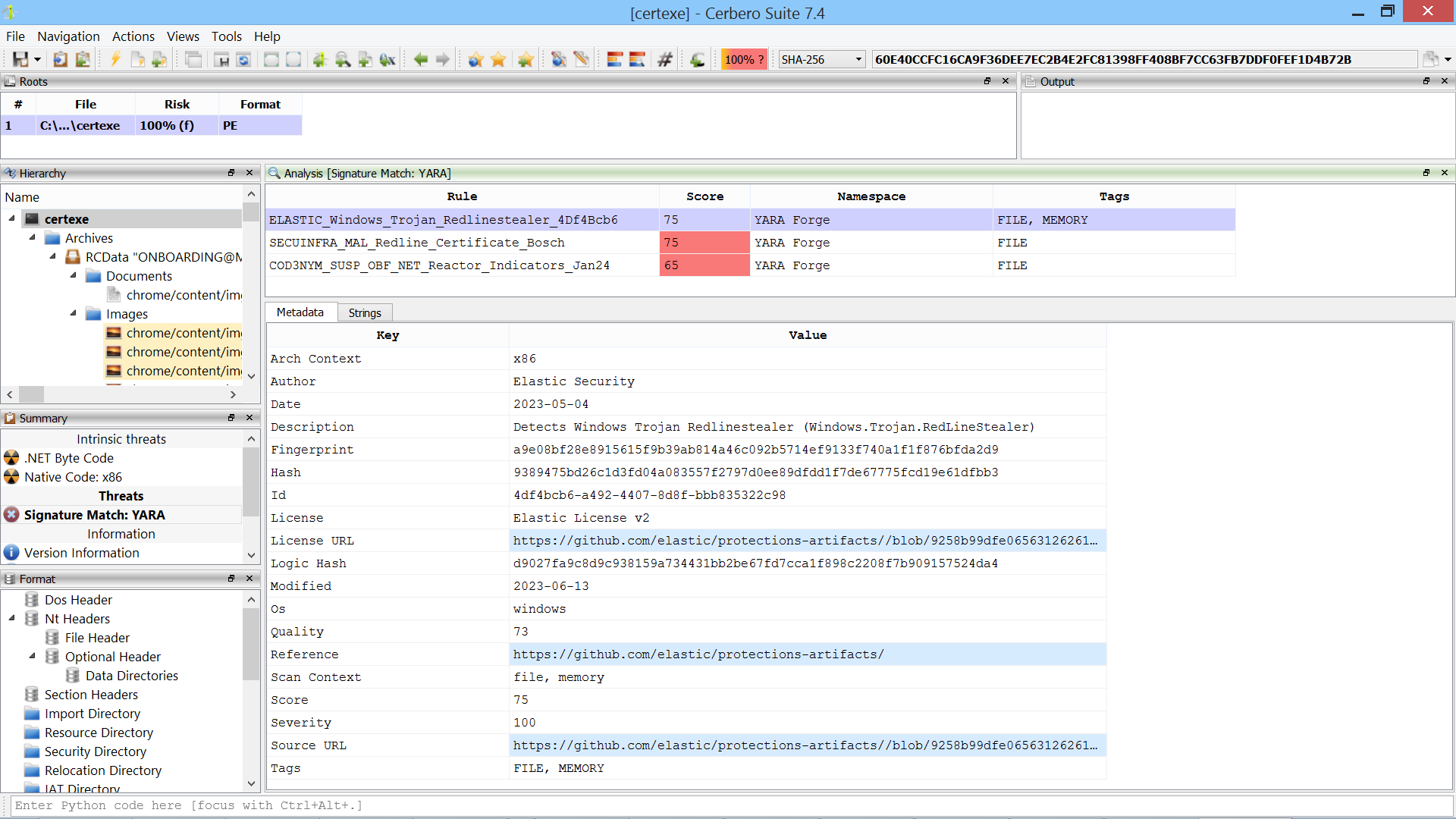
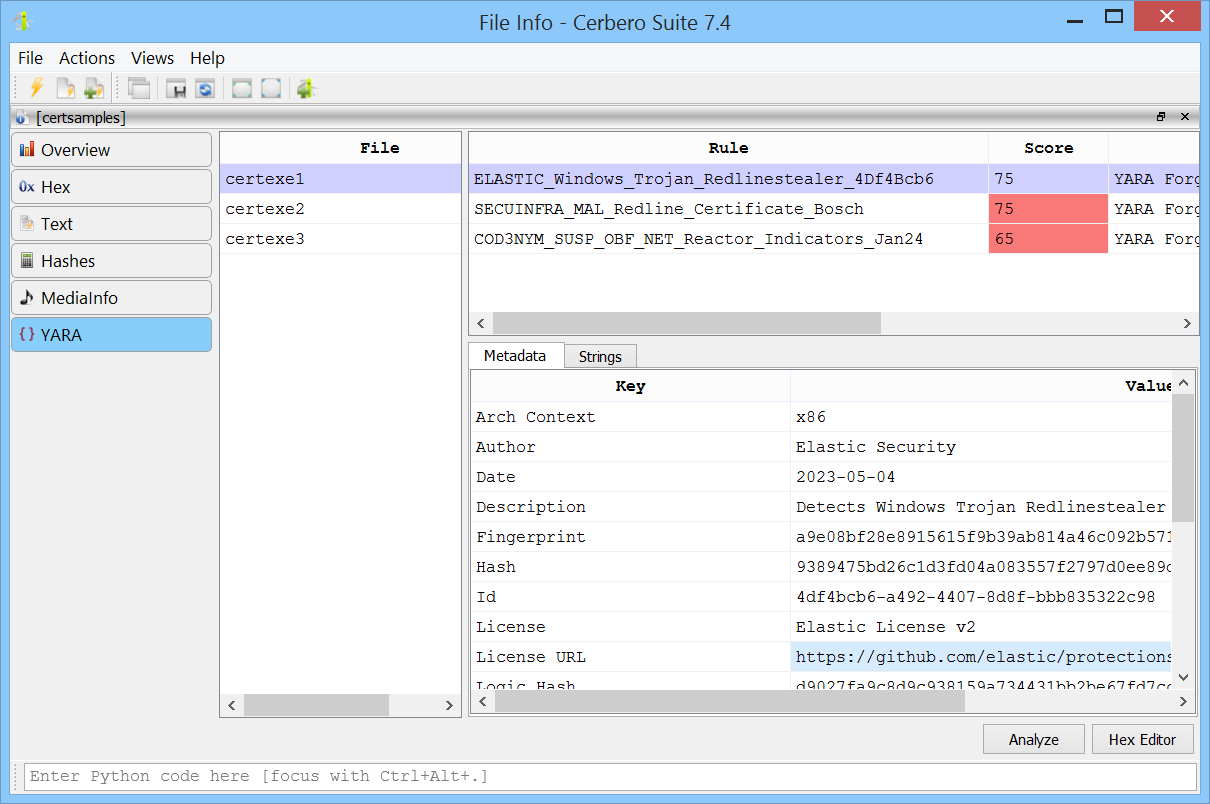
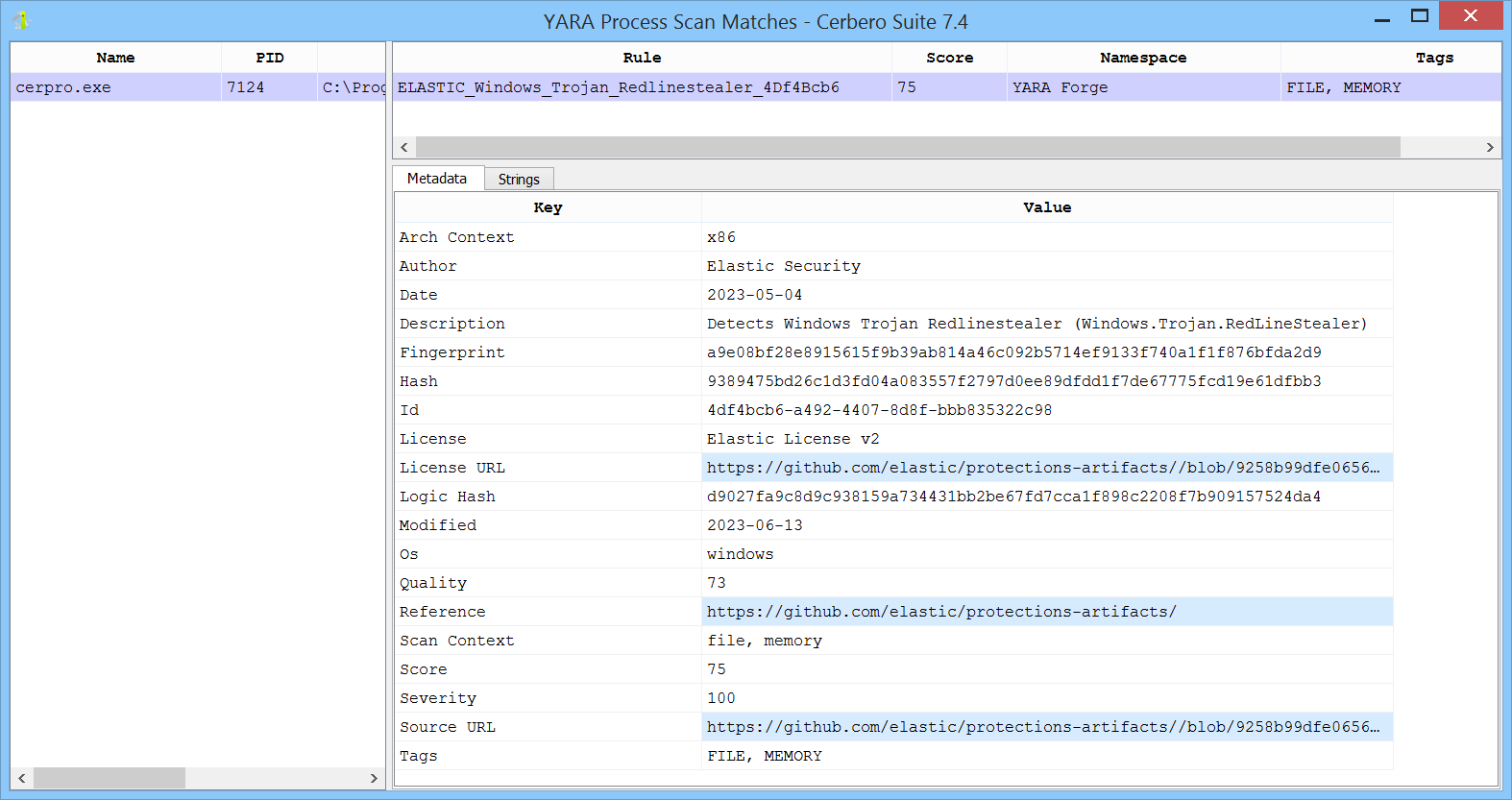
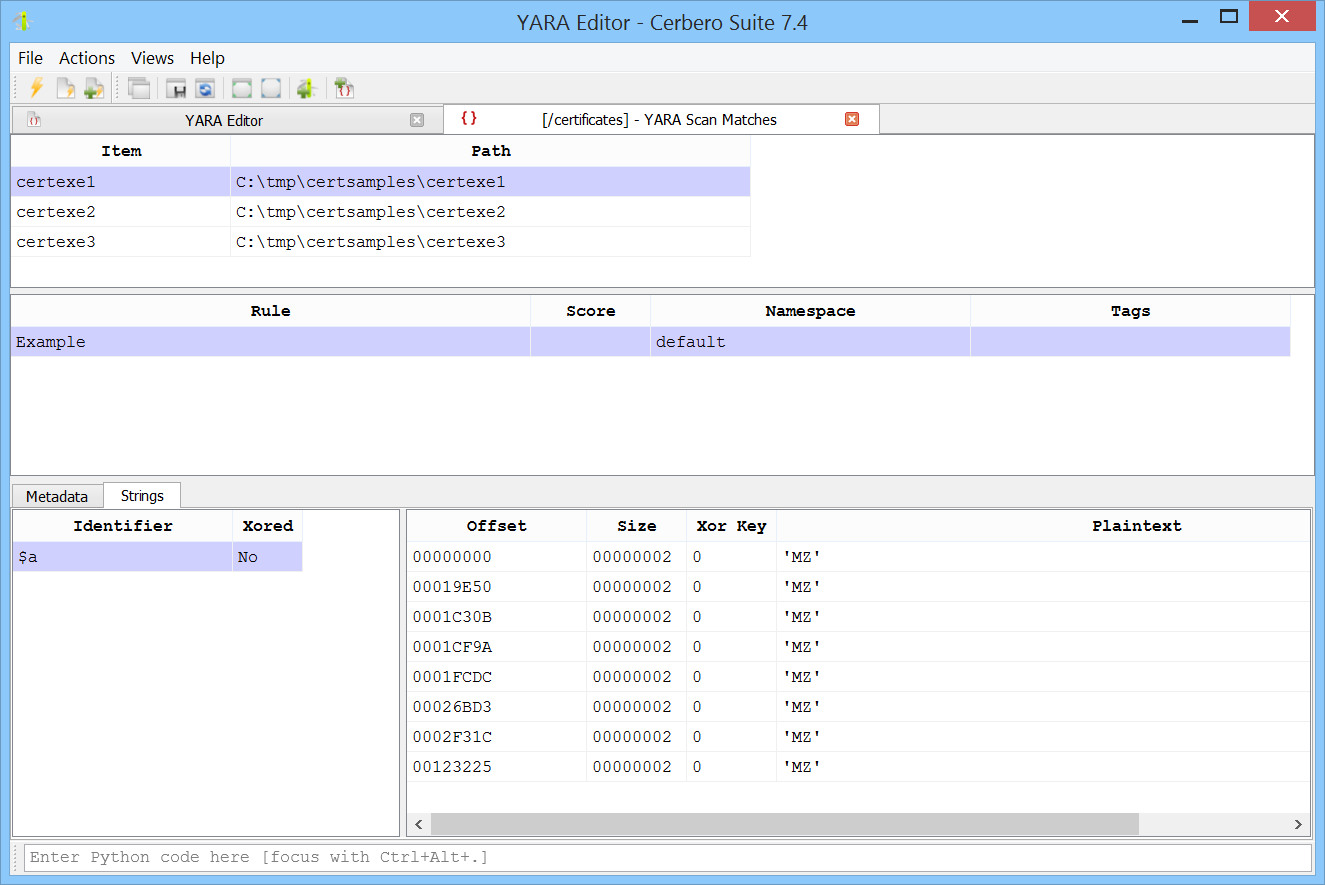
From the view displaying the matches, you can inspect the metadata and the strings for each match.
