We are excited to announce the release of the Memory Analysis 0.7.6 package. This version introduces several improvements, some of which stem from testing our solution against various CTF challenges and didn’t make it into version 0.7.
Category: Package
XST Format Package
We released the XST Format package, which adds support for Microsoft Outlook PST and OST email data formats.
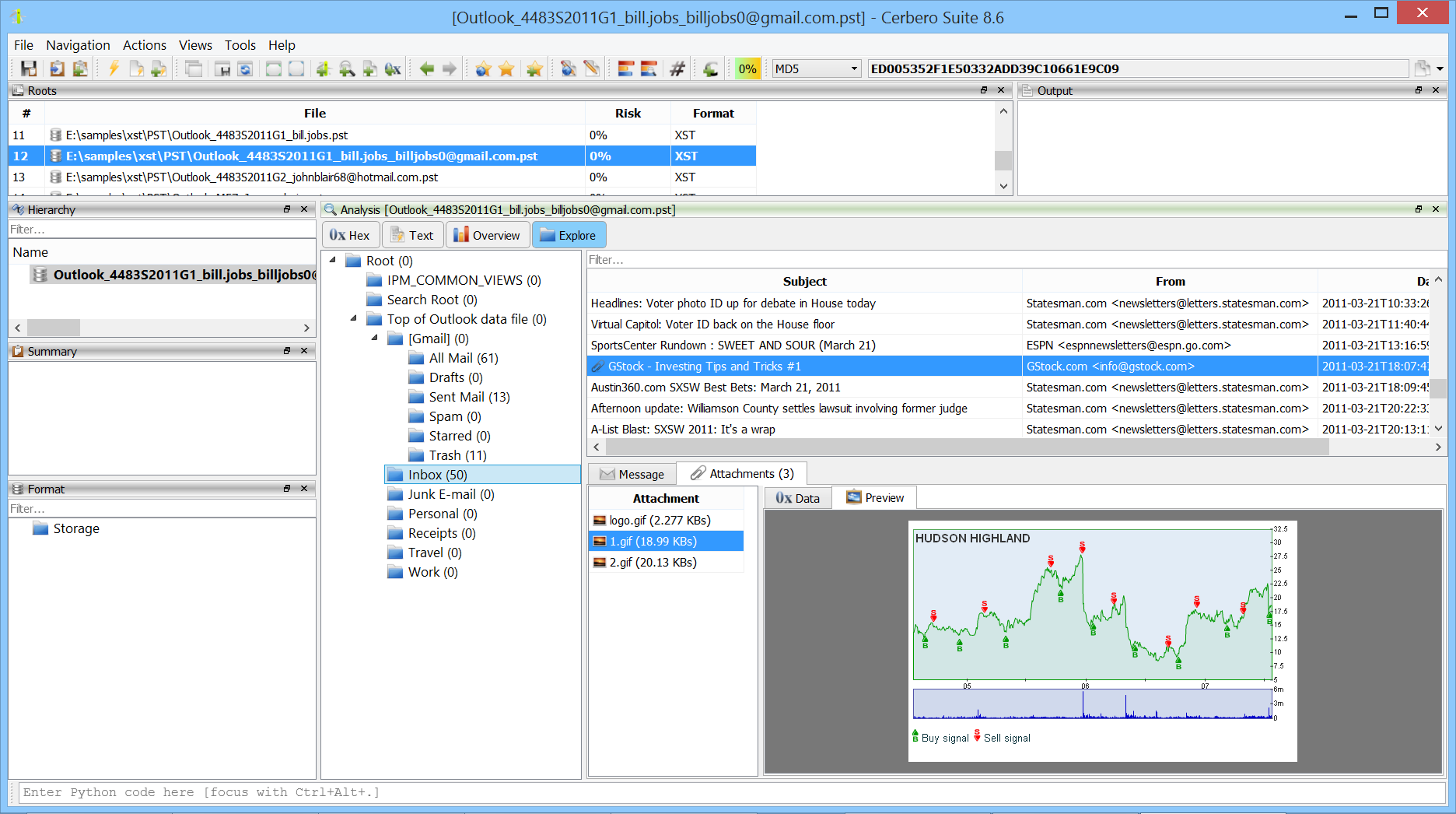
The package makes it possible to explore every part of an email container, including messages, folder structures, metadata and attachments.
