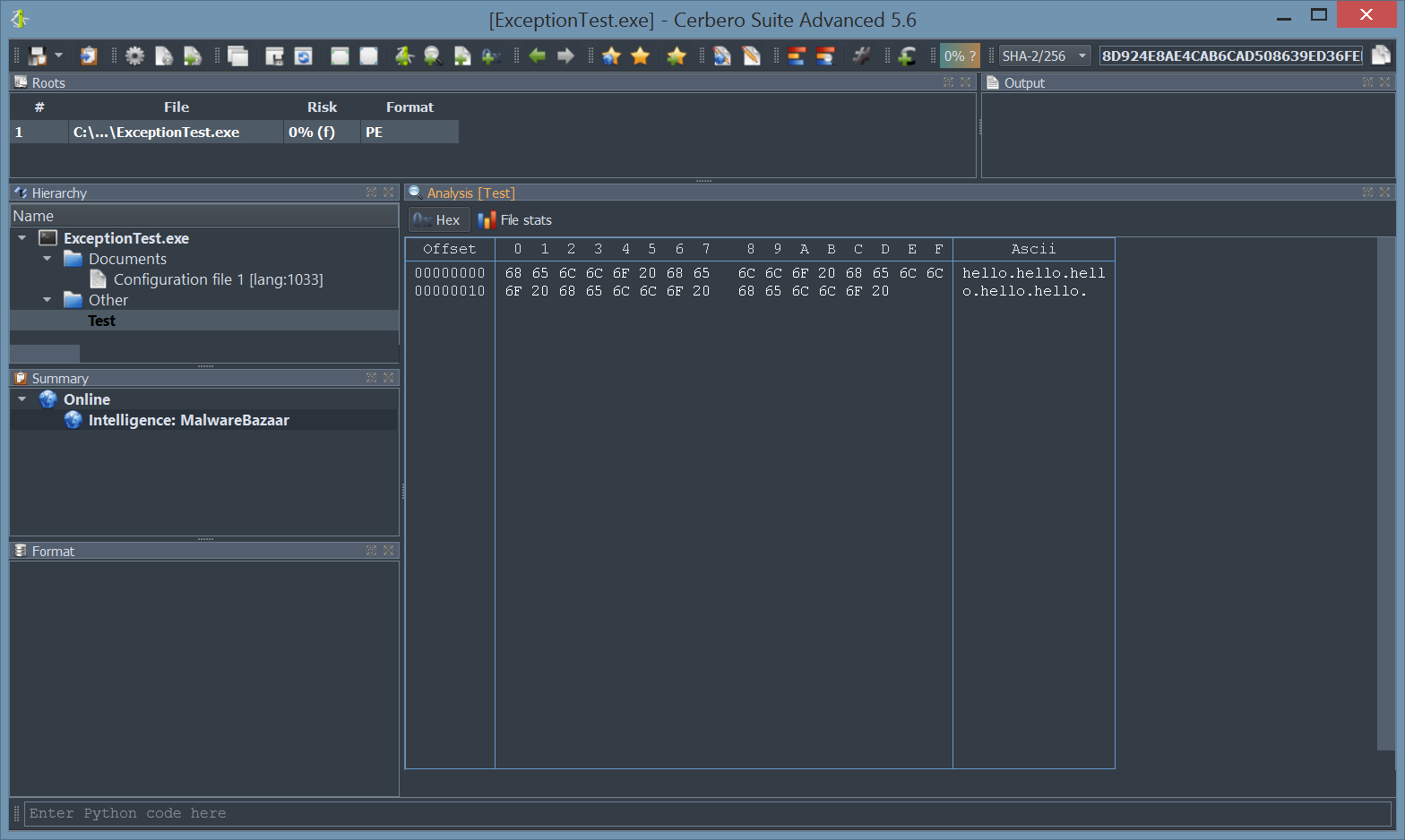
In the upcoming 5.6 version of Cerbero Suite we’ve made several improvements which can be best described as ‘after-scanning actions’.
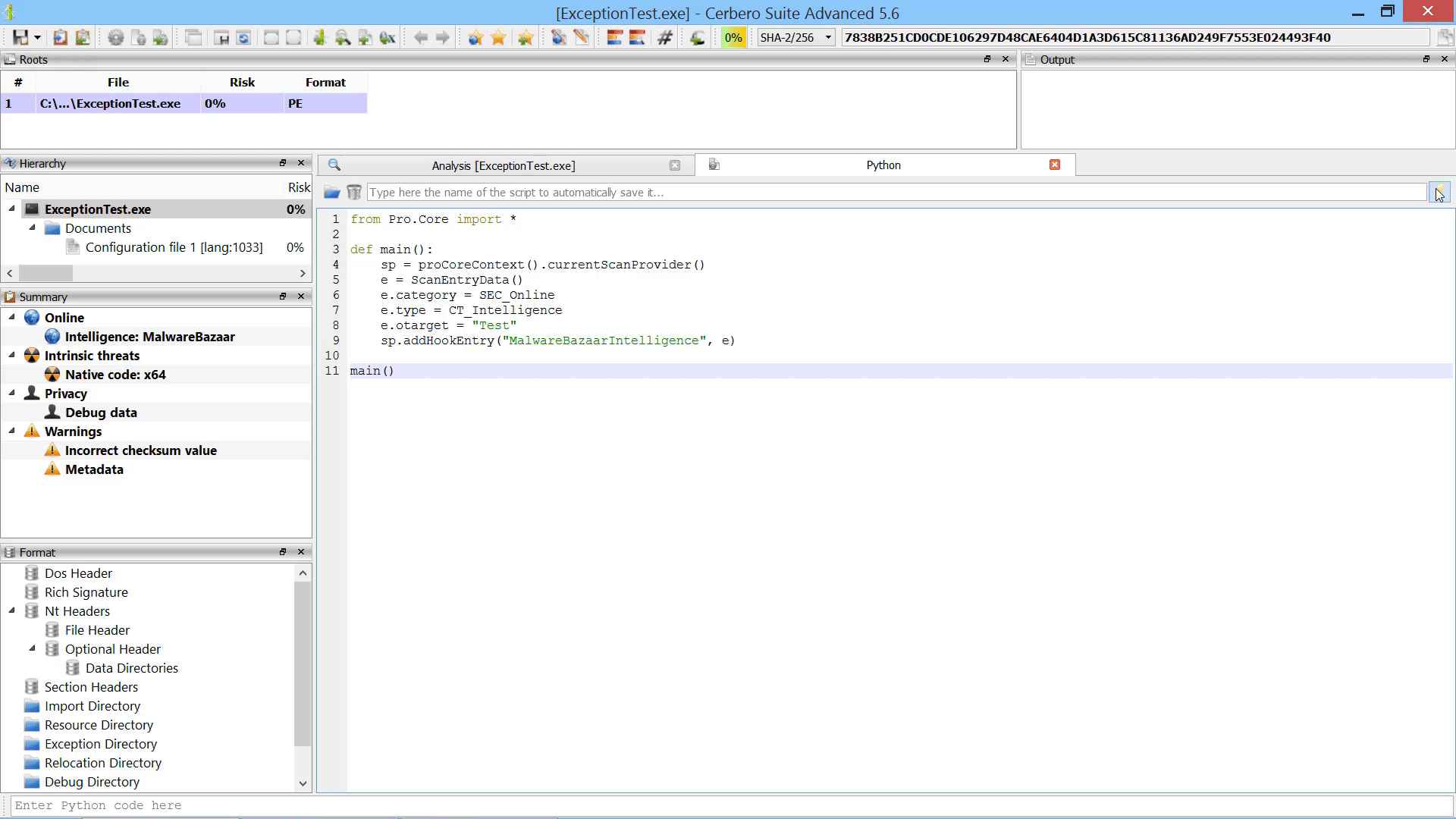