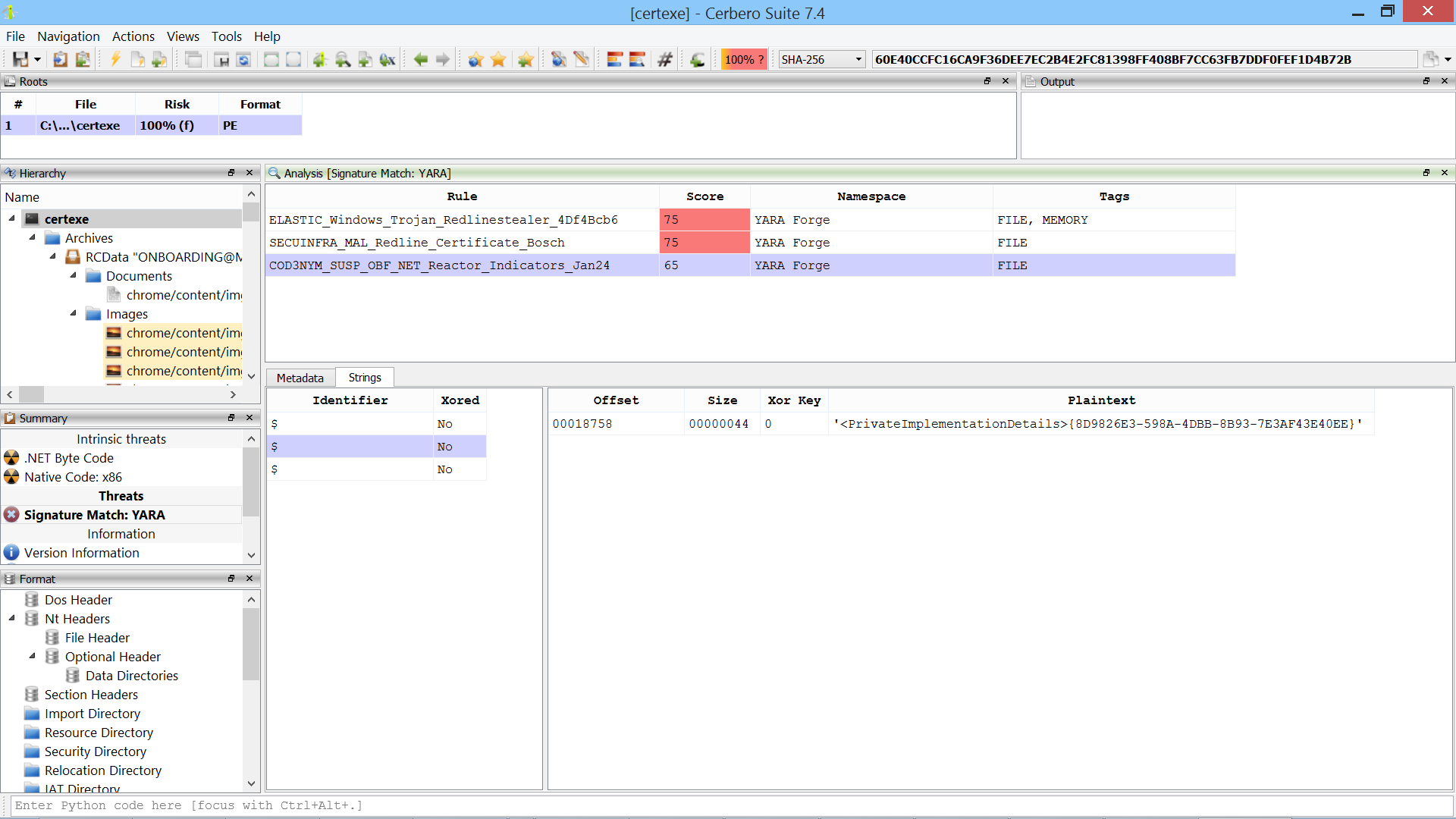
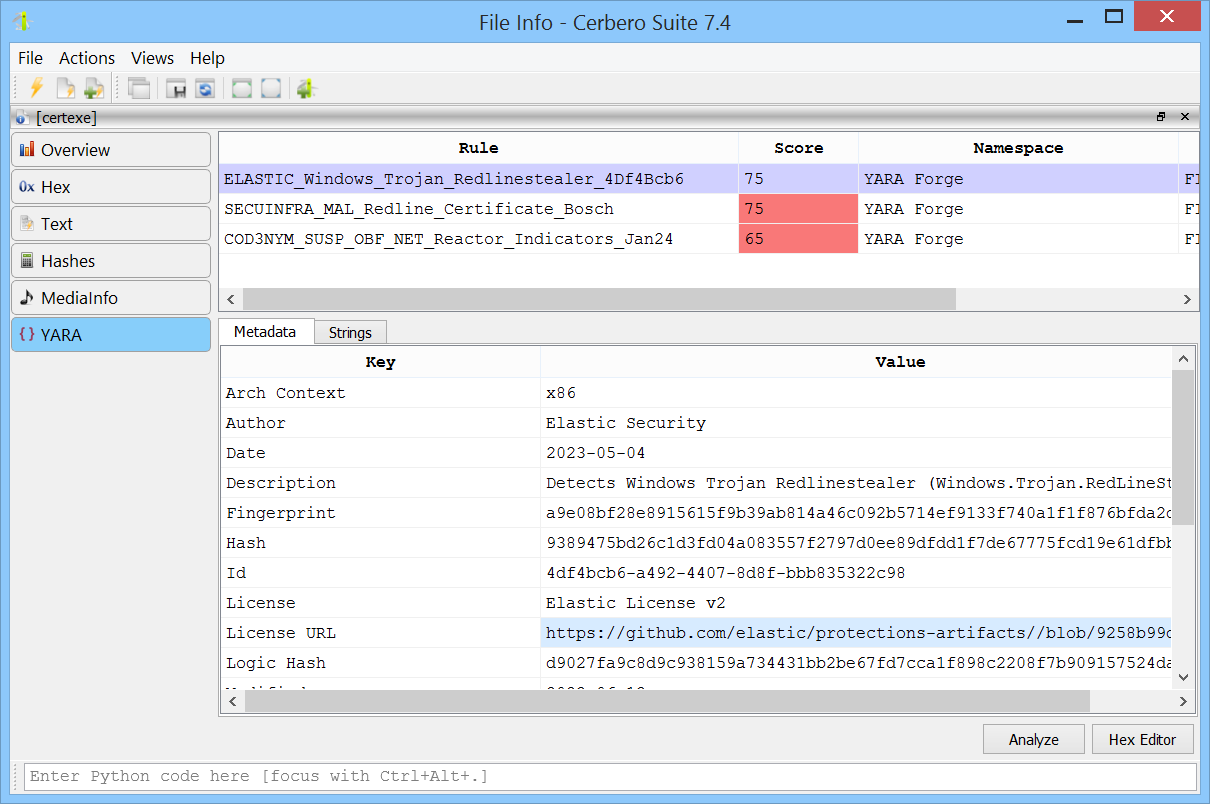
YARA matches are also accessible from the file information view.
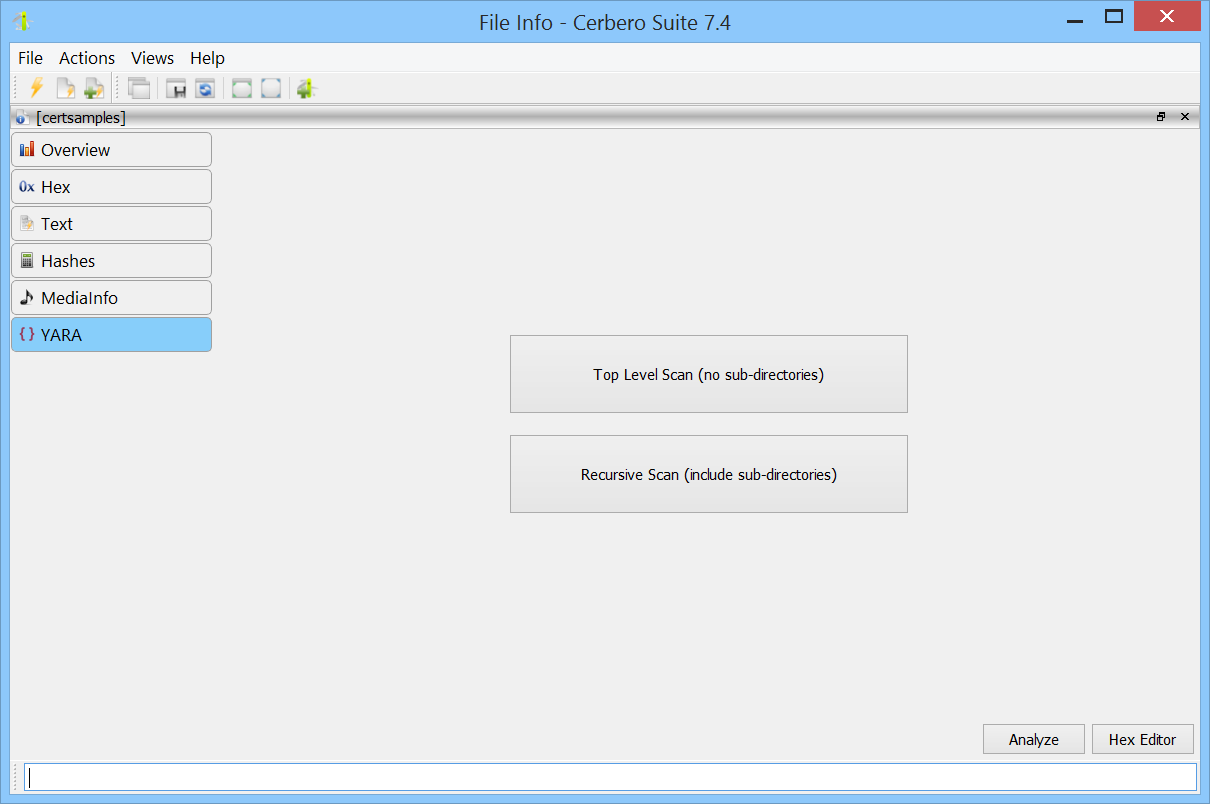
When inspecting a directory from the file information view, you have the option to perform either a top-level or a recursive scan of the directory.
Once the scan is complete, you have the ability to inspect the matches.
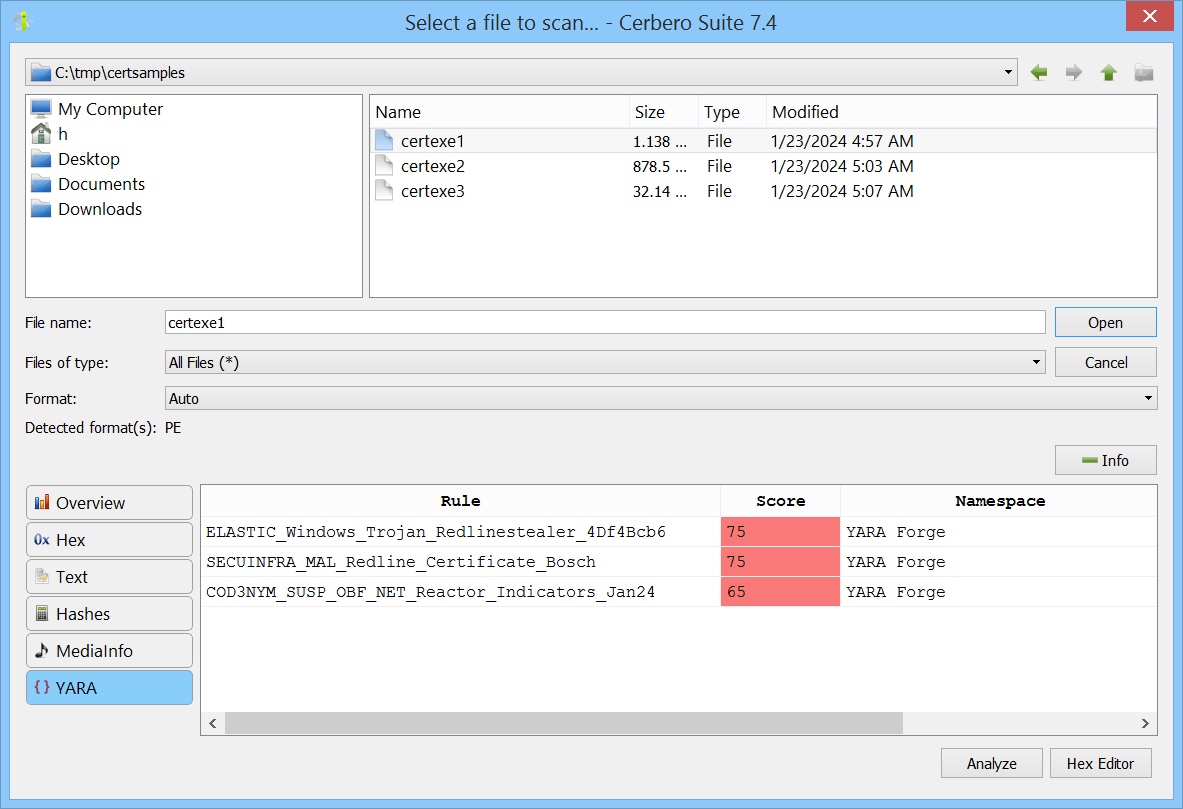
It’s worth mentioning that YARA matches are also accessible from open file dialogs, thanks to their integration with the file information view.