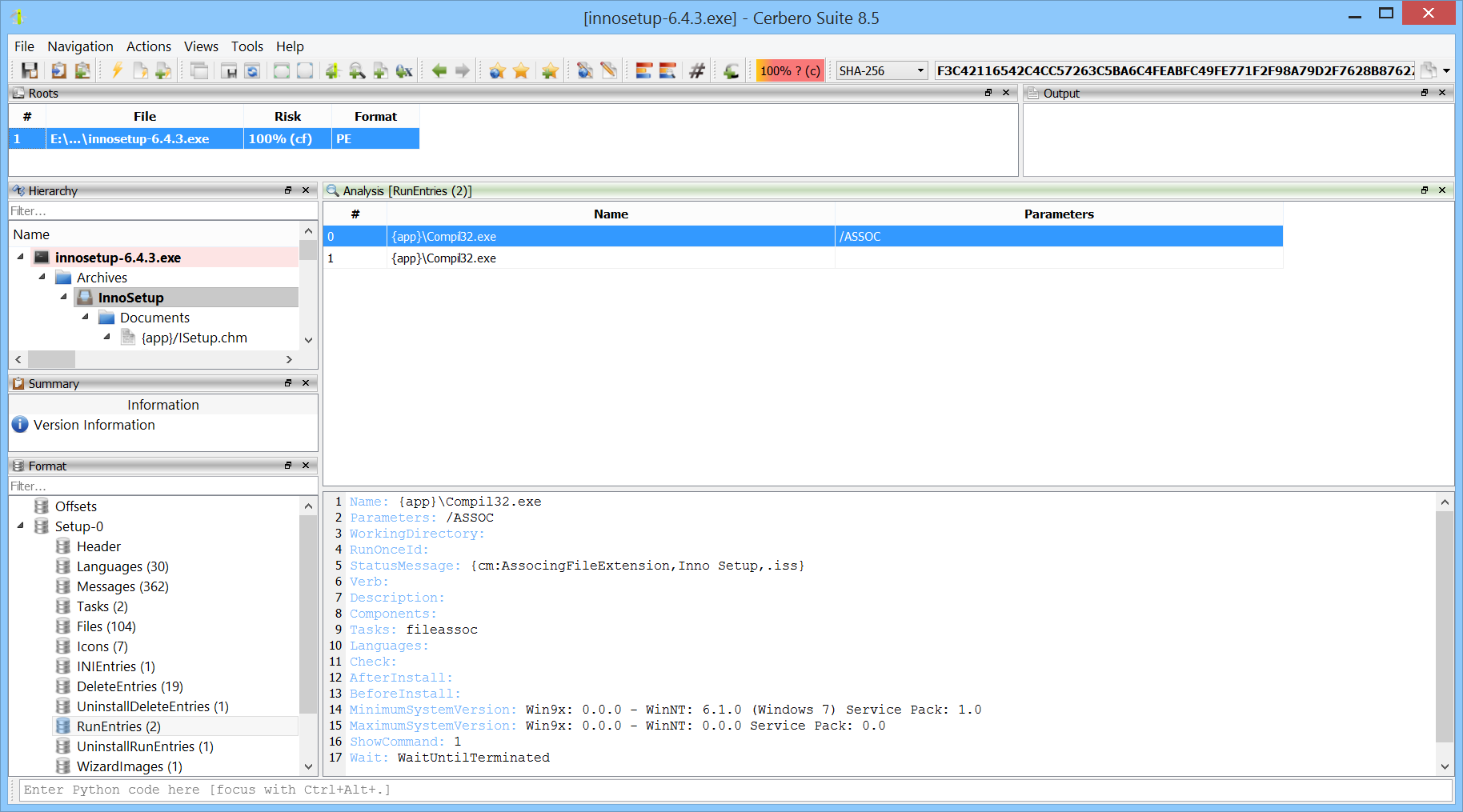
InnoSetup Format Package 3.0
Version 3 of our state-of-the-art InnoSetup Format package is now available and includes support for the latest releases of InnoSetup and the recently introduced full encryption mode.