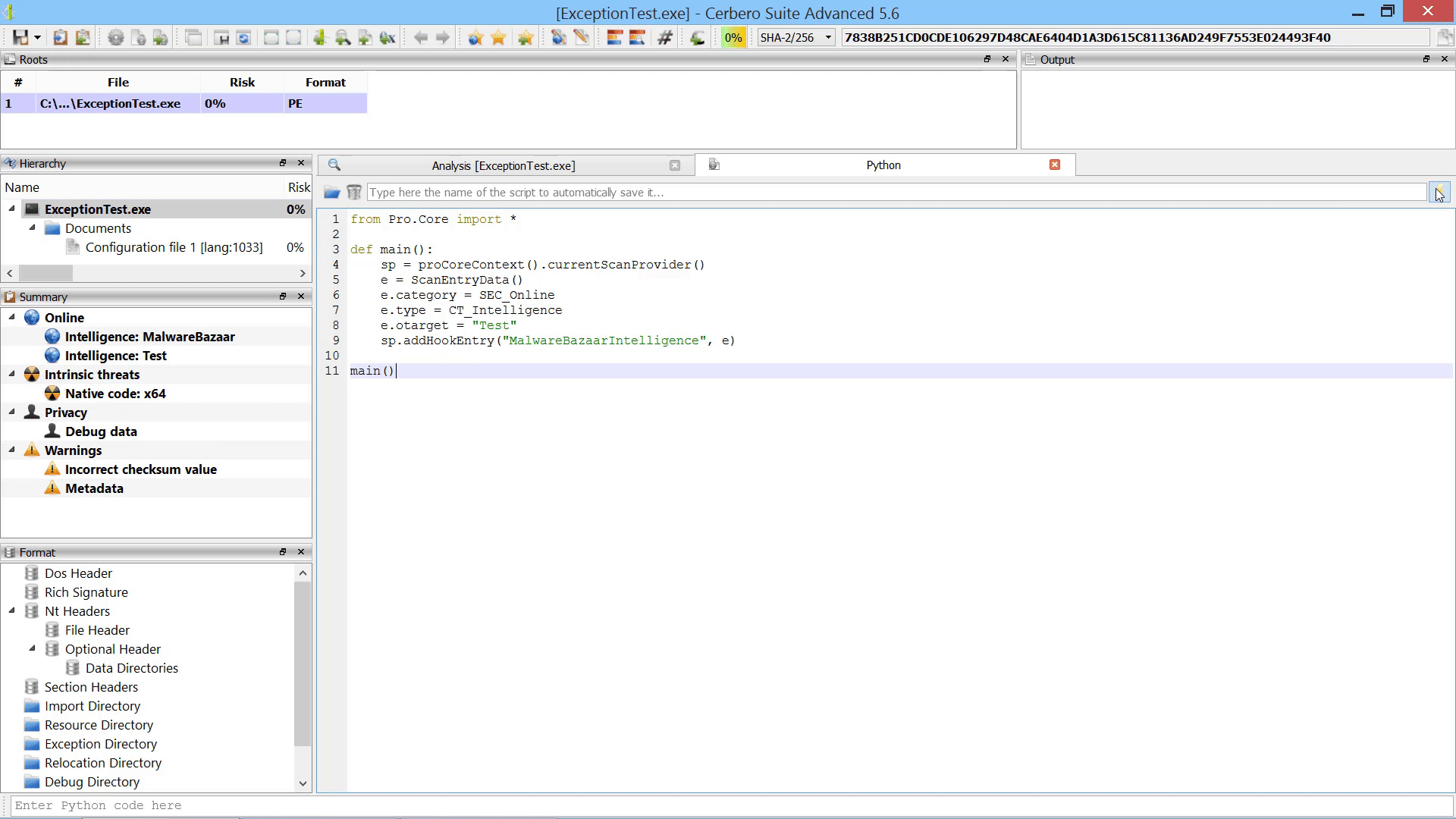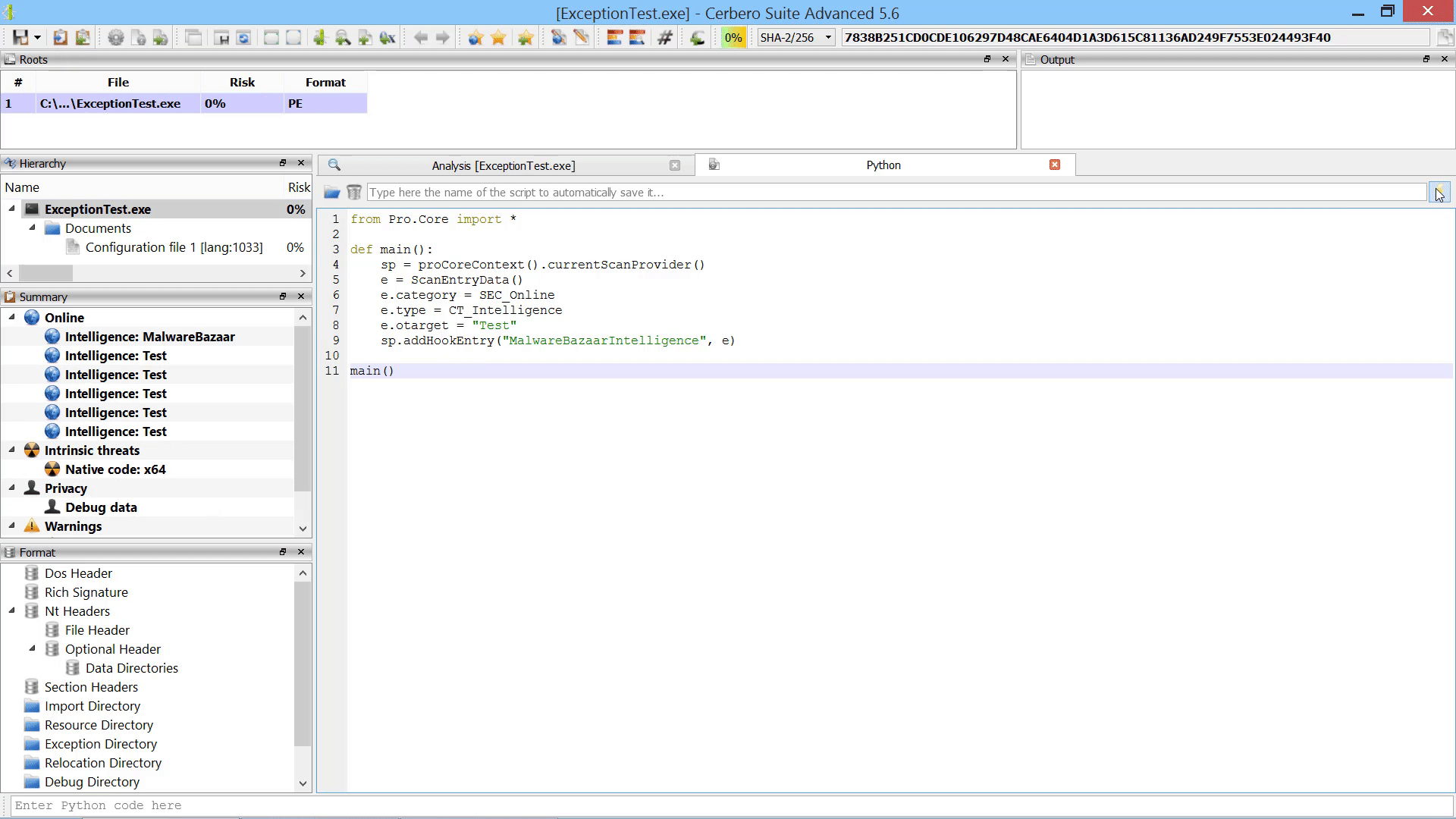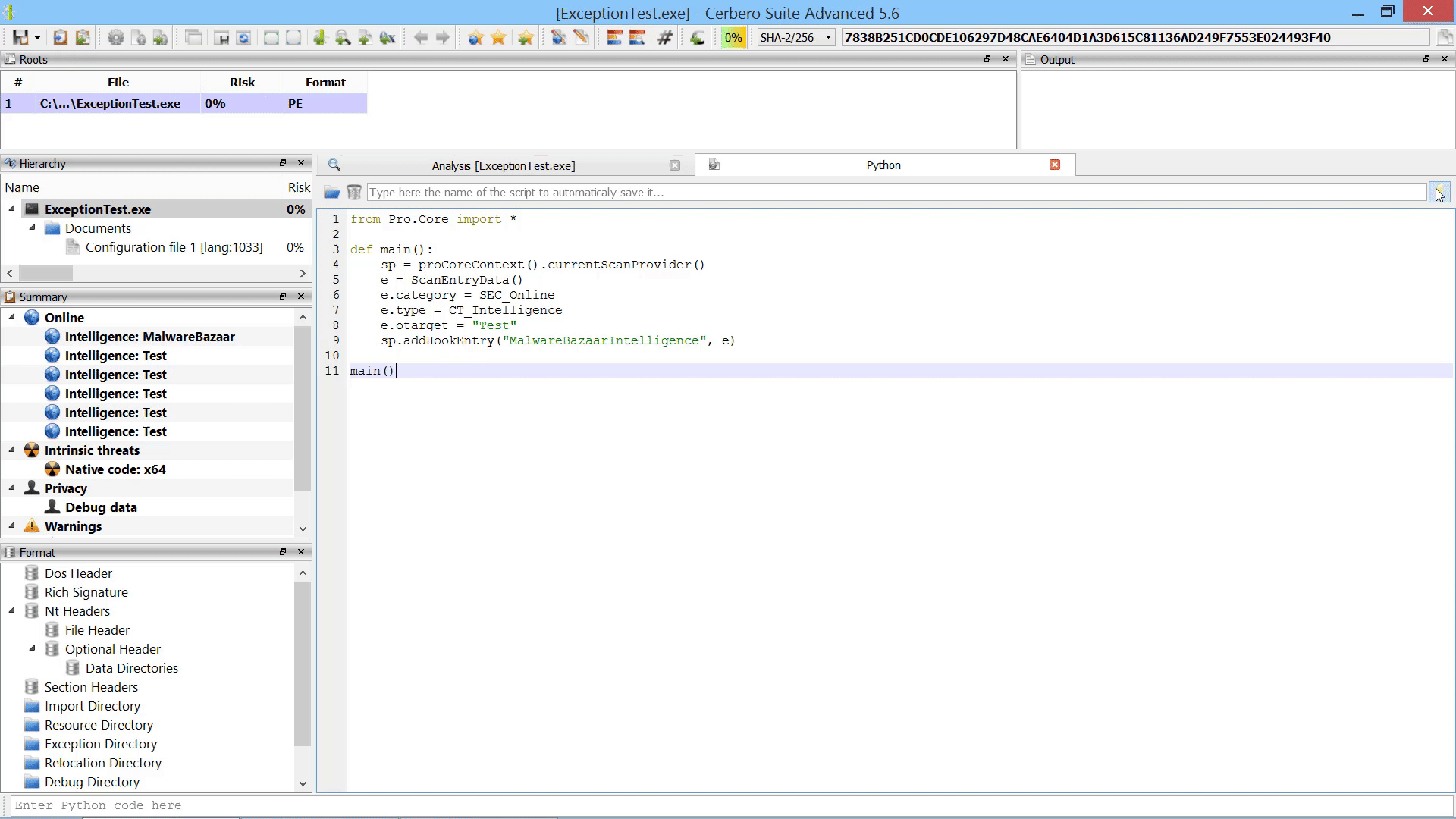
For instance, it is now possible to programmatically add scan entries to a report after the scanning has occurred.