The YARA Rules package introduces four logic providers to the main window.
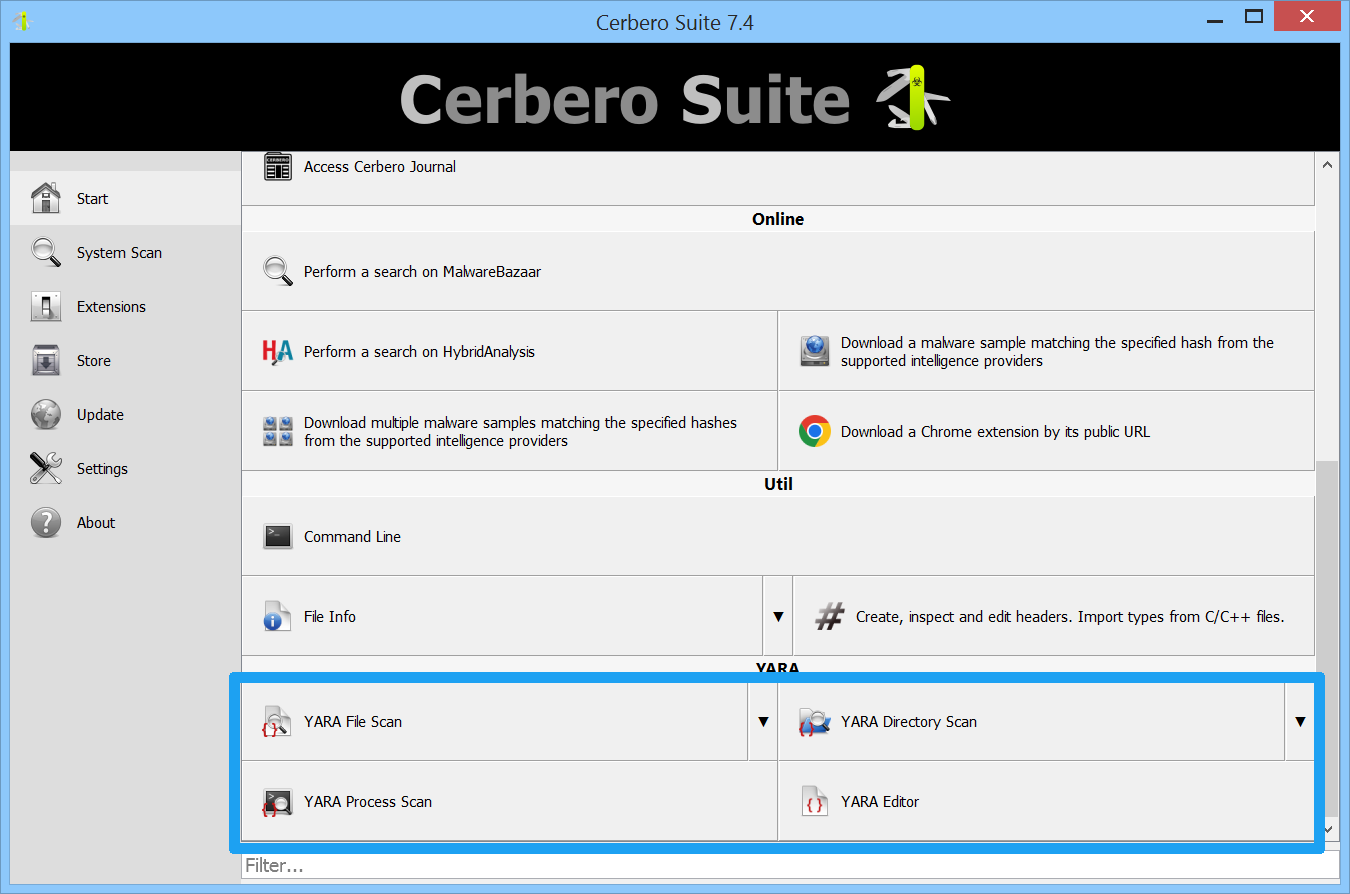
The first two, which scan a file or directory, open the YARA file information for either a file or directory. Meanwhile, the process scan functionality opens a dialog that allows you to select which processes you wish to scan.
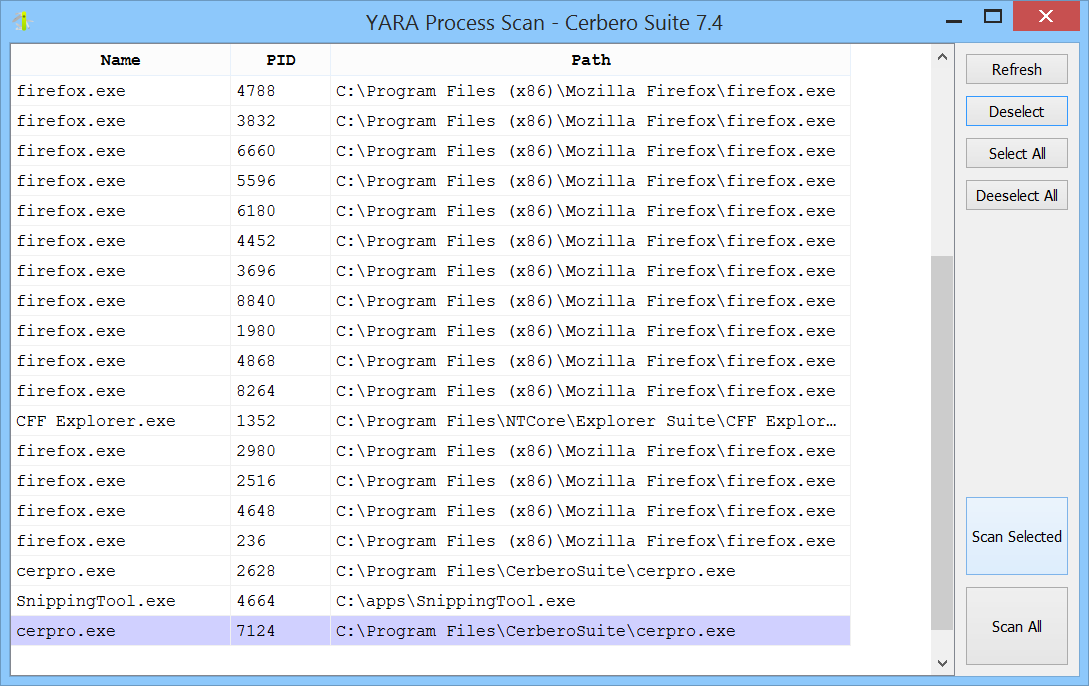
In this case, we opened a malware sample in an instance of Cerbero Suite and scanned the process, resulting in the following match.
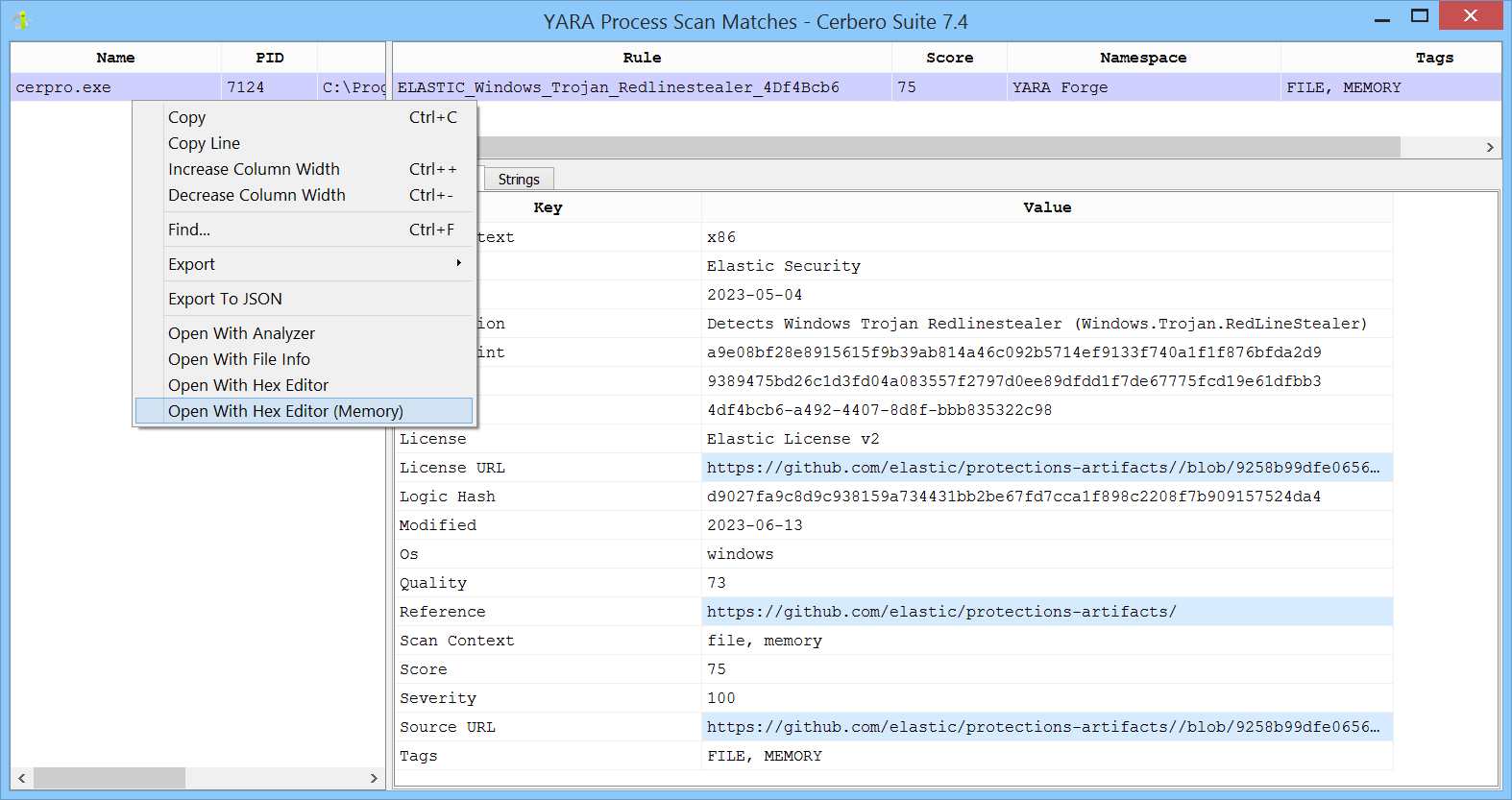
You can open the hex editor to inspect the match in memory.
Note: On Linux and macOS, launching Cerbero Suite as sudo is necessary to scan processes. On Windows, administrator rights are required to scan all system processes, not just those of the current user.