In addition to the format itself and file extraction, make sure to install the IFPS Format package to inspect the code of setup scripts.
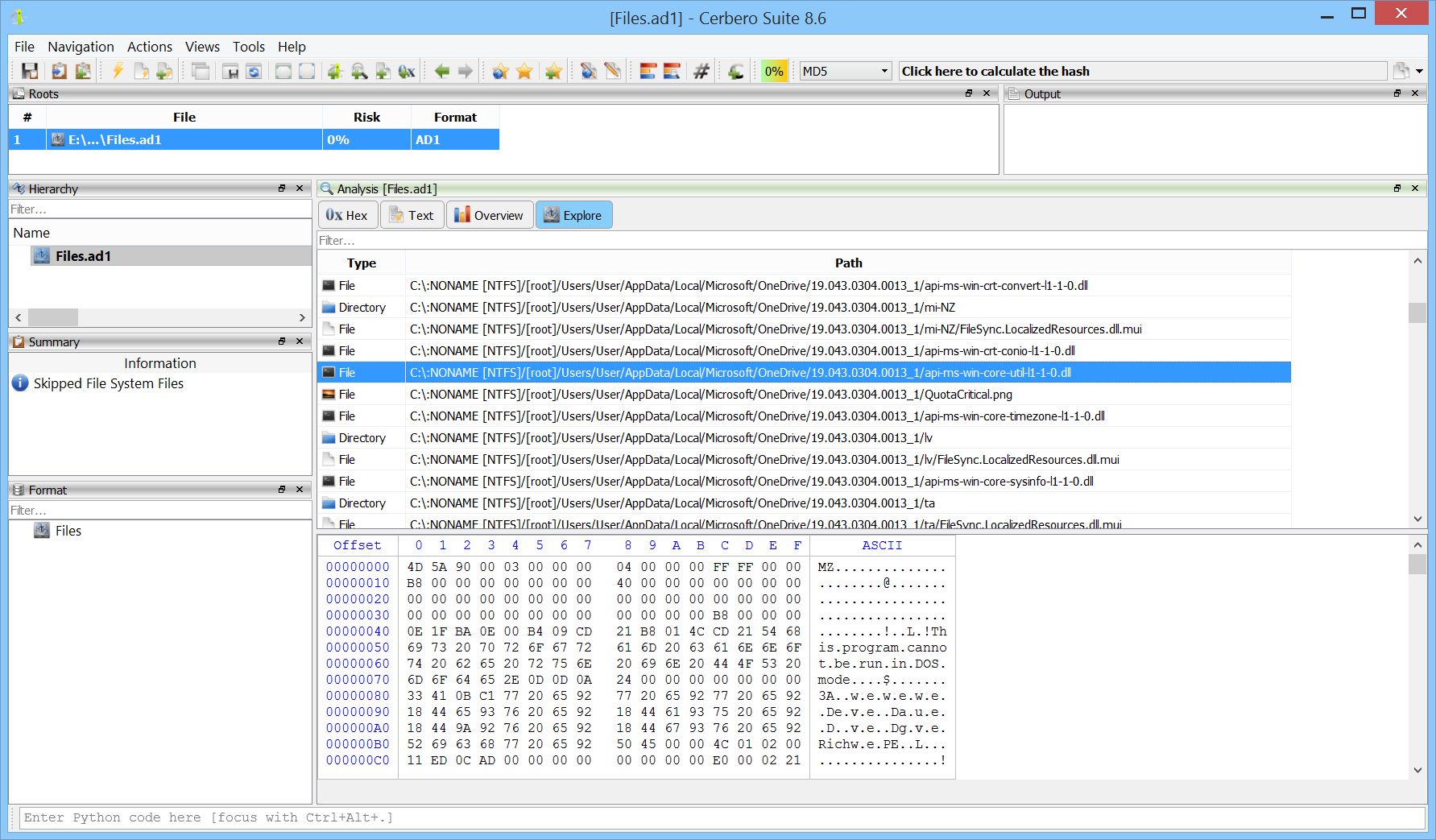
AD1 Format Package
We released the AD1 Format package, which adds basic support for AccessData Custom Content Image files. AD1 images are logical evidence containers created by FTK Imager and other AccessData tools, used to store selected files or folders from a system rather than a full physical disk image.