The following is the code used in the example.
from Pro.Core import *
def main():
sp = proCoreContext().currentScanProvider()
e = ScanEntryData()
e.category = SEC_Online
e.type = CT_Intelligence
e.otarget = "Test"
sp.addHookEntry("MalwareBazaarIntelligence", e)
main()
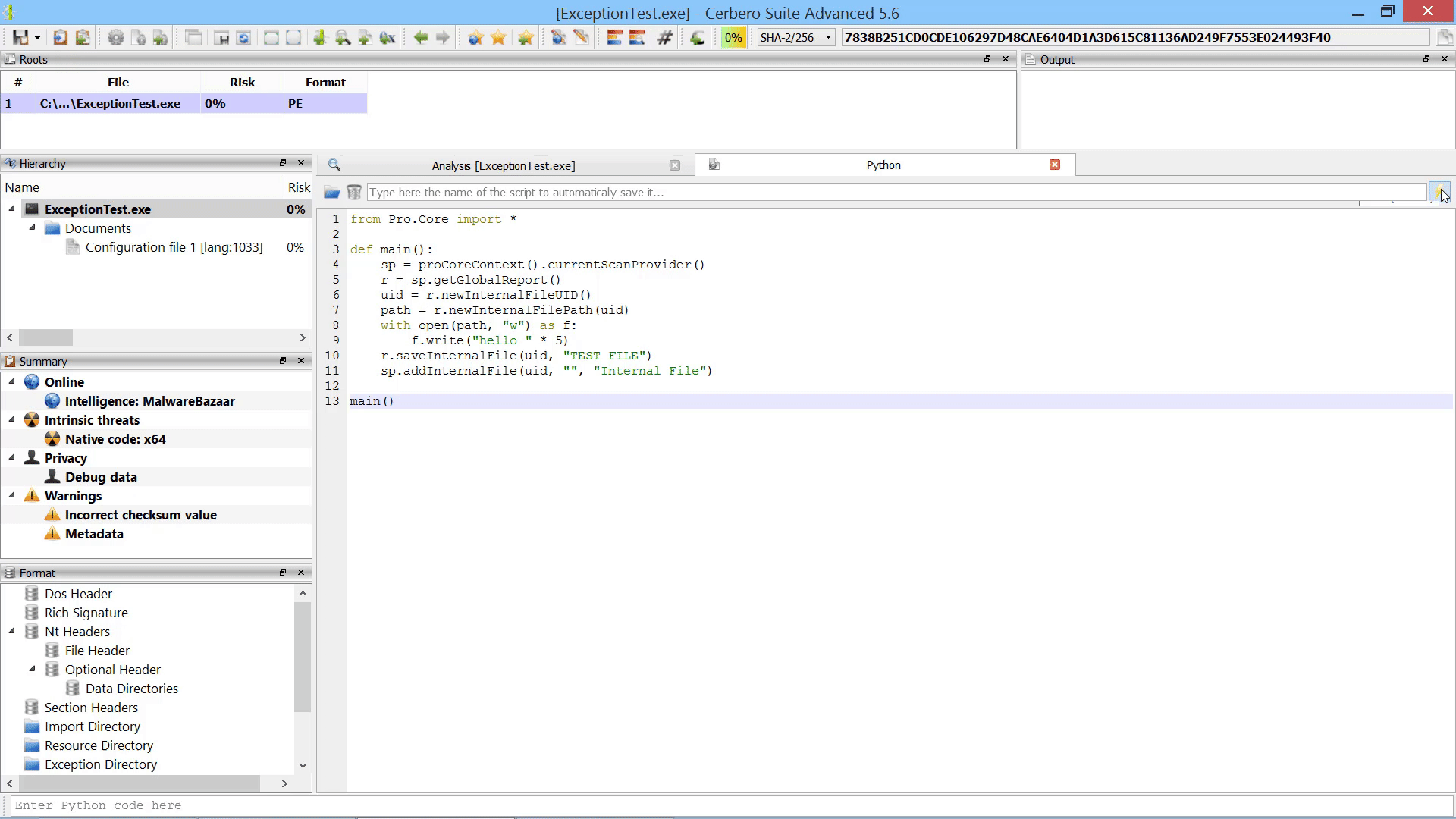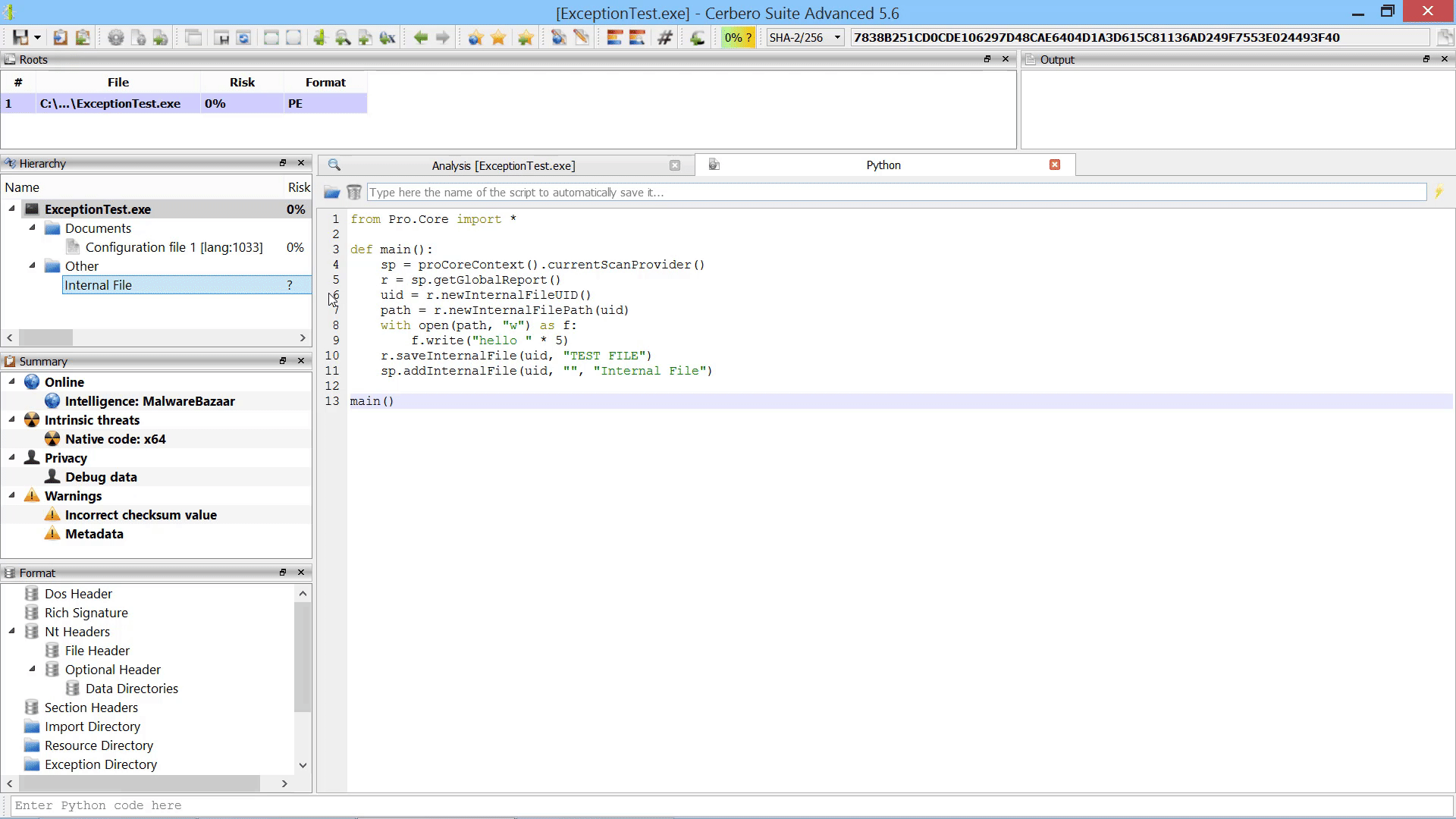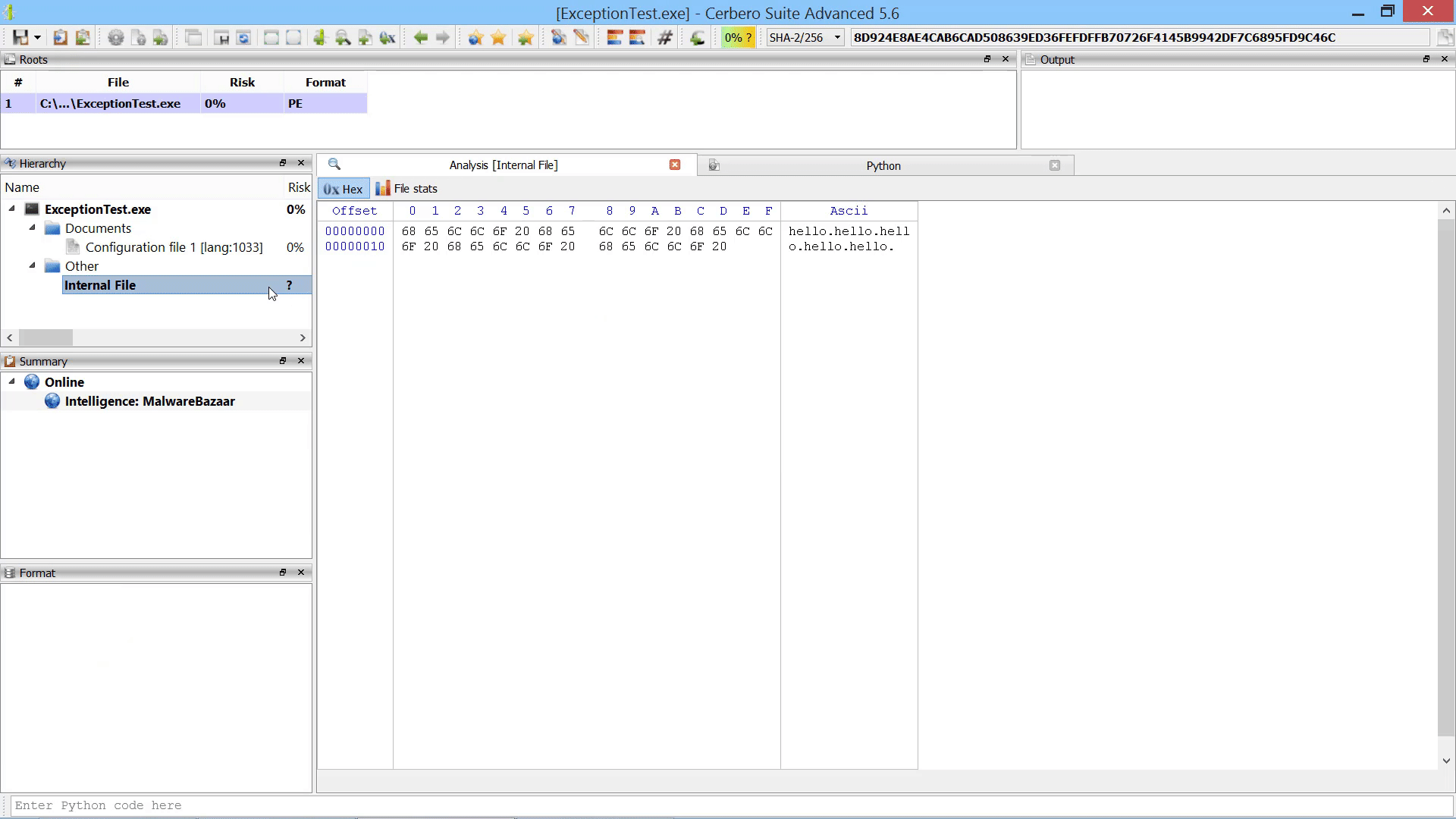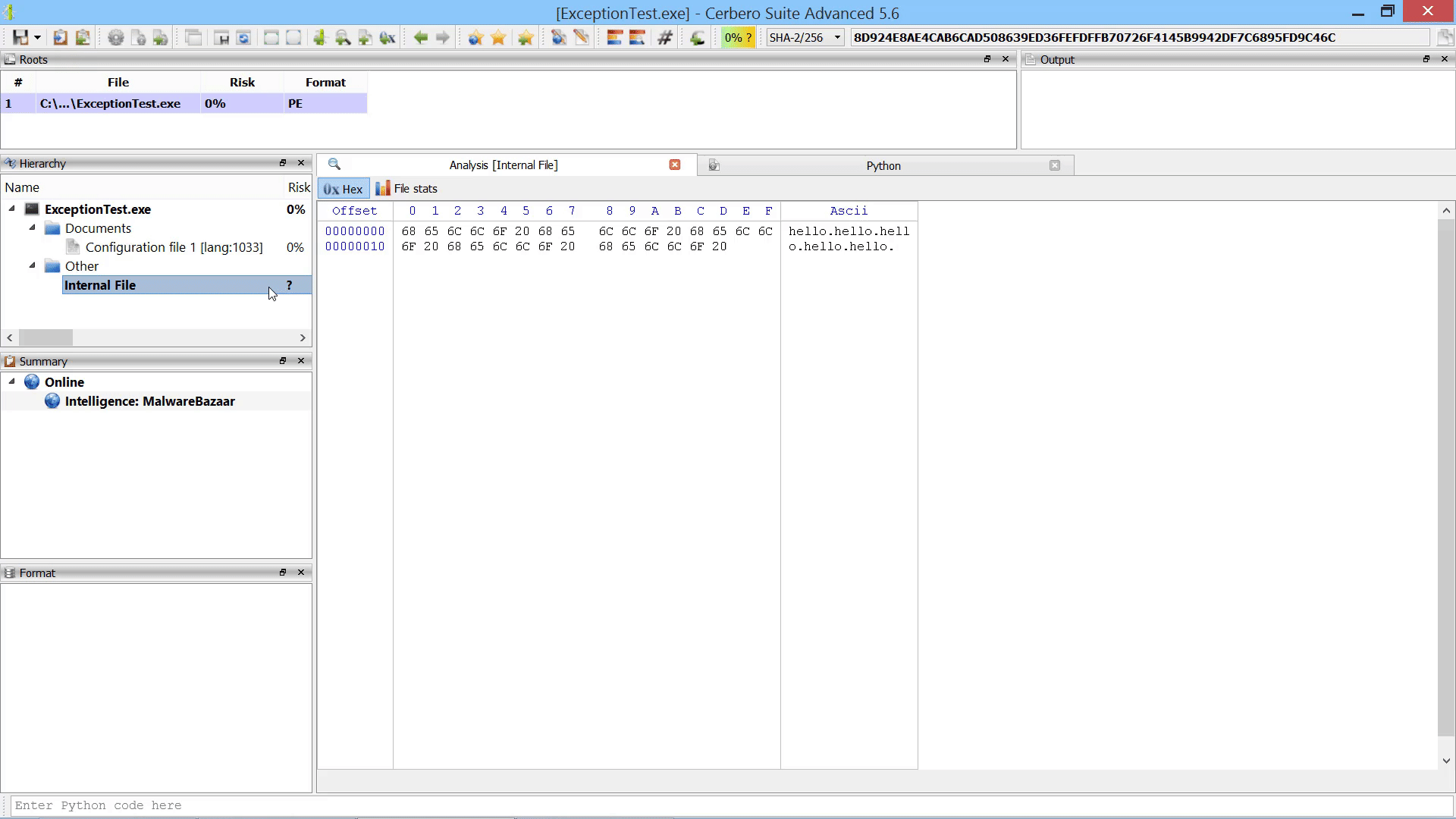
While the user could always manually load embedded objects after scanning, it is now possible to load embedded objects programmatically after scanning.