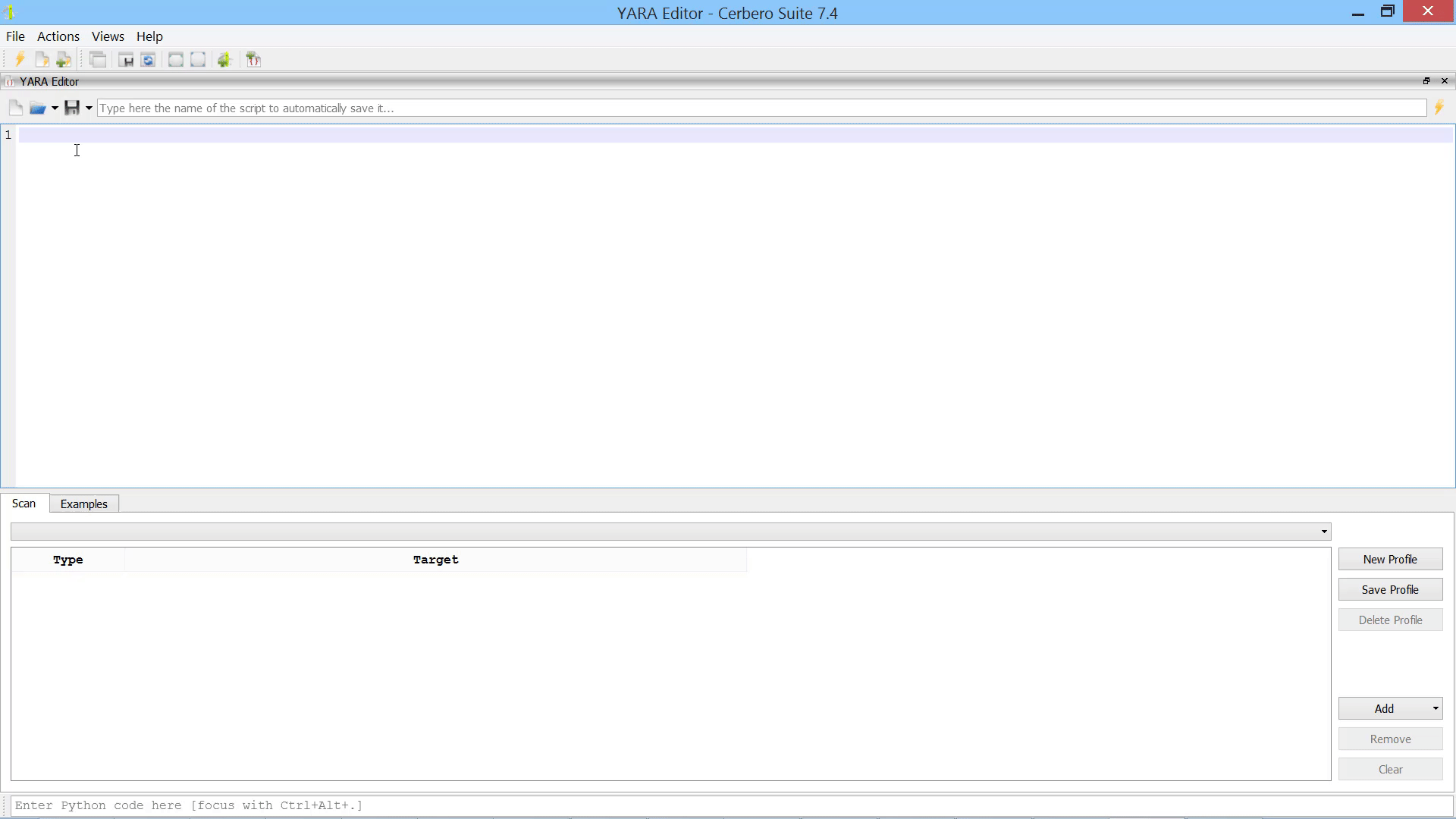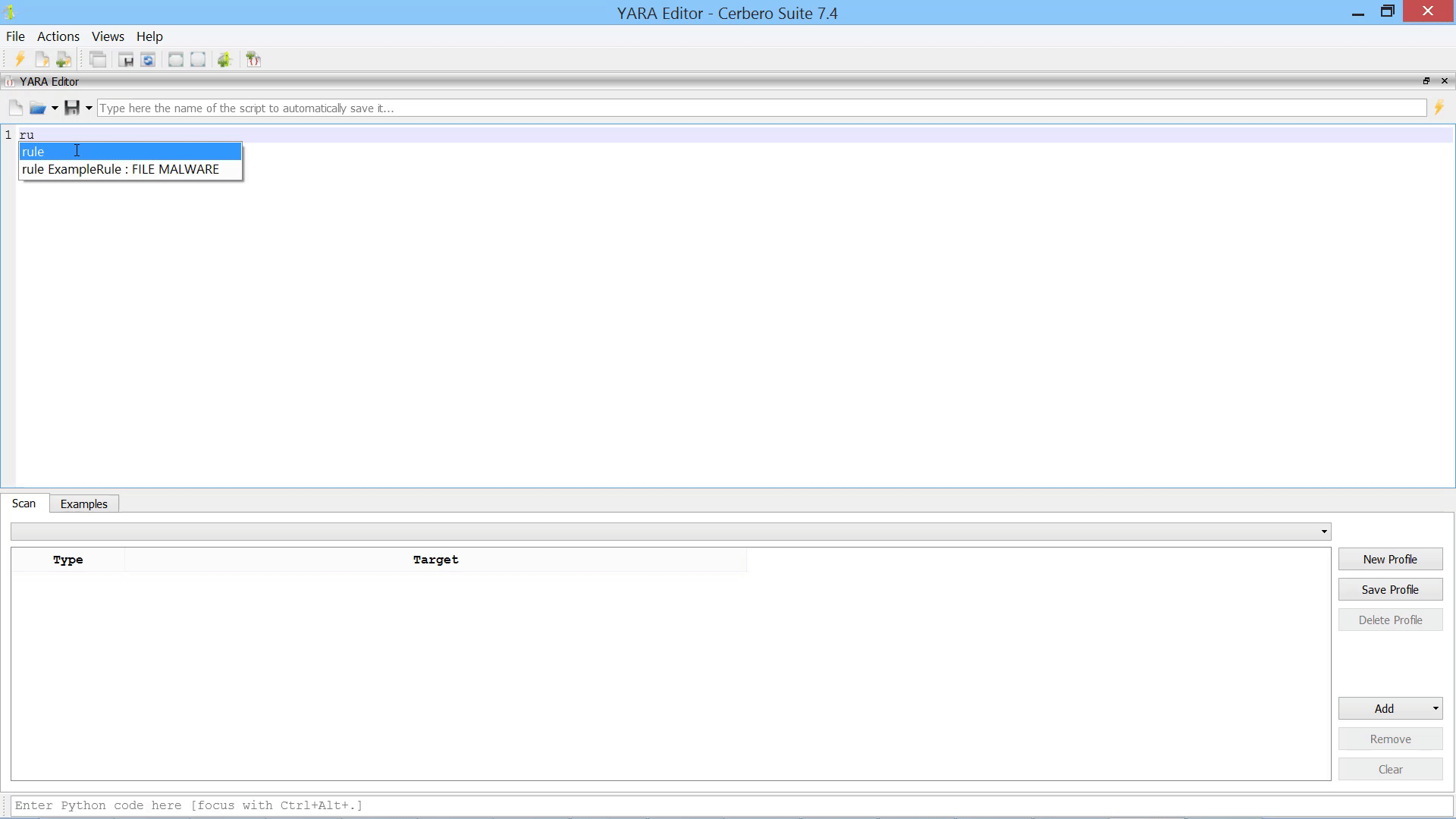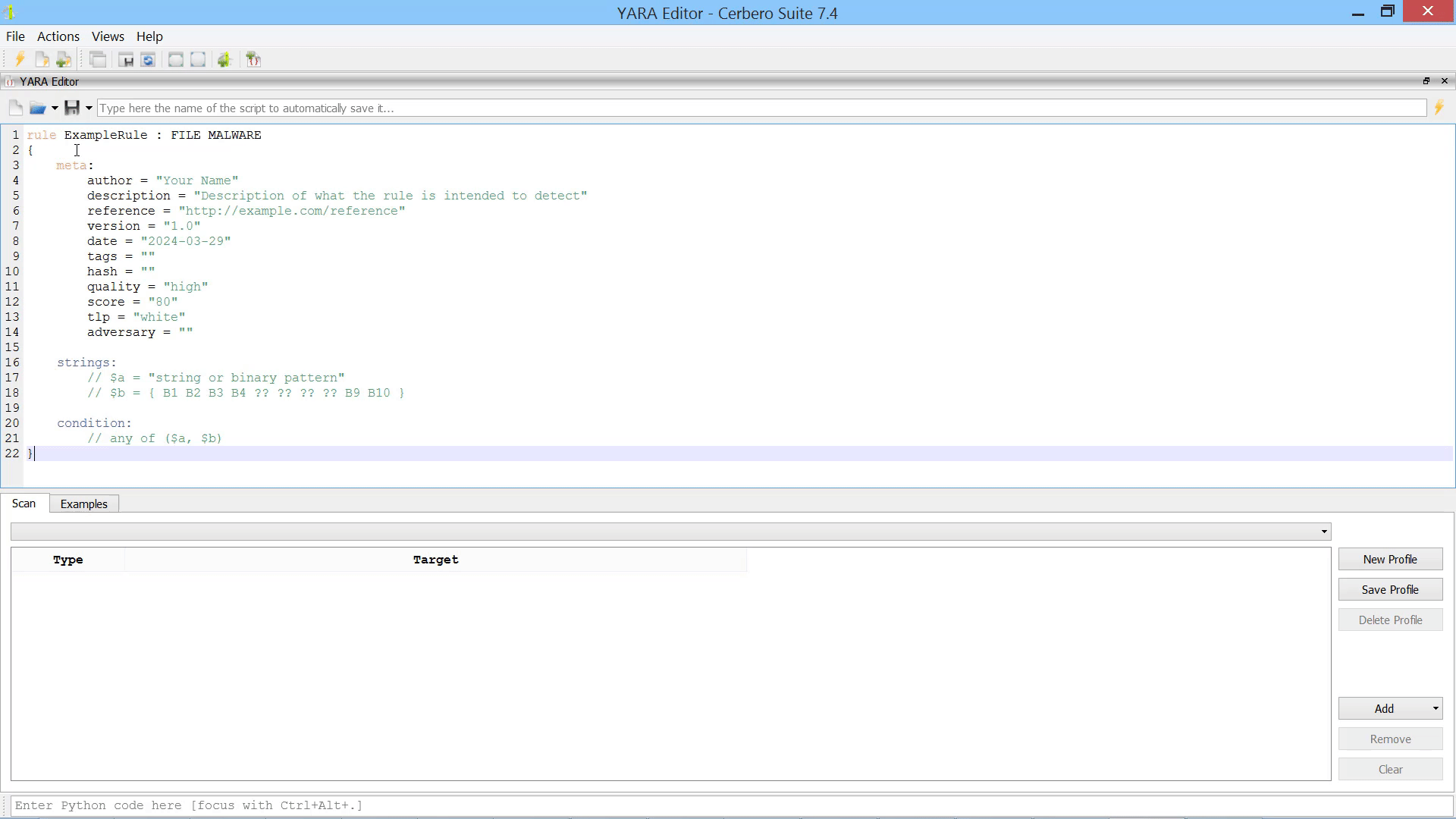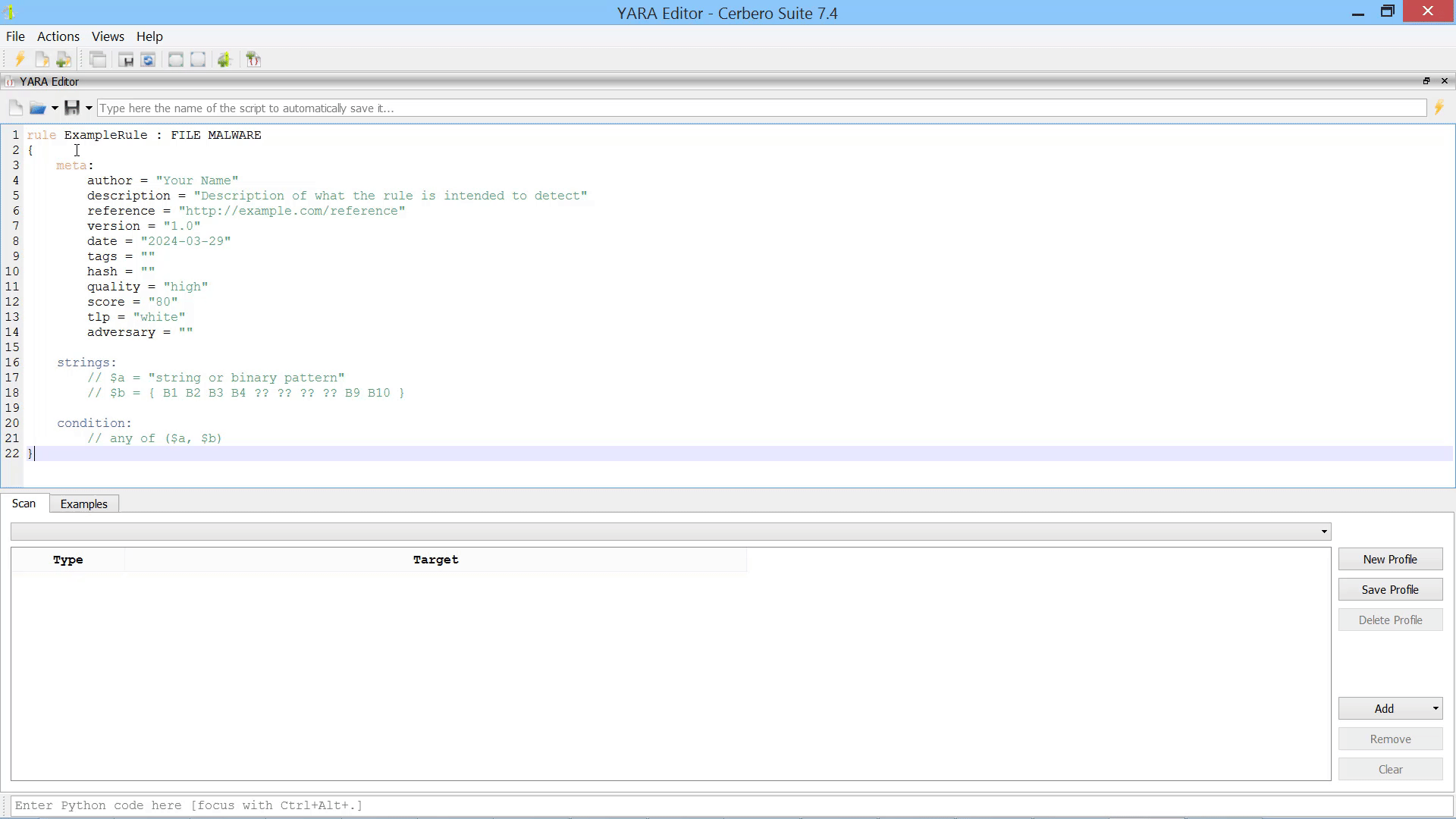
The YARA Editor provides a comprehensive workspace for creating, editing and testing YARA rules.