Memory Analysis Package 0.7
We are excited to announce the release of the Memory Analysis 0.7 package, which is currently in beta. This version introduces significant improvements that partly stem from testing our solution against various CTF challenges.
These new features, together with the recent release of Cerbero Suite 8.6, make this update particularly noteworthy. Thanks to the sophisticated caching mechanism implemented in the latest release of Cerbero Suite, memory analysis is now faster than ever. If you thought it was already fast, you are in for a surprise!
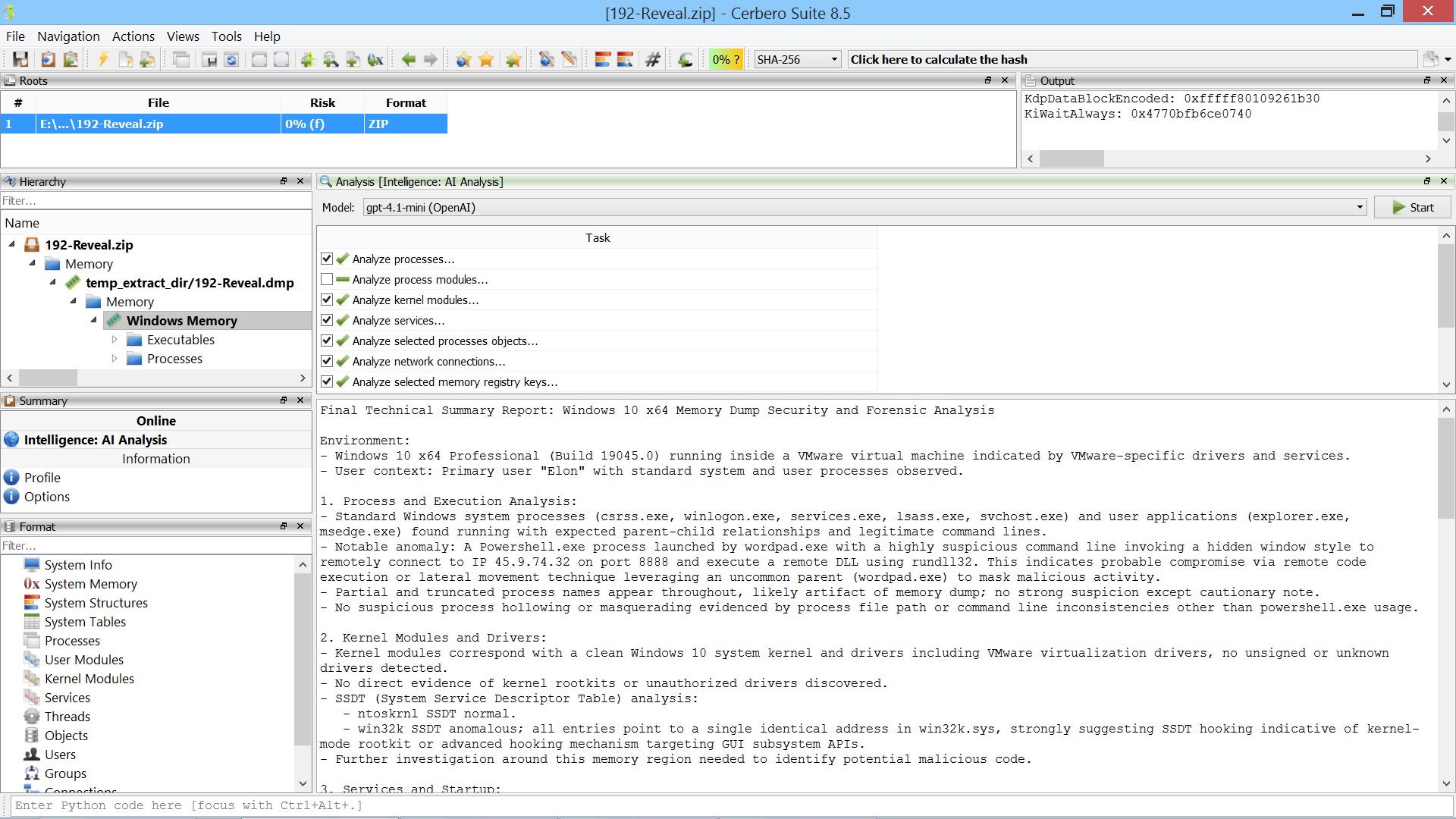
AI Assistant Package (Beta)
We’re happy to announce the beta release of the AI Assistant package. This package integrates popular Large Language Models (LLMs) to assist with file analysis.