In the code example we use the recently introduced internal files to demonstrate how to add an embedded object referencing an internal file.
from Pro.Core import *
def main():
sp = proCoreContext().currentScanProvider()
r = sp.getGlobalReport()
uid = r.newInternalFileUID()
path = r.newInternalFilePath(uid)
with open(path, "w") as f:
f.write("hello " * 5)
r.saveInternalFile(uid, "Test File")
sp.addInternalFile(uid, "", "Internal File")
main()
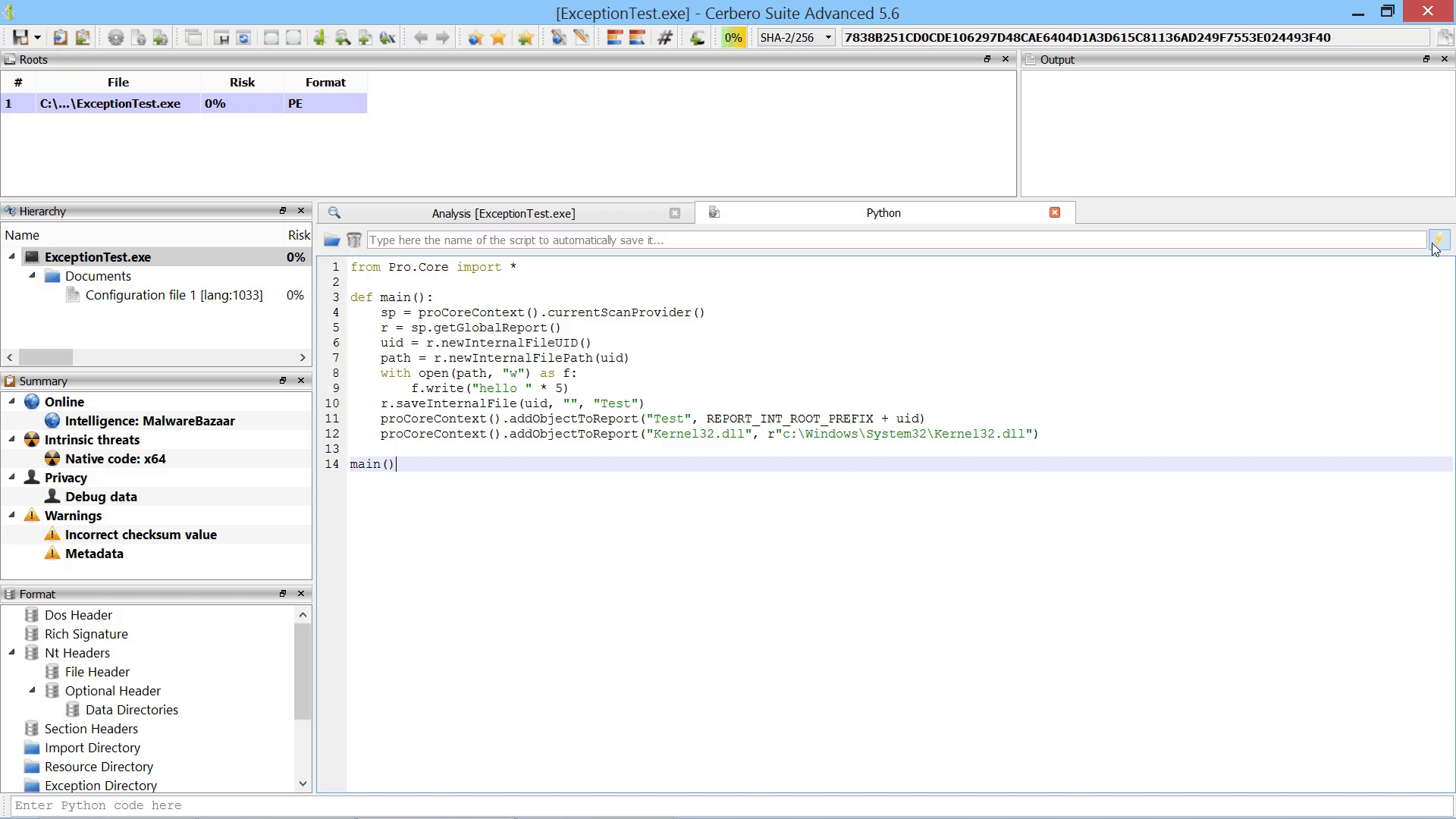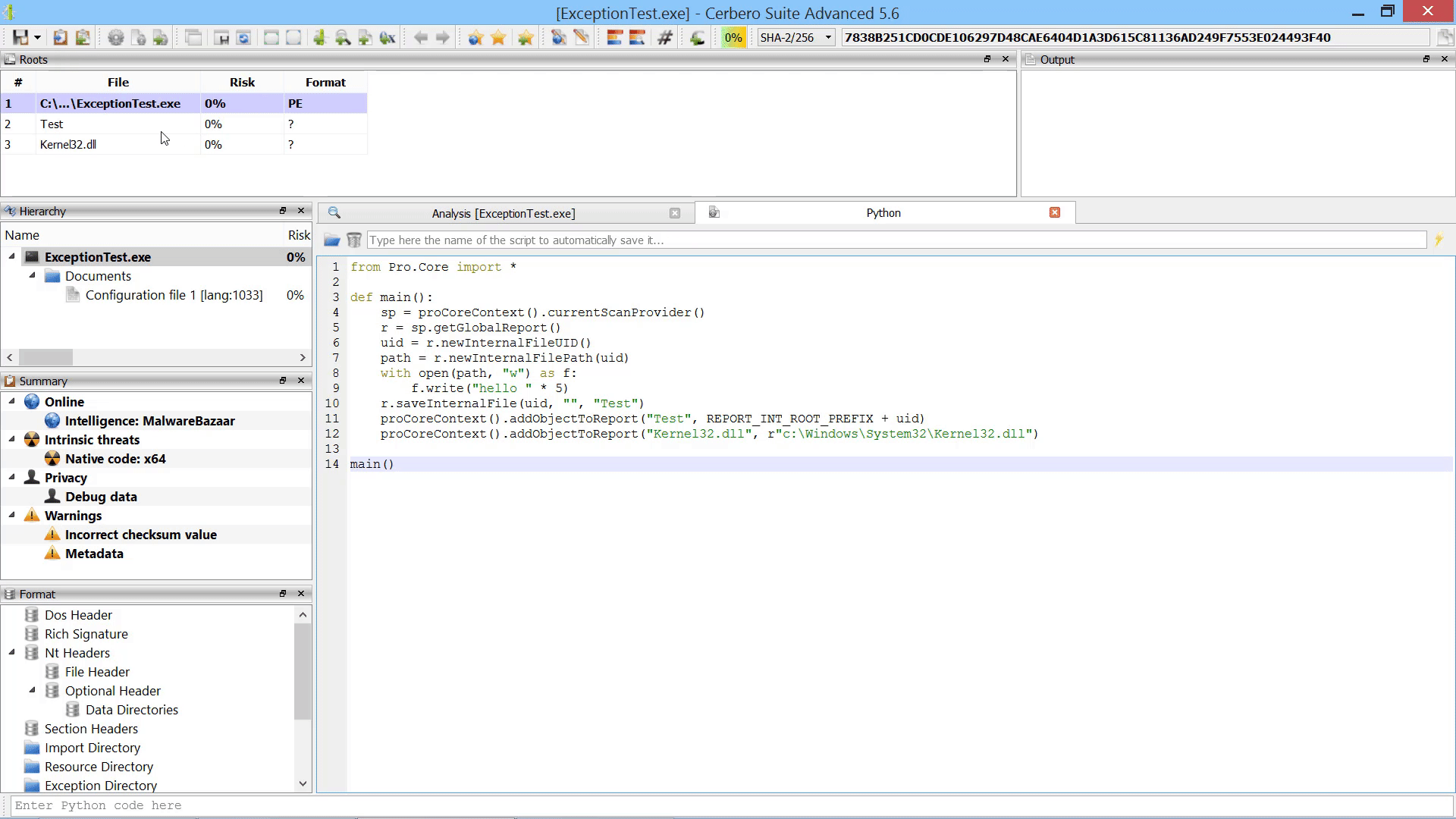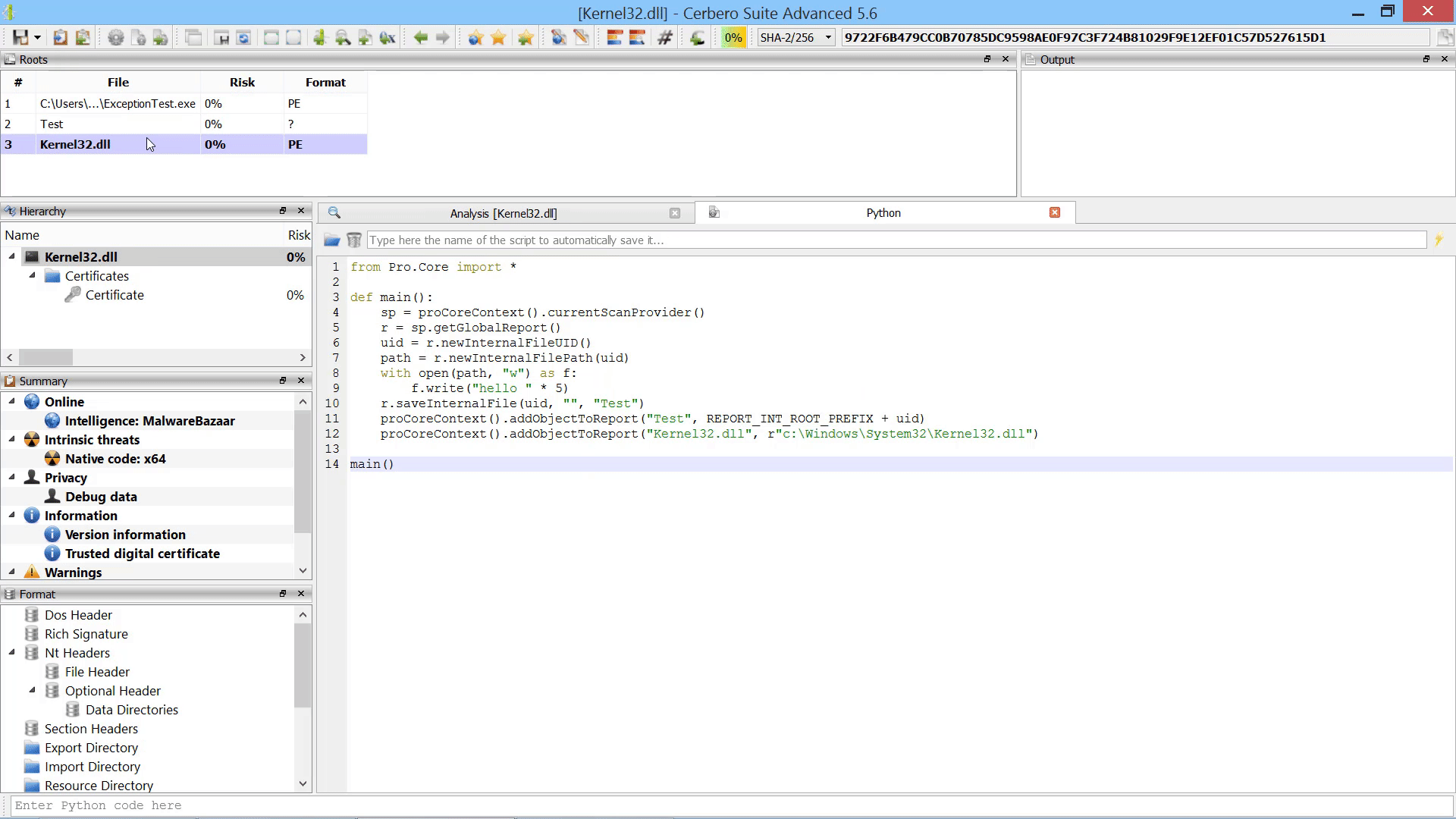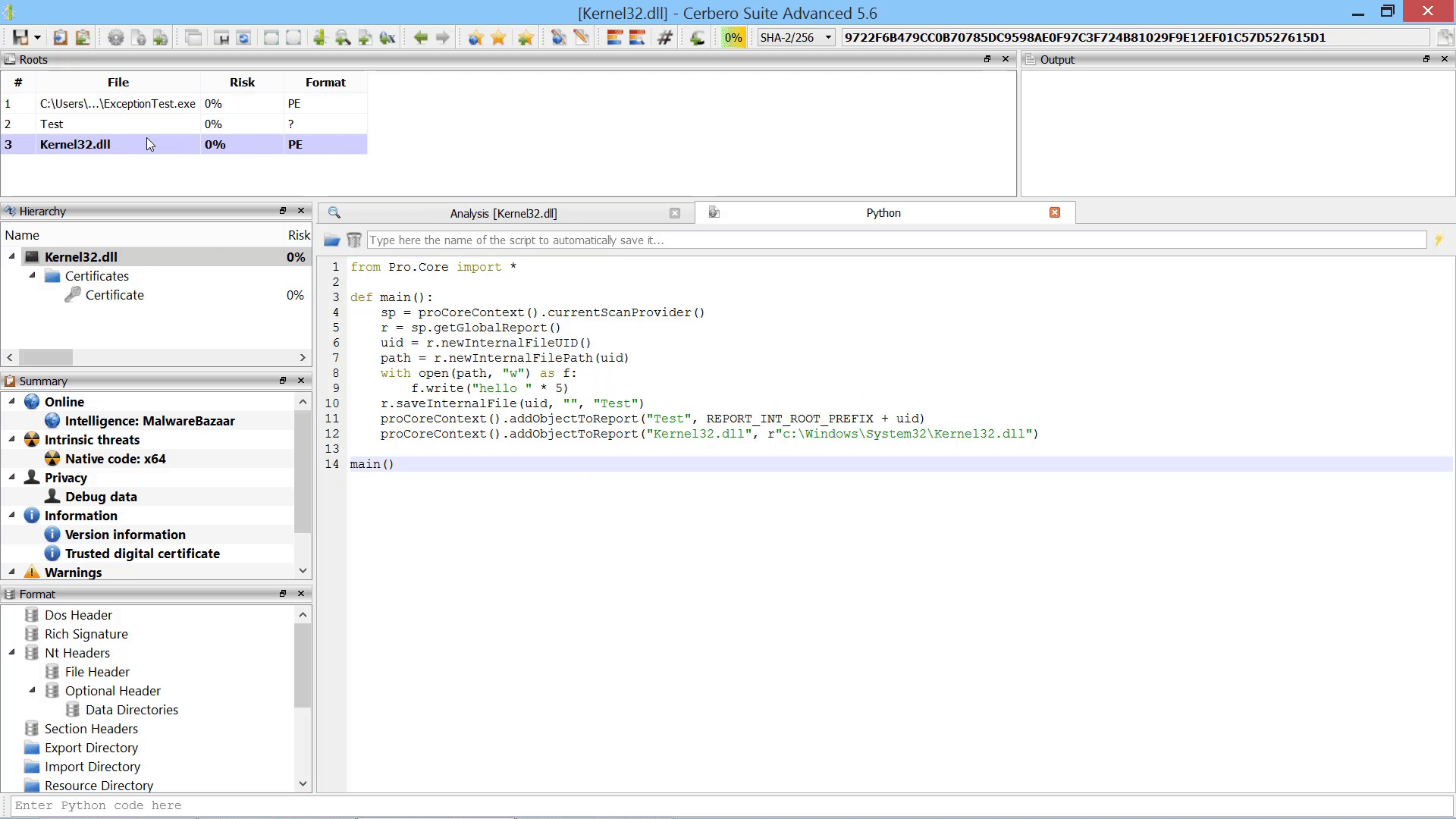
Furthermore, we added the capability to add new root entries to a report by letting the user choose files from disk. This can also be performed programmatically.