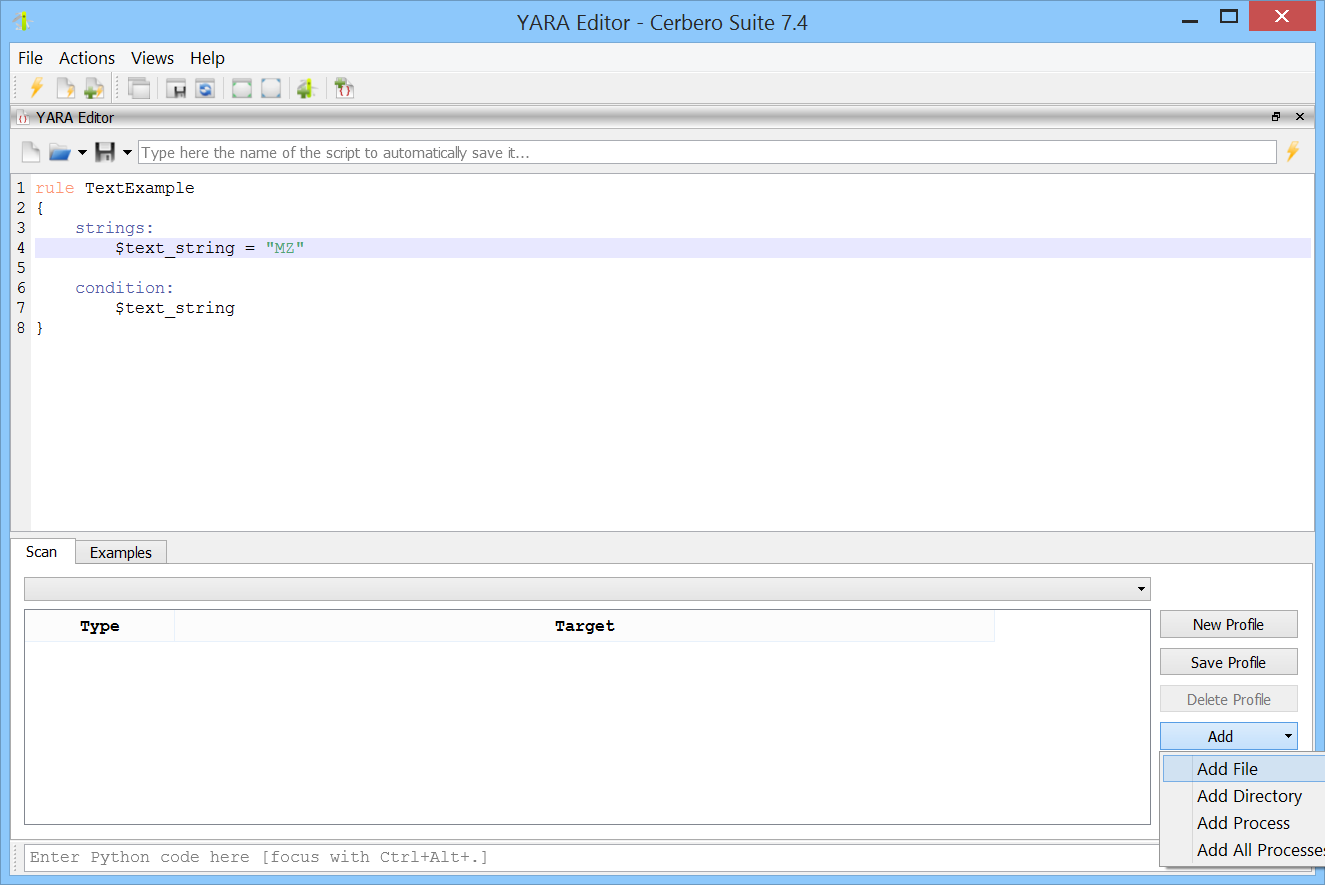
You can create various scan profiles to test different types of rules against different sets of files, directories, or processes.
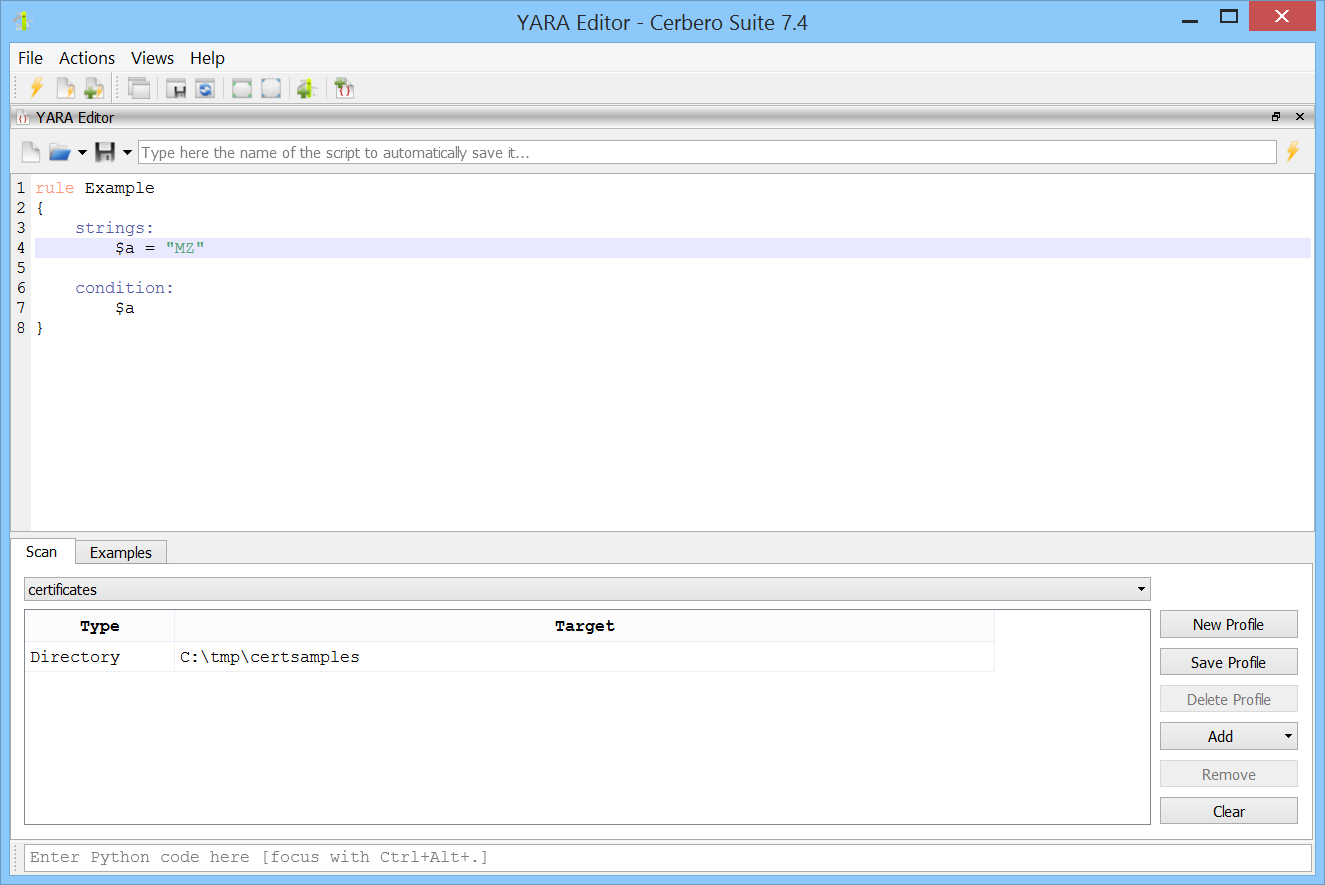
Once you execute the rule, matches are displayed upon completion of the scan.
You can also leave the scan profile empty if you just want to verify the syntax of a rule.
The editor is equipped with syntax completion.