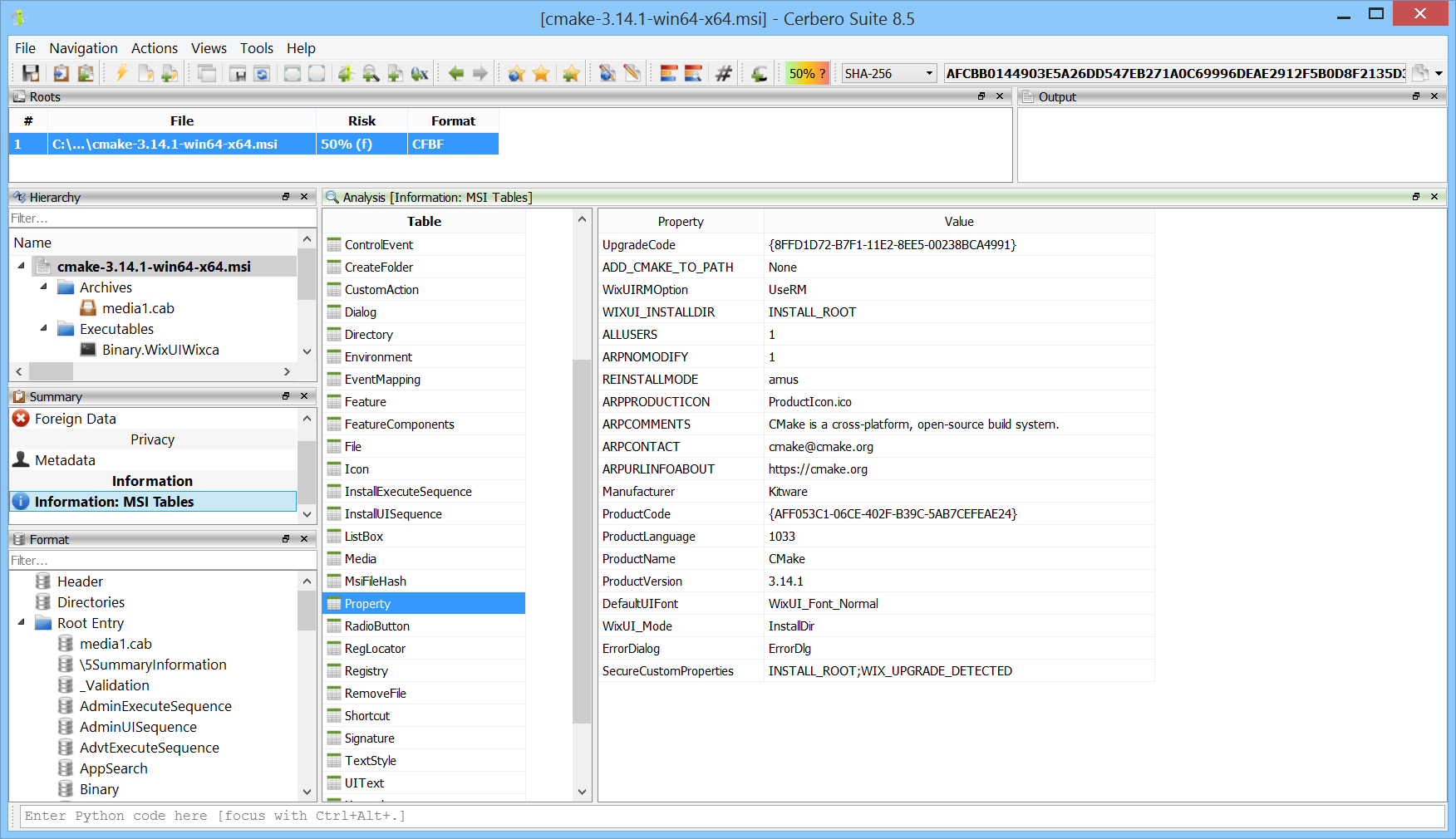
MSI Format Package
While the extraction of files from Windows Installer (MSI) files has always been supported, we’ve now released the MSI Format package to offer in-depth support for the format, such as the display of tables.