In the code example we demonstrate how to add both an internal file as root entry and a regular file on disk.
from Pro.Core import *
def main():
sp = proCoreContext().currentScanProvider()
r = sp.getGlobalReport()
uid = r.newInternalFileUID()
path = r.newInternalFilePath(uid)
with open(path, "w") as f:
f.write("hello " * 5)
r.saveInternalFile(uid, "", "Test")
proCoreContext().addObjectToReport("Test", REPORT_INT_ROOT_PREFIX + uid)
proCoreContext().addObjectToReport("Kernel32.dll", r"c:\Windows\System32\Kernel32.dll")
main()
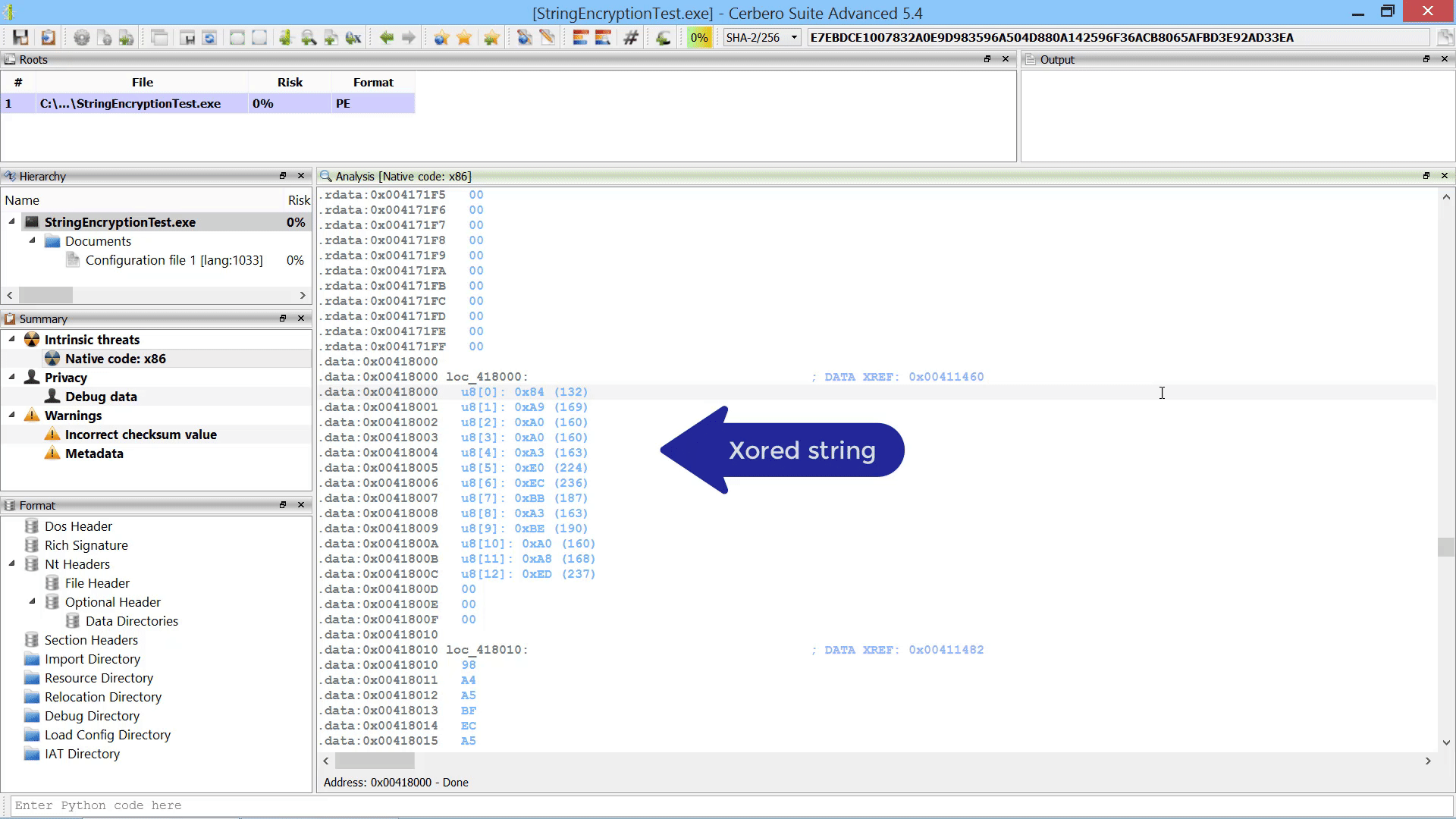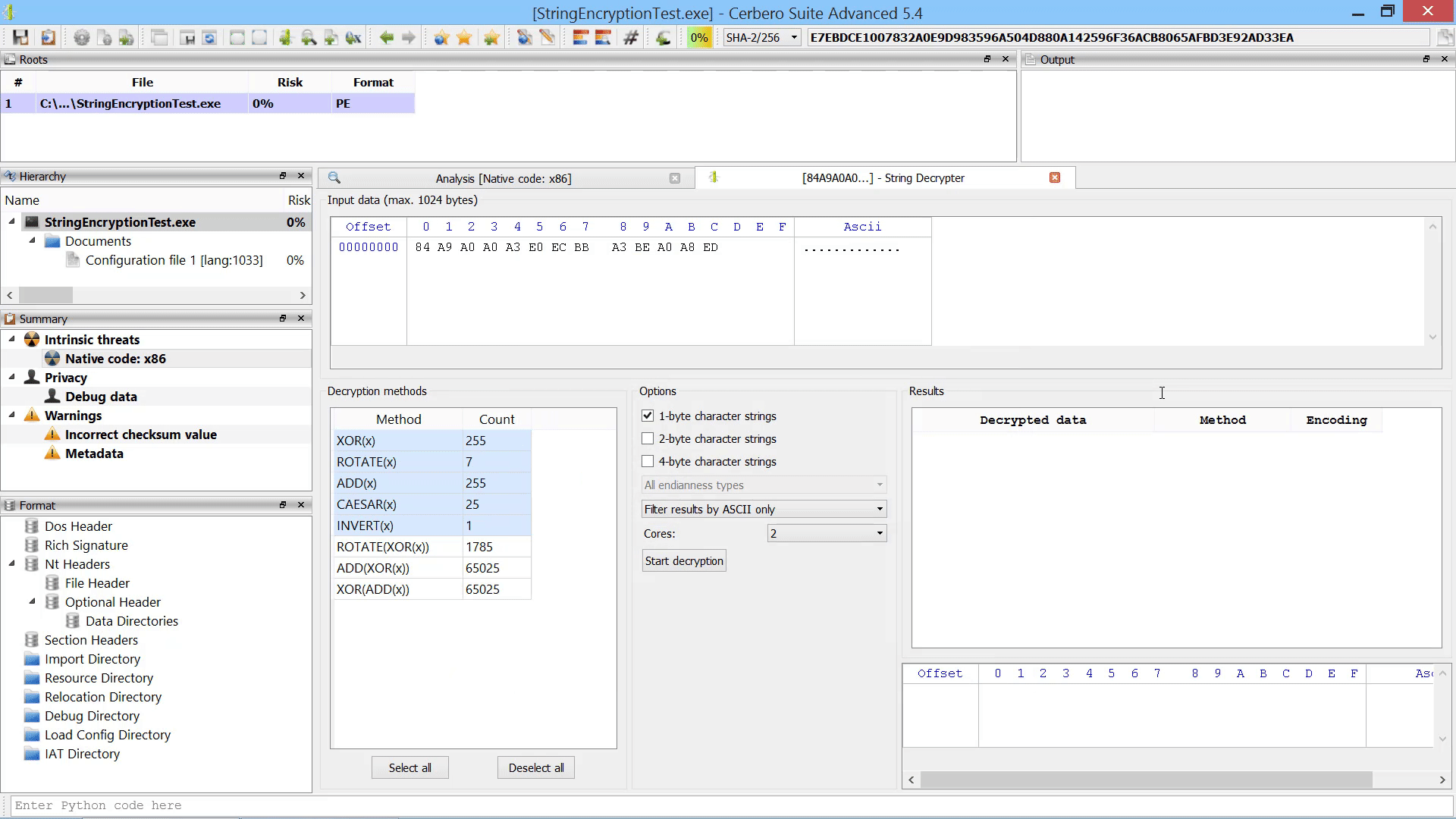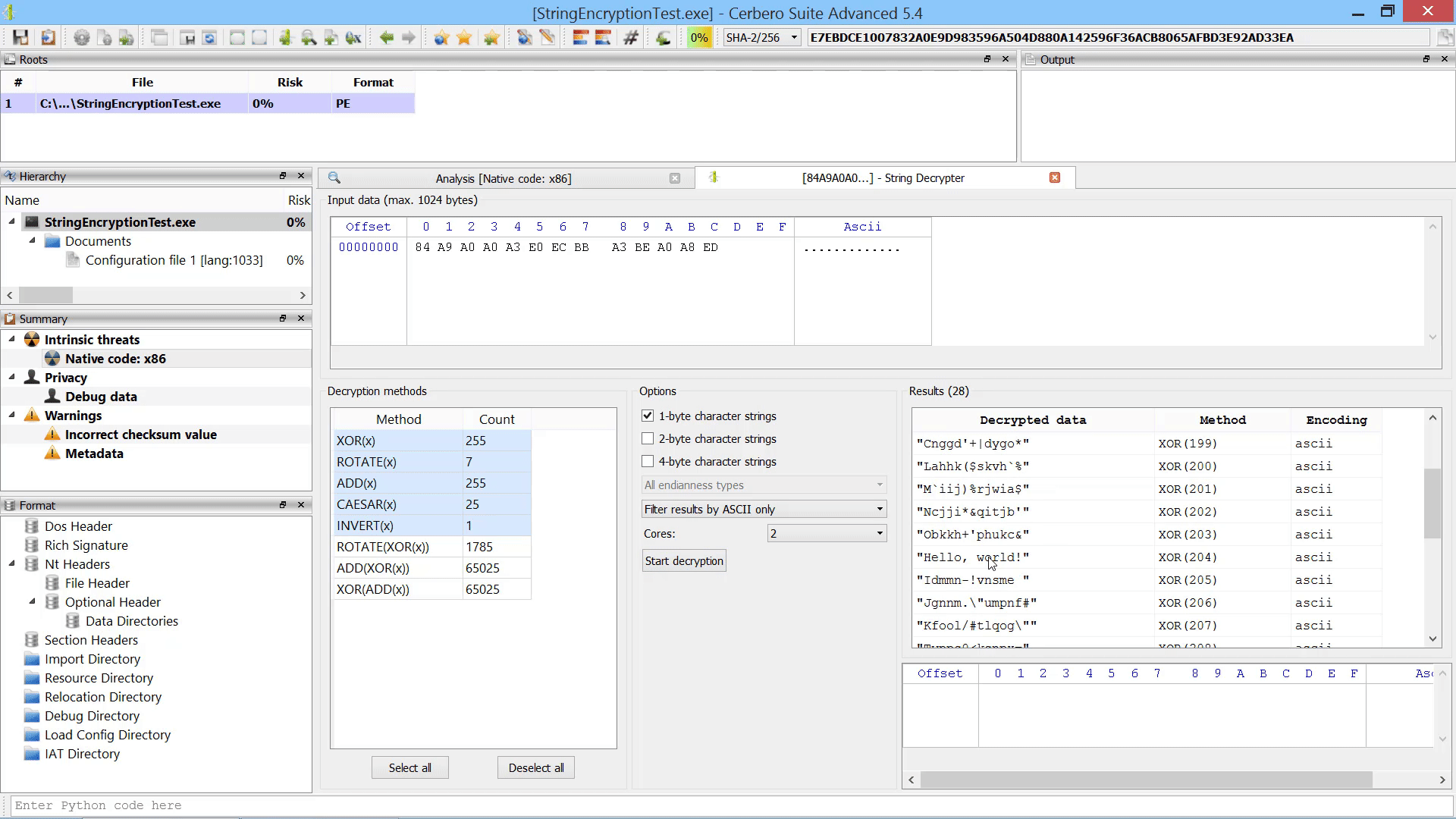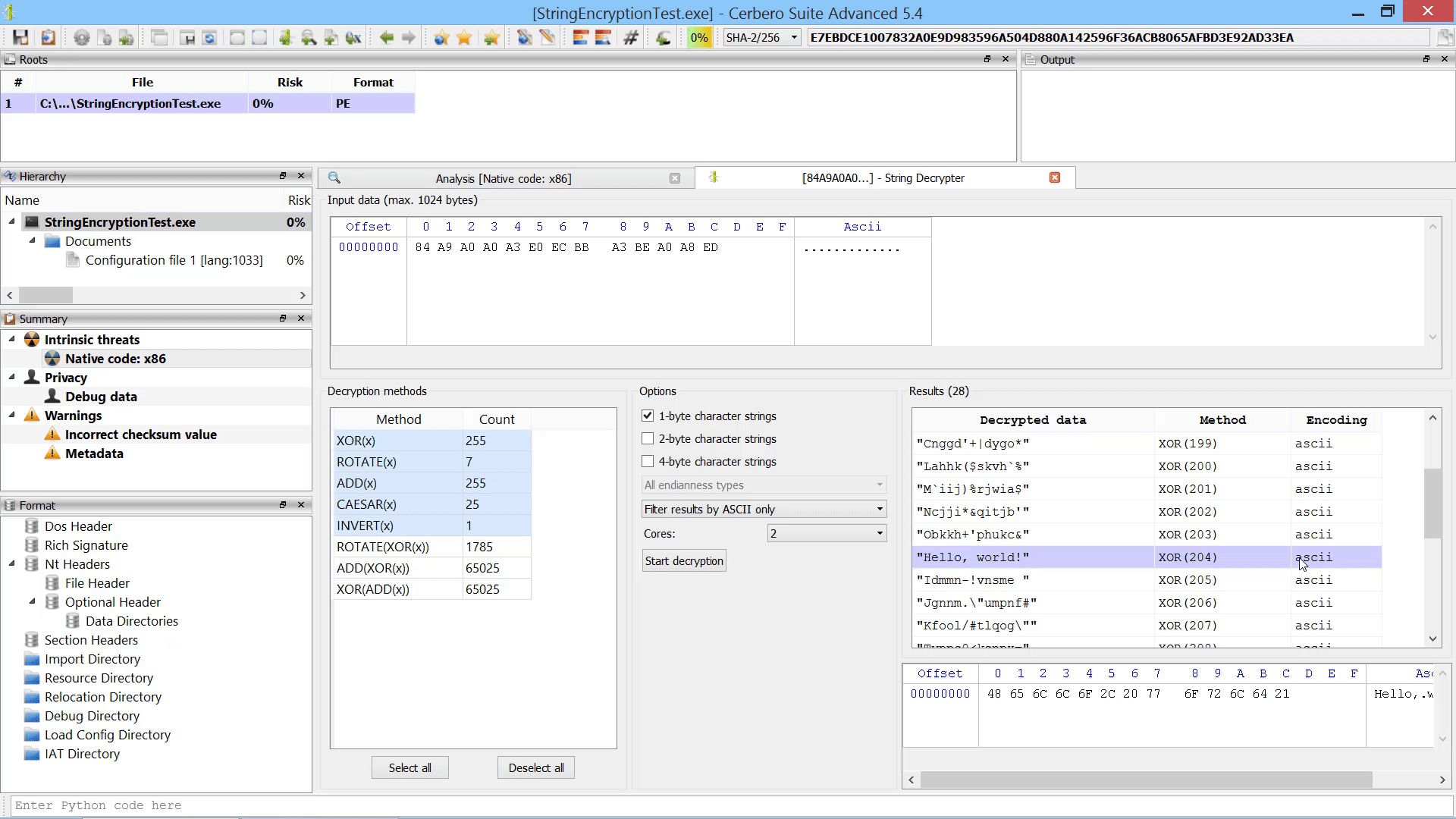
Last but not least, we added the capability to promote the data in a hex view to a root file in the report.
The data from the hex view is stored as an internal file and referenced from the root entry. The advantage over loading an embedded object from a hex view is that promoting the data to a root file isn’t limited to analysis hex views. In fact, this action can be performed from any hex view.