To simplify the creation of rules, we have included rule examples that you can quickly search through and inspect.
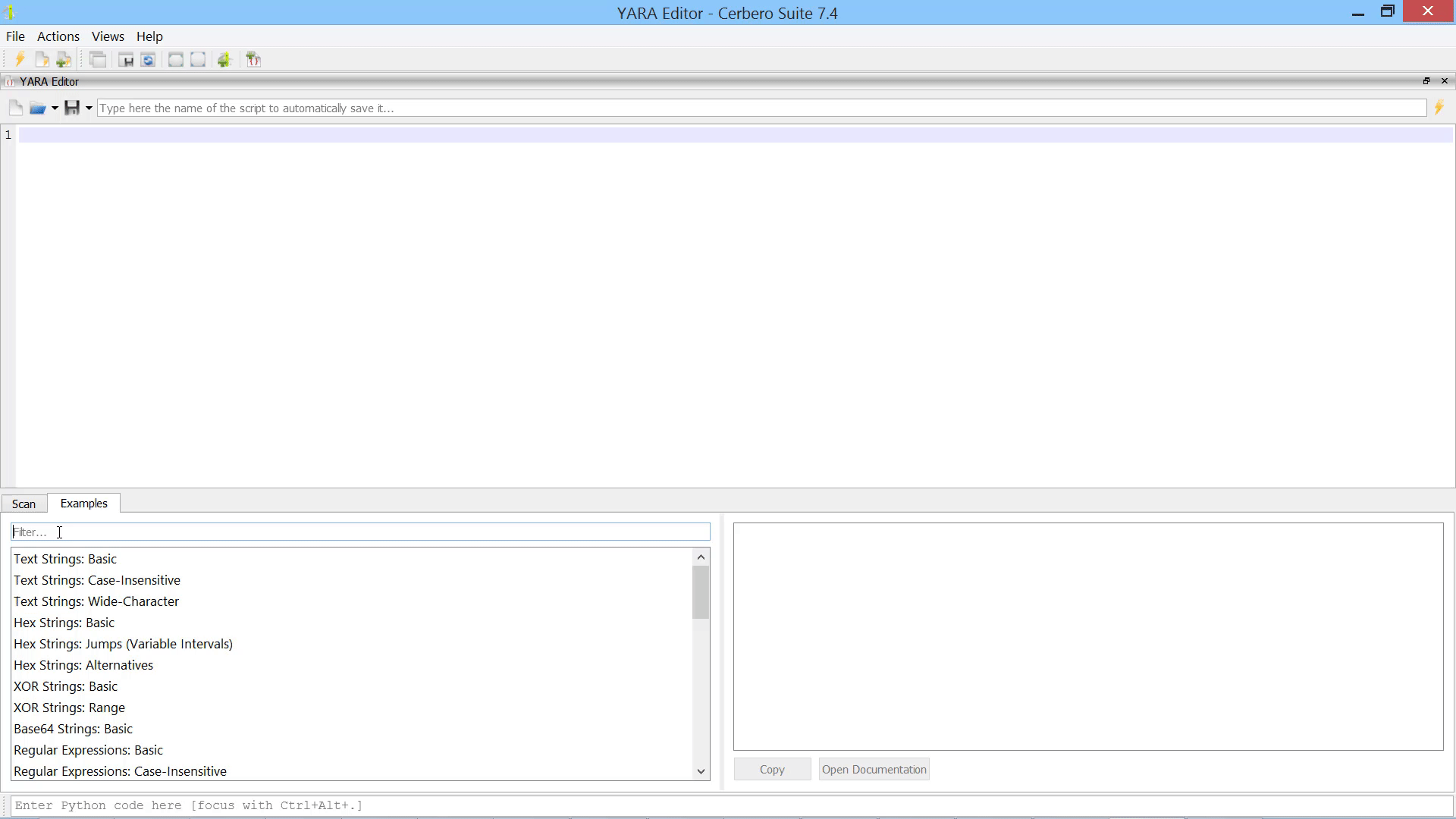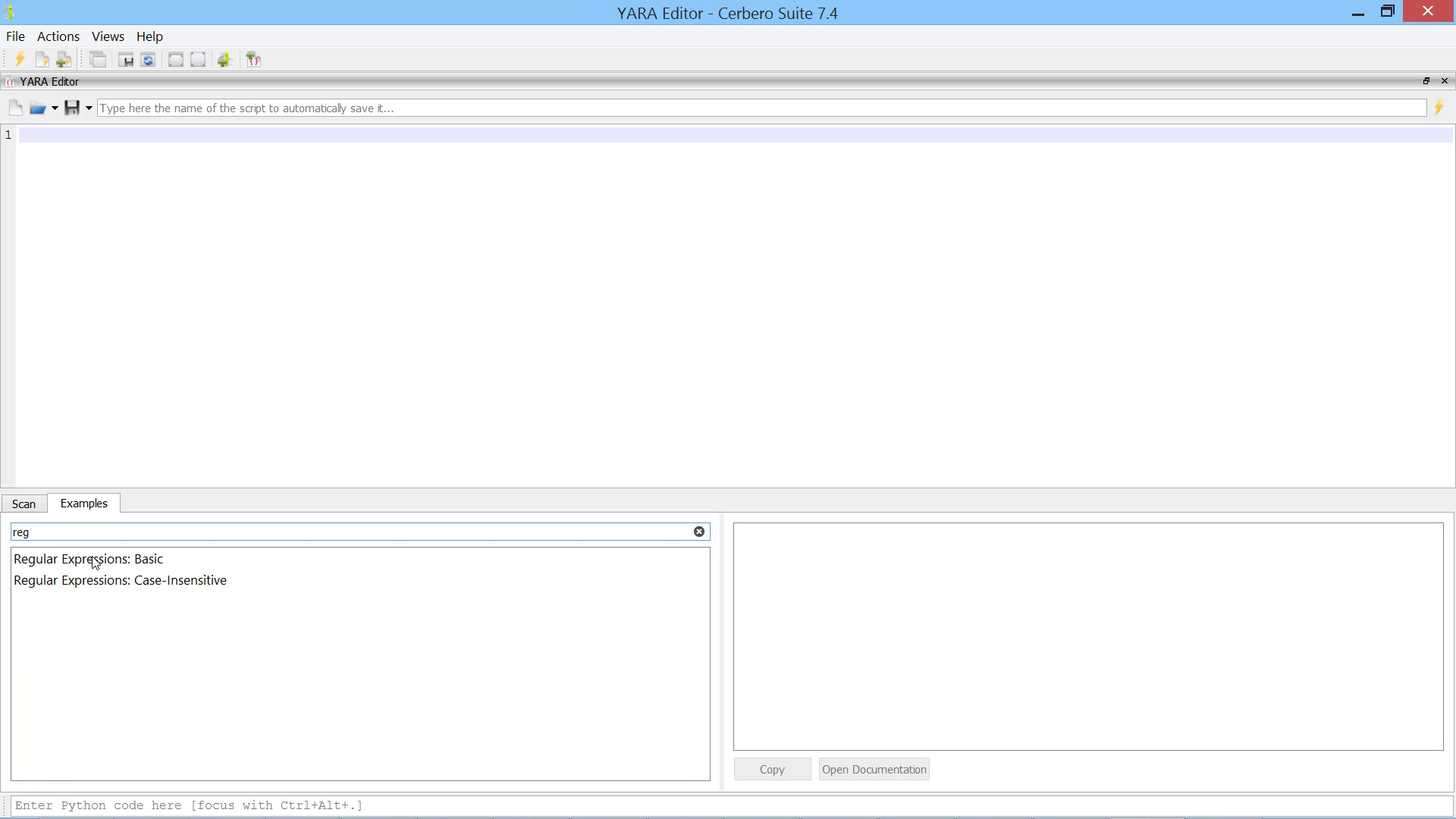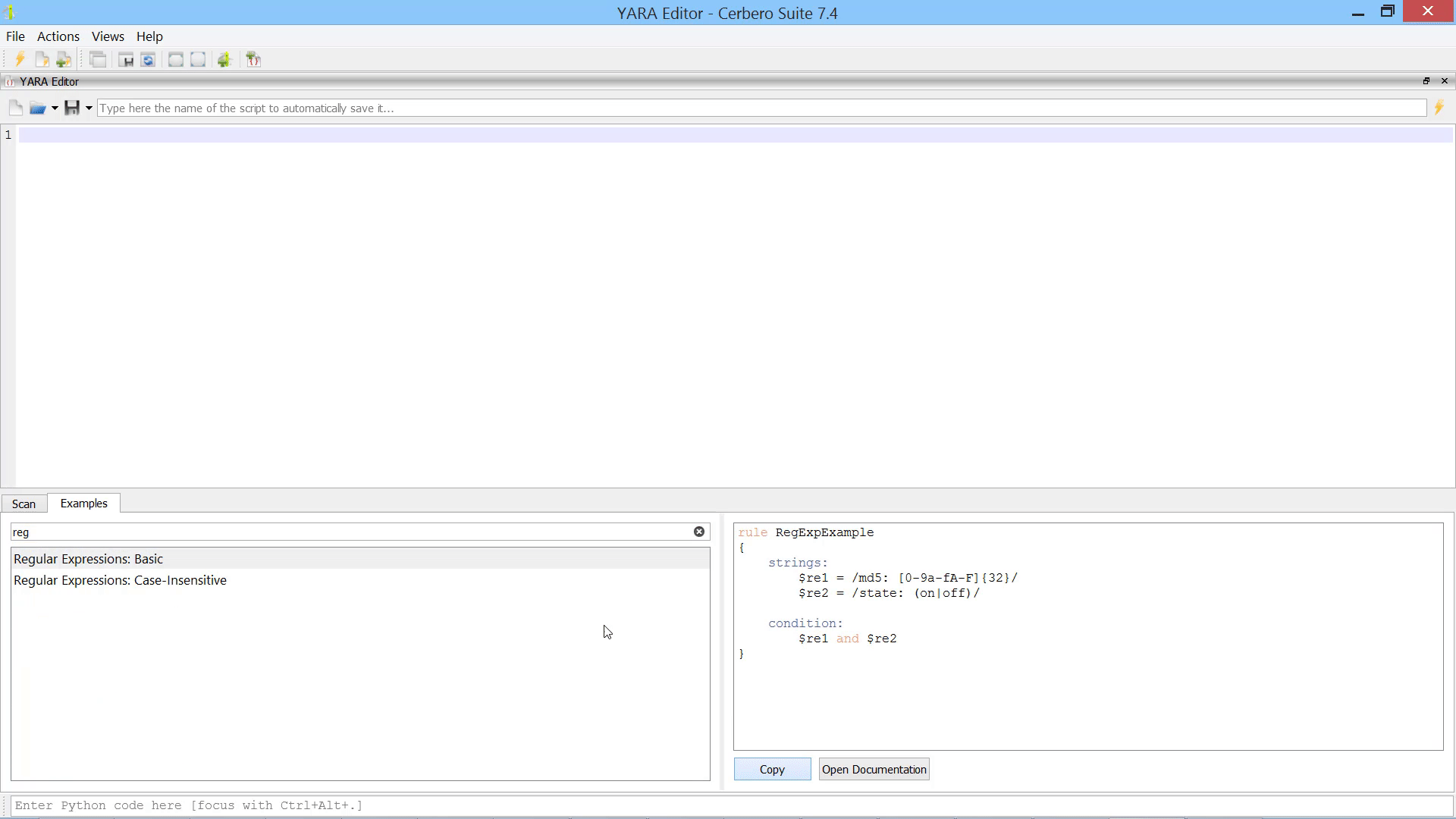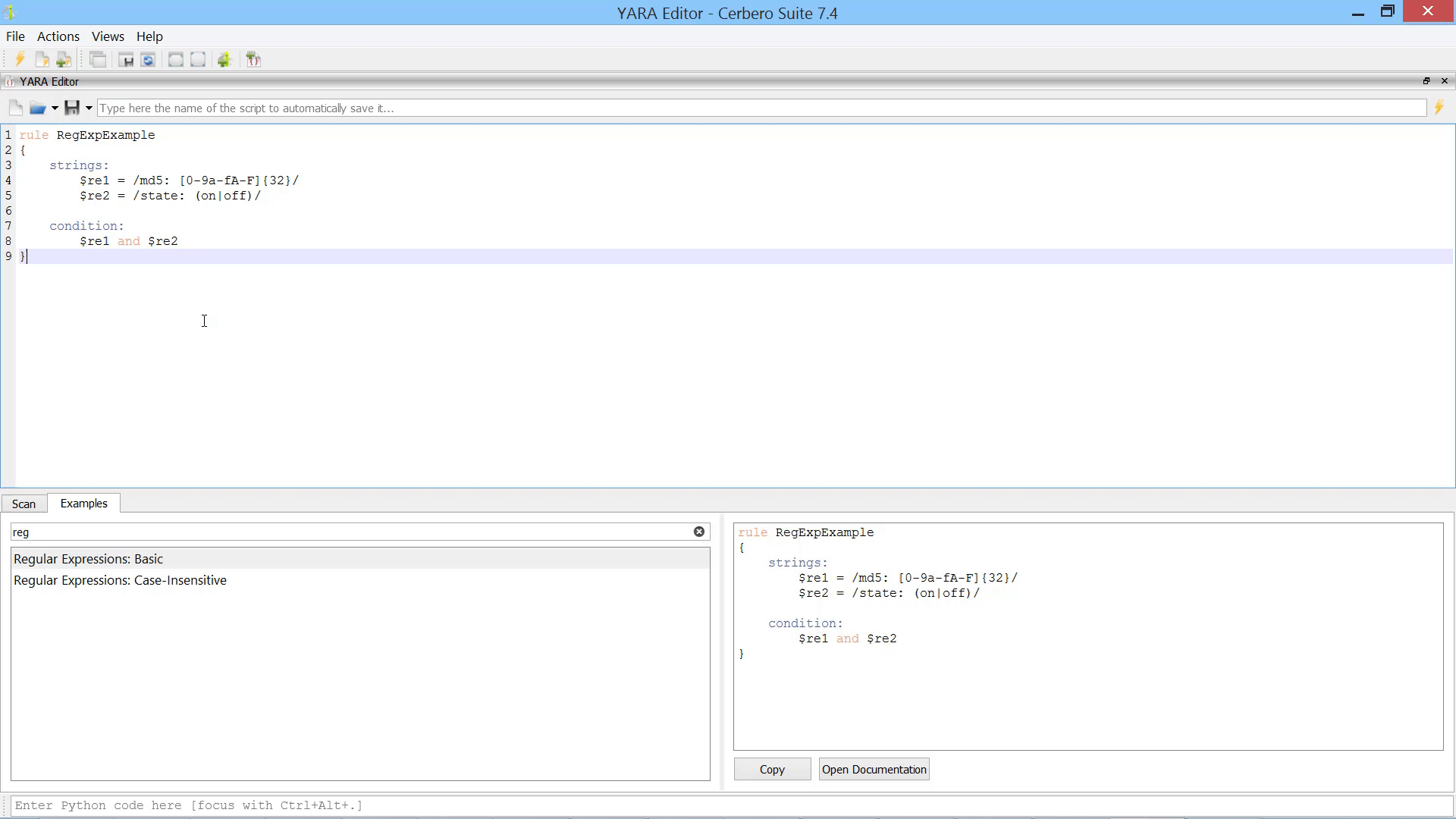
Each example is detailed further in the official YARA documentation, accessible via the ‘Open Documentation’ button.