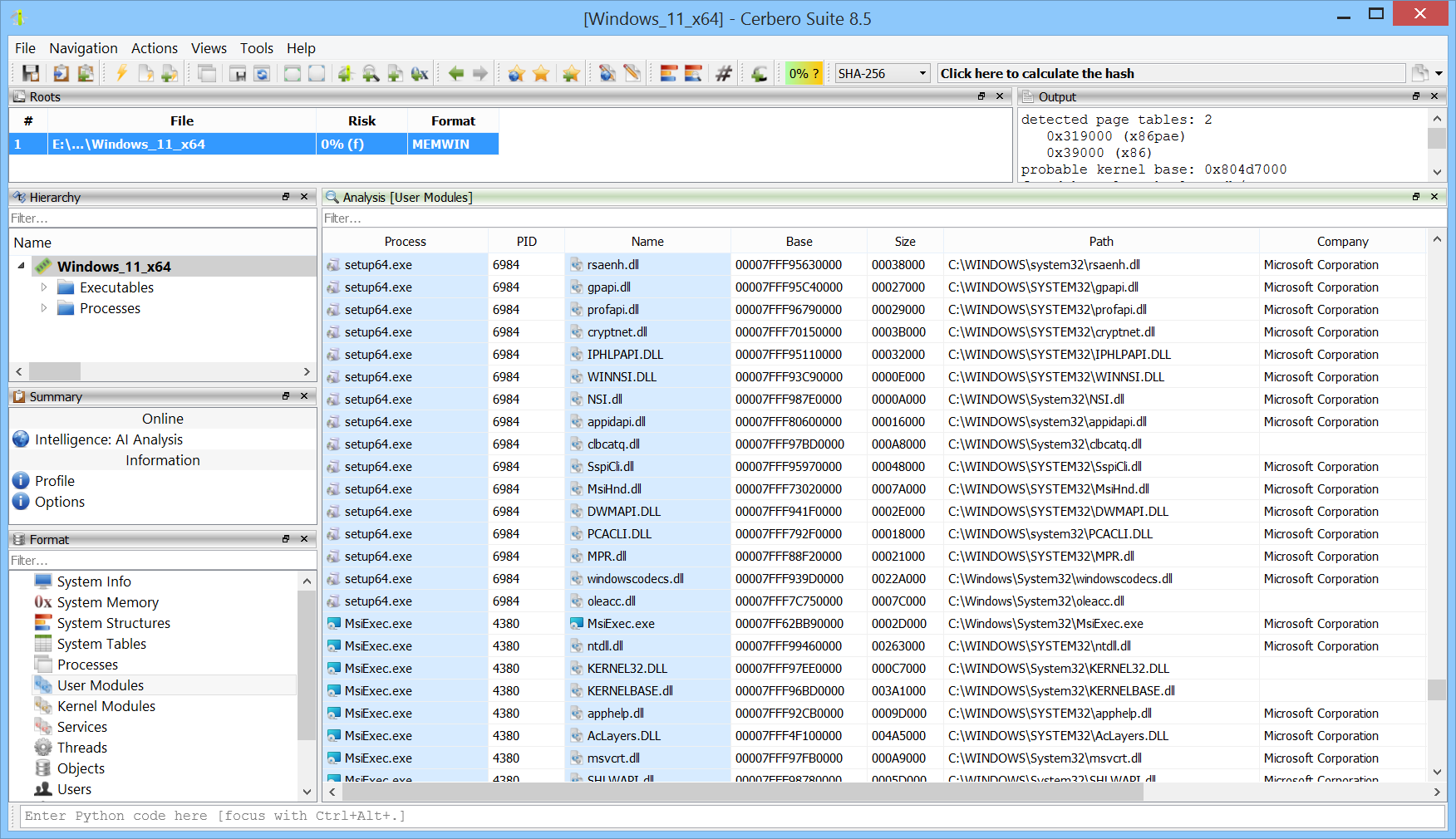
Memory Analysis Package 0.6
We’ve released version 0.6 of the Memory Analysis package, currently in beta.