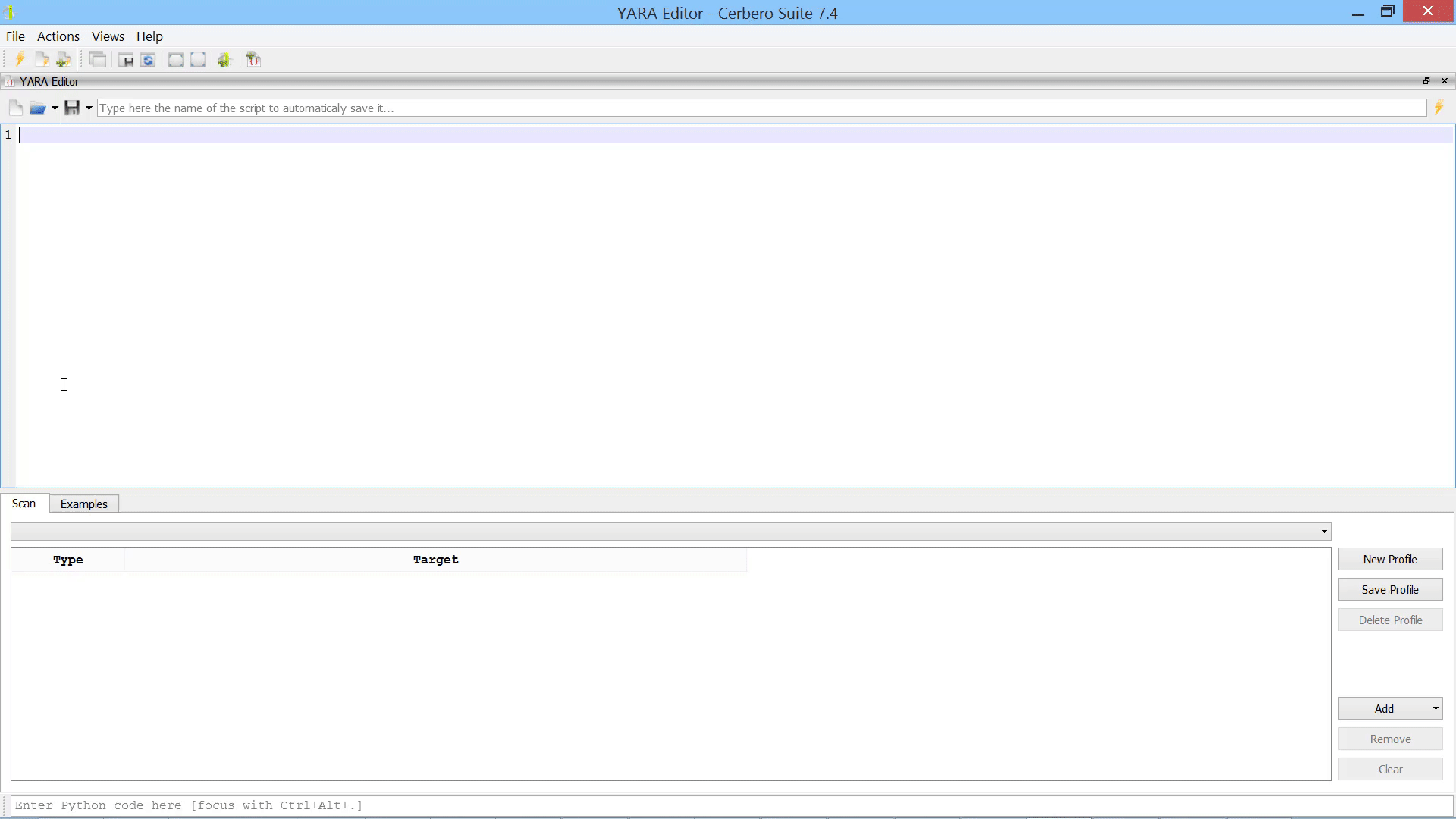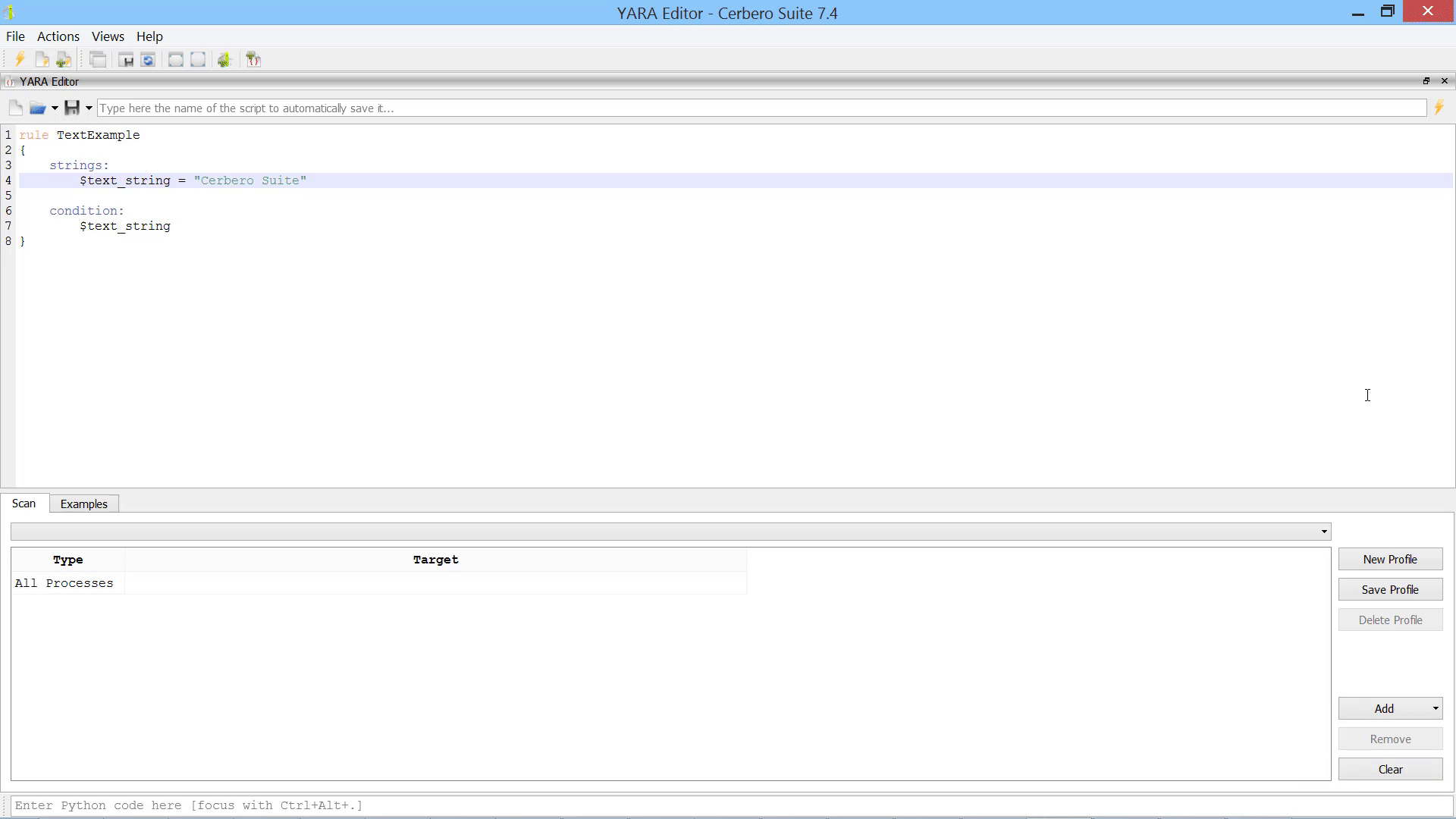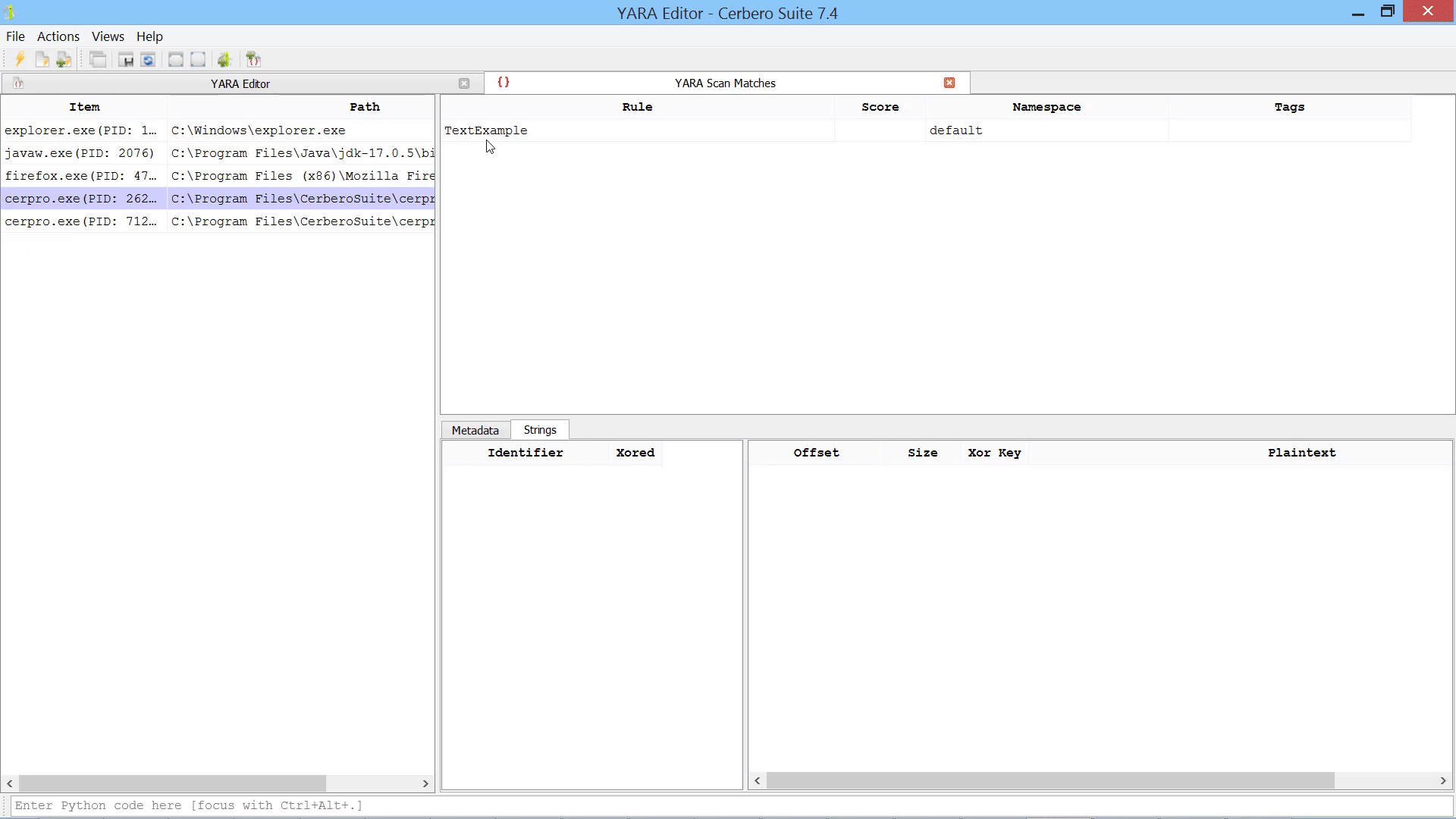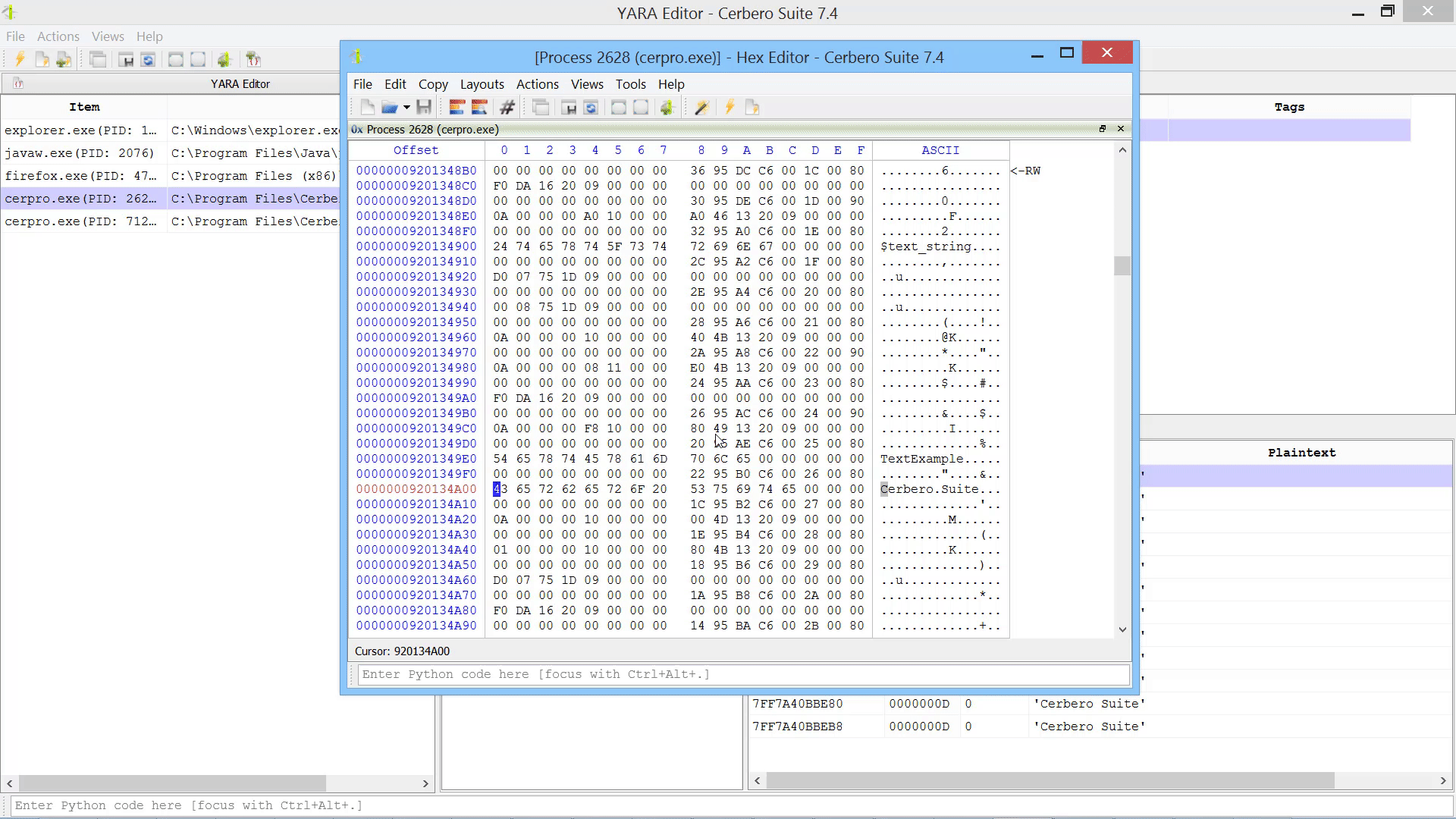
While the editor is an excellent tool for creating and editing YARA rules, it can also be utilized for quick searches in files, directories, and processes. Here is an example of how to swiftly search for a string in all processes and inspect the matches in memory.
The YARA Rules package also offers a variety of actions.