All user modules from all processes can now be inspected at once. This makes it easy to discover which processes load a particular module.
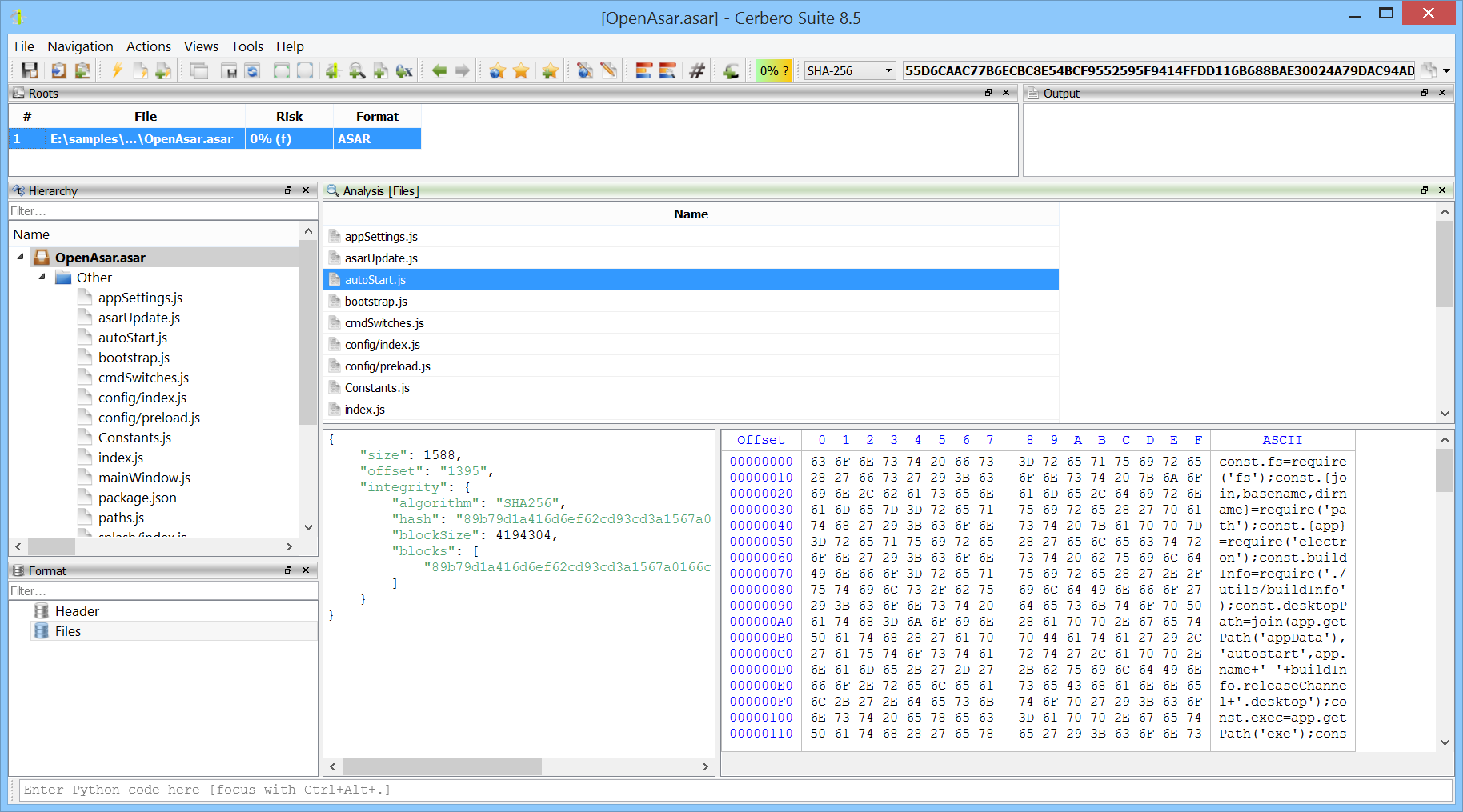
ASAR Format Package
We’ve released the ASAR Format package, which adds support for the Atom Shell Archive Format, which is a lightweight archive format primarily used in Electron applications.
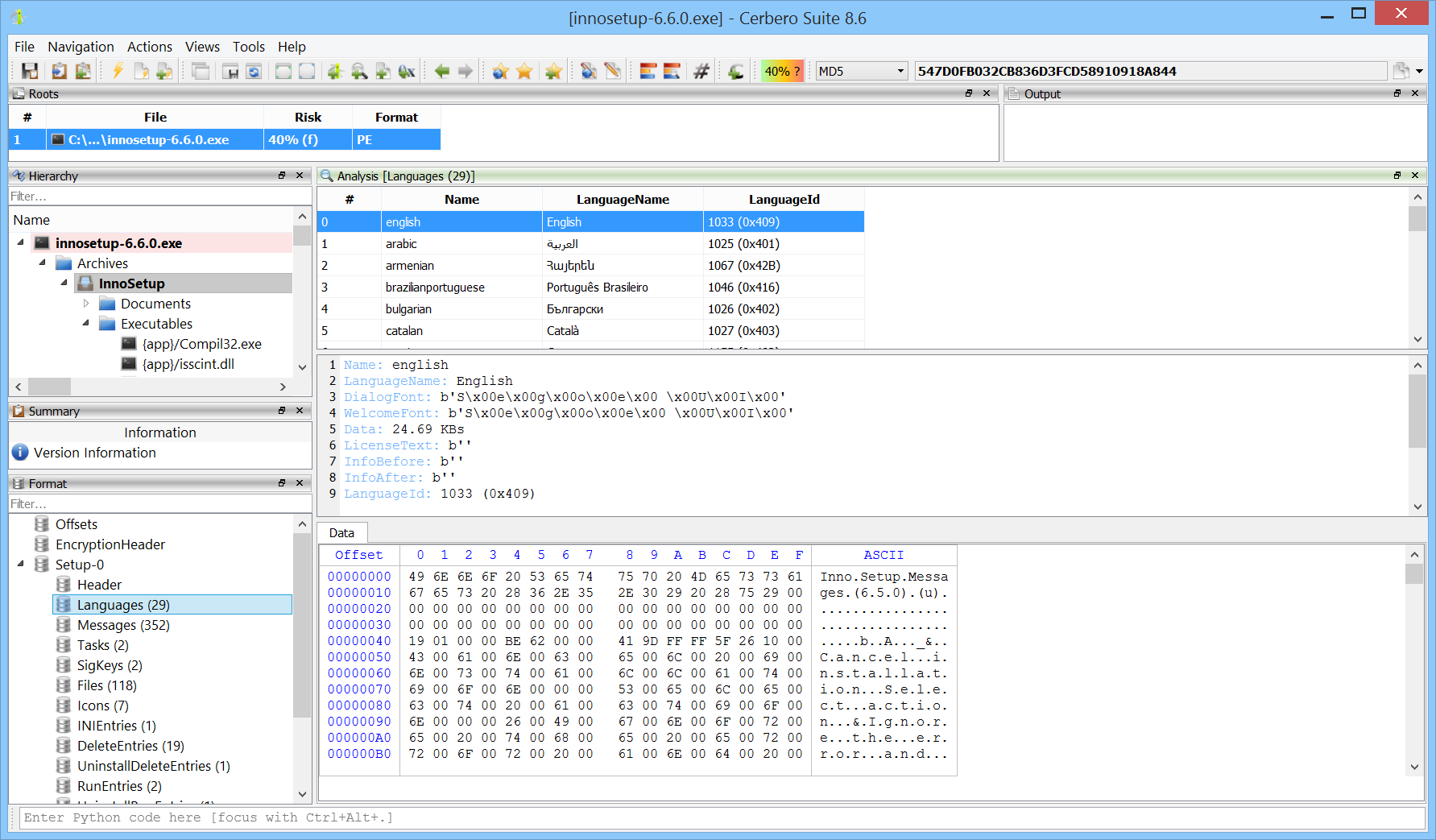
InnoSetup Format Package 2.0
Version 2 of the InnoSetup Format package is now available and includes support for the latest releases of InnoSetup.