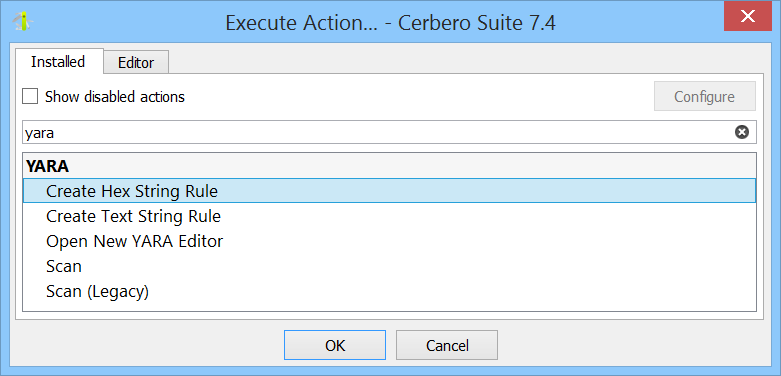
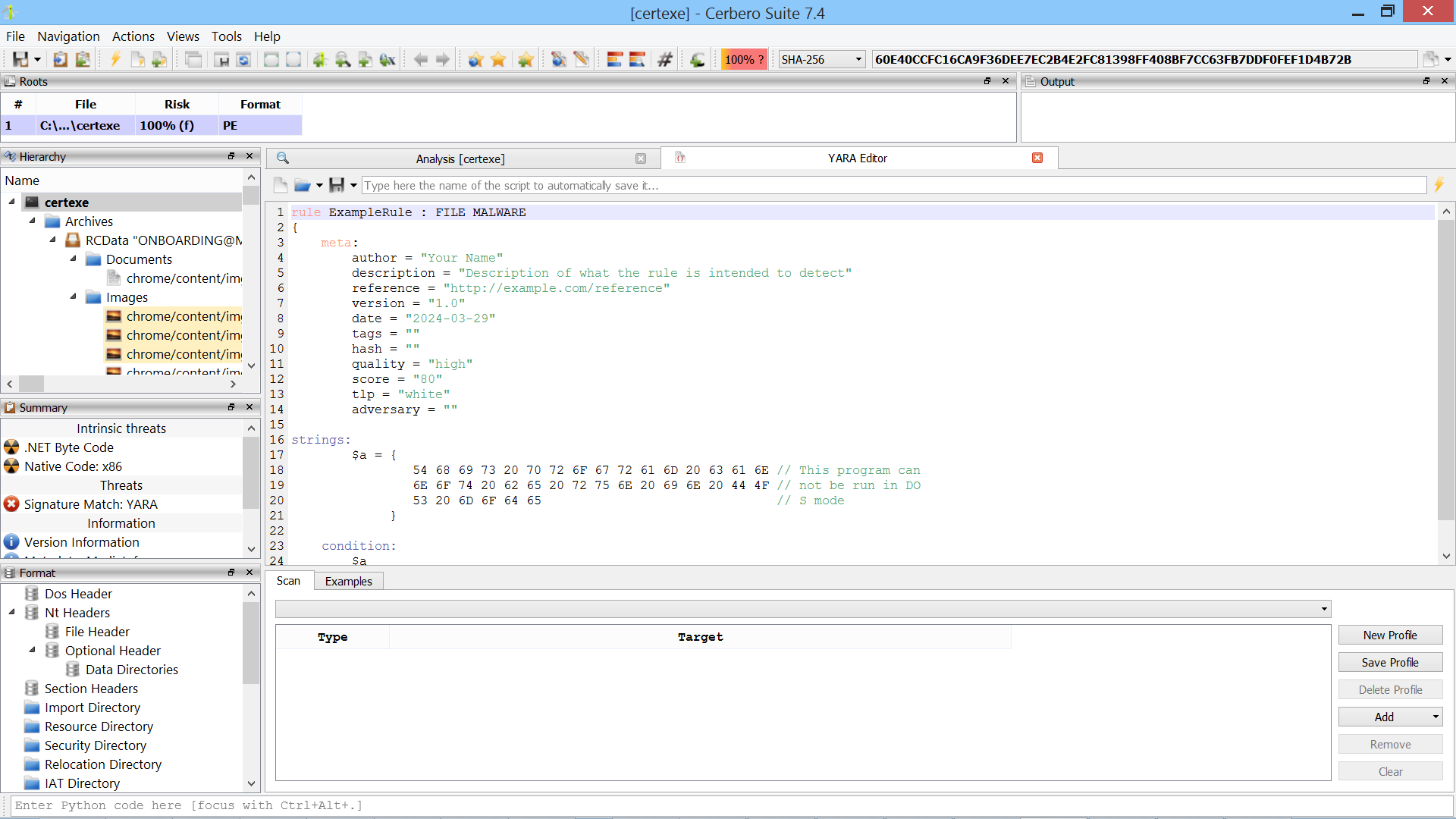
The ‘Scan’ action initiates a scan on data in a hex view, while the ‘Open New YARA Editor’ simply opens a new YARA editor. The ‘Create Hex String Rule’ and ‘Create Text String Rule’ actions generate respective rules based on the current selection. The rule below was generated from selected data in a hex view.
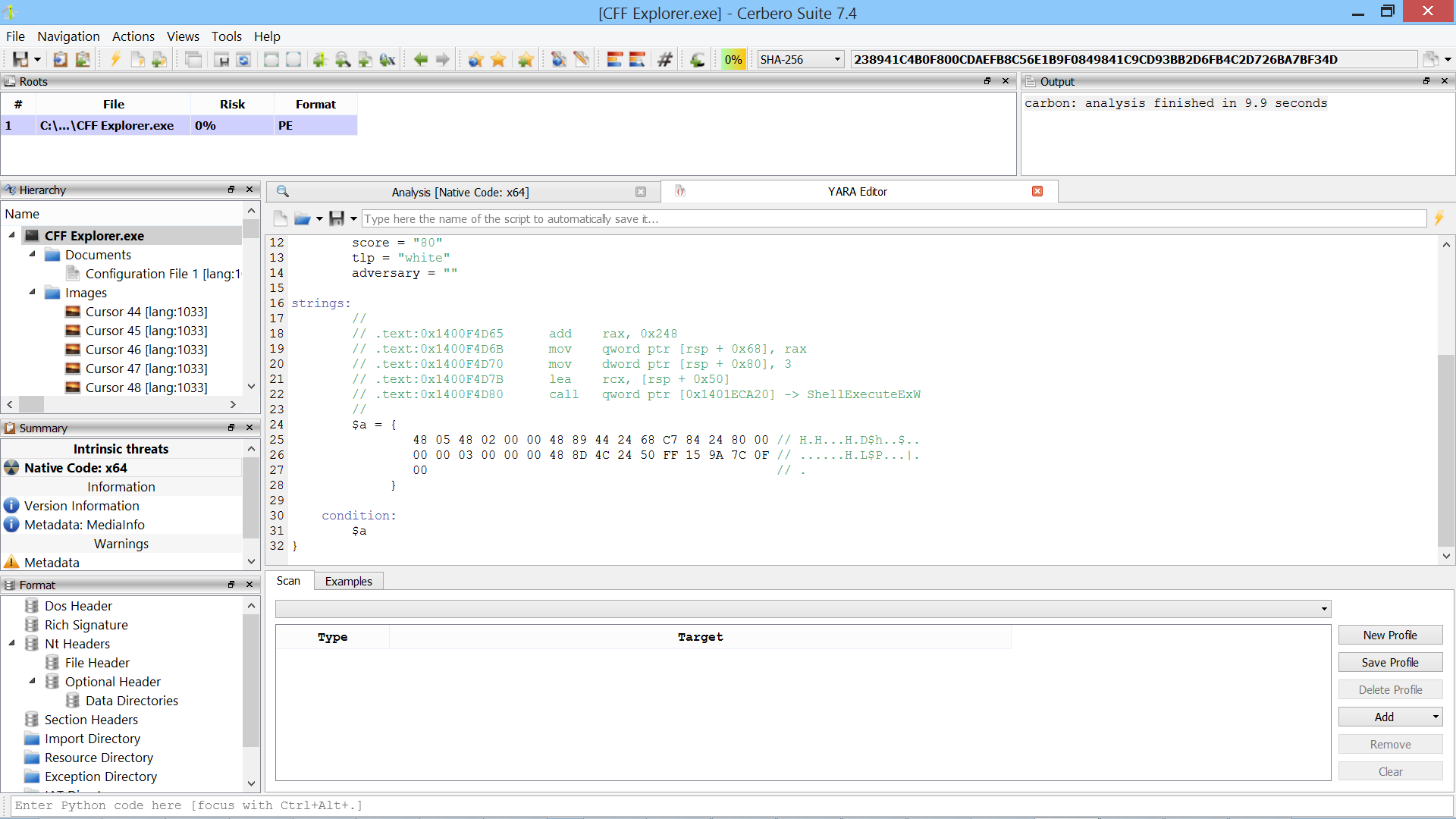
Meanwhile, the rule below was generated from selected instructions in a Carbon disassembly view.
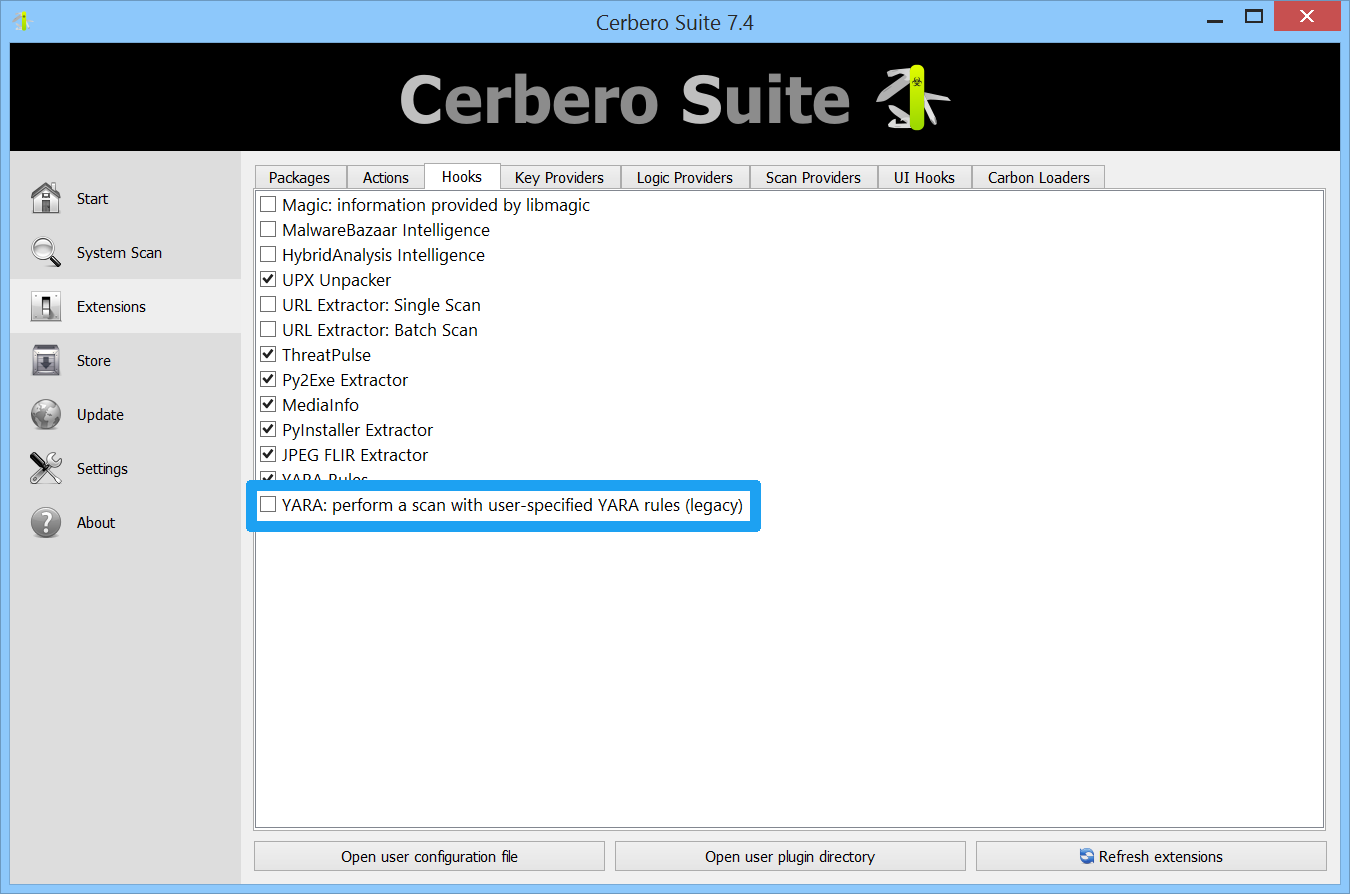
The ‘Scan (Legacy)’ action offers the legacy YARA scan functionality that was previously included in Cerbero Suite but is no longer part of the main installation.
The legacy hook is also available for customized scans using YARA.
All YARA modules are available on all supported systems. This includes the ‘Magic’ module, which isn’t officially available on Windows and the experimental ‘LNK’ module.
Developers can create installable rules packages for Cerbero Suite by including a configured ‘yara_sources.cfg’ file within their package.
In conclusion, the introduction of the YARA Rules package to Cerbero Suite marks a significant enhancement in the toolkit available to cybersecurity professionals. We are excited for you to explore its features and truly hope you enjoy the new capabilities it brings to your cybersecurity and forensic analysis endeavors.
One thought on “YARA Rules Package”